Principle of Least Privilege: What It Is & How to Implement It
What is the principle of least Privilege?
The principle of least privilege (PoLP) is a foundational security concept where a user, application, or system is given only the minimum levels of access necessary to perform required tasks, and nothing more. It is one of the core components of Zero Trust Network Access (ZTNA) and a foundational practice in cybersecurity.
Cloud-native environments are often faced with a steadily increasing user base and sporadic fluctuations of ephemeral resources. The enforcement of the principle of least privilege is not only good practice, but necessary to maintain a constant and effective security posture. This requires a thoughtful, pre-planned environment setup where security and compliance can live alongside adequate employee productivity and user access.
An environment where principle of least privilege is neglected can produce scope creep or privilege creep, the incremental broadening of access beyond what is actually needed, resulting in a less secure environment and unmaintainable user and system resource base. Hackers can take advantage of elevated privileges to gain a foothold and pivot into a system, gaining access to other systems resulting in any number of data breaches we’ve seen in the past. By limiting access, the potential damage of a hack is greatly reduced from both ransomware, hackers and insider threats. PoLP is a strong foundation for a zero trust security model.
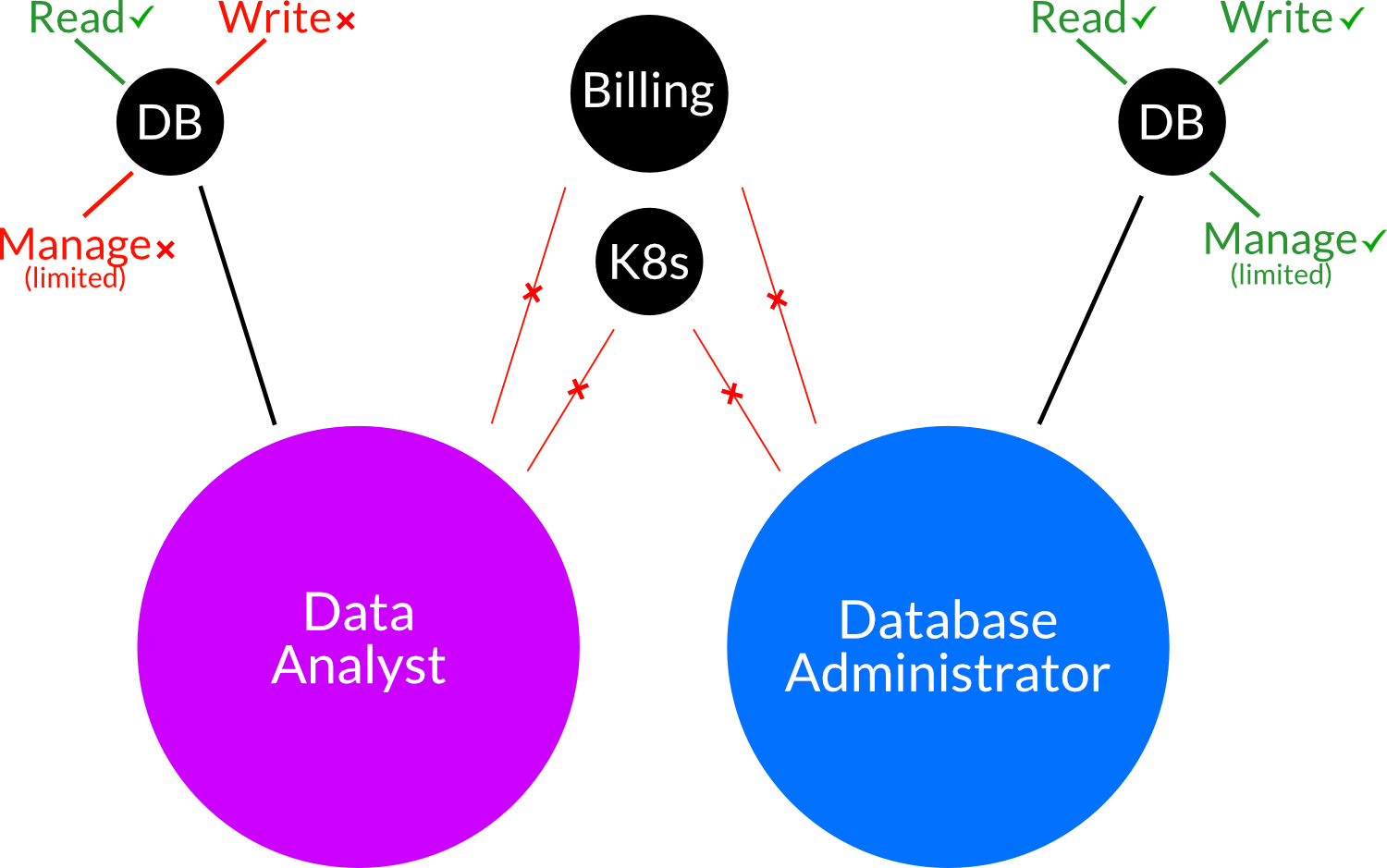
In the above diagram, we have two users, a Data Analyst and a Database Administrator. The Data Analyst only needs to read data from a database, thus read-only access is granted. On the other hand, the database administrator needs to also write and manage the database in some way (though this should still be limited). However, neither need any access to Kubernetes clusters or billing information. They are both given a baseline access of what they need to perform their daily duties and nothing more.
Who and what does least privilege apply to?
When we think of the principle of least privilege, and really privilege in general, we think especially of users and what they are authorized to carry out. For example, an administrator will have a higher privilege than a third-party contractor, allowing them to perform more sensitive operations.
But the principle of least privilege applies not only to users, but also to machines. For example, in Zero Trust environments machines also have an identity and are assigned privileges authorizing them to perform certain operations. A CI/CD pipeline should be authorized to perform, say, updates on a server and access to a code repository, but should not also be authorized to create users and assign privileges.
Whether it's a user account, a system, or a server, care should be taken to assess what permissions are needed to perform the duties, and nothing more.
What are the benefits and best practices of least privilege?
Benefits
So we’ve shared so far that the principle of least privilege is important in creating and maintaining secure environments and the systems within it. But let me get specific and list out some of the more explicit benefits:
Reduces attack surface: If a user or machine is compromised or a company is facing a cyberattack, the enforcement of PoLP will limit the attacker from broad access. This is why care should be taken to limit or even get rid of administrative accounts, or superuser access altogether (via temporary, privileged access requests).
Reduces spread of malware: With fewer users having broad, administrative privileges, any introduction of malware or vulnerabilities to the environment can be better contained and restricted to the actions of that user or machine’s permissions.
Reduces human error: All humans are prone to mistakes. With PoLP in place, those inevitable mistakes can be contained and kept isolated from critical systems, processes and sensitive data, and can limit any broad ramifications.
Keeps you prepared for any audits: Having an up-to-date PoLP policy in place can reduce the effort and scope of regular audits. In addition, many compliance standards (HIPAA, GDPR,, PCI DSS, and SOX) will require that a form of PoLP be in place.
Ease of operational management: Managing privileges over a large database of users and systems can be quite complex. PoLP can produce better productivity, as a result of clear definitions, stability and manageability as operations move up and to the right.
Best practices
Now let’s take a look at best practices when it comes to the principle of least privilege:
Adopt least privilege by default: This should be a default practice in your environment and implemented at the very beginning of any project.
Disable or remove unnecessary components: A tight inventory should be kept in such a way that unnecessary or unused components be removed or disabled in a timely manner. Otherwise, these will be forgotten in security updates and can pose security risks.
Limit privileged accounts: Privileged accounts should be limited not only in number, but in access as well. Privileged accounts can often be removed completely with the addition of privileged access requests where access gets approved on a case-by-case basis, temporarily, by other members of the team.
Logs should be regularly audited: Logs should be reviewed and alerts set up to detect the use or abuse of over-privileged actions as they happen.
Clear definitions: Be sure that roles and permissions for your users and systems are clearly defined and separated in such a way where privilege doesn’t easily overlap between users of different departments or skill sets.
Secure Endpoints: Rolling out Device Trust can be a helpful method of protecting developers machines and endpoints.
What are some challenges to implementing PoLP?
The principle of least privilege also faces several challenges when implemented. Here are a few:
User frustration: While management can benefit from better control over the environment and processes within, employees who are used to having an abundance of access may find the limits frustrating and even an impediment to their workflow, productivity and satisfaction. Teams should look for systems that provide just-in-time access.
Operating system capability: PoLP isn’t a concept that every operating system makes easy to implement. With different configurations, and handling of roles and privileges, finding a unified methodology across various operating systems can pose a challenge.
Ephemeral cloud environments: Also, while the principle of least privilege can be an asset to security in an ever-changing cloud environment, it can also be a challenge to apply effectively in ephemeral cloud environments due to the changing nature of the resources and users within it.
Scaling: And as users and processes increase, especially in multi-cloud environments, and defined privileges become more fluid and lenient, admins or management can have a harder time enforcing these boundaries effectively. Regular audits and adjustments should be made to keep this in order.
How to implement principle of least privilege
It’s easier to implement the principle of least privilege at the outset of a new project where users and machines are first being created and onboarded.
If you are at this stage, make use of role-based access controls (RBAC) instead of assigning privileges based on individual user needs. Design these roles to be with the least privilege possible and be sure to perform regular audits to keep on top of scope creep. And consider just-in-time access requests, to temporarily elevate privilege, over granting administrative access to users.
However, we rarely find ourselves in this ideal situation. More common is that time has passed on a project and many users and resources have gone unchecked leading to an ever-growing scope creep. In this situation, here are some steps to take to get realigned with the least privilege access.
Initiate a privilege audit: The first step is to initiate a privilege audit. You’ll need to comb through your users and resources to see how the privilege “landscape” is looking. Create a record of things like:
- Who has more privilege than needed, and how often is it being used?
- Is this use justified? How can you redistribute, update, or create roles or privileges to better meet the principle of least privilege?
- How are roles and privileges separated out? Do these need to be redefined to better fit your company’s positions and goals such that an abuse of privilege is less likely to be a necessary outcome?
Re-evaluate your separation of duties: Consider the duties of your users and services. Are they separated and defined in such a way that they can easily be given privilege for their specific duties and nothing more? For example, instead of having 4 DBAs, you could further define these based on database type or responsibility so that all four don’t share the same widespread database privileges, much of which they may not need.
Establish least privilege as a default moving forward: Now that you’ve performed an audit and made appropriate changes, set up a plan to keep the principle of least privilege at the forefront of security moving forward.
Monitor and analyze privilege access: Put a system of monitoring in place so that least privilege can be better maintained going forward. Set alerts to help you keep privilege abuse in check.
Provide just-in-time, granular access with a tool like Teleport: Just-in-time access allows users and machines to temporarily request privilege elevation on an as-needed basis. This helps companies steer away from too many admin roles or privileges (if any) needing to be assigned. Tools like Teleport combine this just-in-time access with a robust RBAC system to shrink any attack surface and keep control at a very granular level.
Regularly review privileges and privilege rulesets: Finally, schedule time quarterly or bi-annually to review privileges and privilege rulesets to keep privileges tidy and attack surfaces low.
How does Teleport implement and improve upon PoLP?
Teleport helps organizations adopt PoLP quickly in the cloud by way of being a secure, centralized, role-based platform for all your infrastructure, applications and systems.
Centralized access: Centralized access for all your systems sets the stage for a manageable and secure principle of least privilege workflow. With all of your servers, Kubernetes clusters, applications, databases and Windows machines being securely managed in a central location, you can better define and maintain roles within a bigger picture.
Role-based access control: Access and privilege should not be assigned based on individual user needs. Instead, roles should be thoughtfully created around responsibilities of your users and machines. Teleport comes with role-based access control built in, governing who has access to what and what level of access is given. By centralizing access policies, teams can easily view and audit levels of access.
On-demand privileged access requests: Teleport’s Just-in-Time Access Requests allow users to request access to resources or roles depending on need for a pre-approved limited window or time. Approvers can be configured to approve these requests and can do so via ChatOps tools like Slack. These access requests allow for a severe reduction, or even elimination, of admin, superuser roles, better known as zero-standing privilege.
Frequently Asked Questions
How does the principle of least privilege differ from separation of duties?
Separation of duties is splitting up the privileges or responsibilities of your users so that no one user has all the privileges needed to execute critical business functions. This reduces the chance of misconduct by one over-privileged user. Principle of least privilege has more to do with seeing that all users only have the privileges necessary to perform their specific tasks at hand.
Does PoLP also apply to non-humans?
Yes. Servers, CI/CD pipelines, internal processes, applications, etc. all are granted privileges to perform certain tasks. You want to make sure that each of these are evaluated as to what actions they ‘need’ to perform and be scoped accordingly. Instead of using static privileged credentials, teams should look at deploying short-lived certificates for access. Teleport Machine ID is a good open-source option for teams looking to secure machine accounts.
How often should access rights be reviewed?
While this depends on the particular organization, we all can agree that it should be done regularly, especially after a security incident or on personnel changes.
Should every user have a different level of access in PoLP?
No. Most PoLP integrations include the use of role-based access controls or a similar setup where similar users can share a limited set of permissions based on particular job functions.
How does PoLP relate to zero trust?
PoLP is complementary to zero trust ensuring that even in a zero-trust environment, where nothing and no one is trusted, users and machines only have the access they absolutely need. It’s an added security measure to zero trust.
What tools can help enforce PoLP?
Identity and access management (IAM) solutions, role-based access control (RBAC) systems, and privileged access management (PAM) tools like Teleport can help organizations enforce this principle.
