Teleport Blog
Subscribe to the RSS FeedFeatured Post

Teleport 16
Learn about the latest advancements in Teleport 16, our major release packed with new features, bug fixes, and improvements. This release focuses on defending against IdP compromise, improved usability for teams, and a few significant breaking changes, including a new commercial license for Teleport Community Edition. Explore enhanced security with phishing-resistant MFA, Teleport VNet, and more.
Teleport
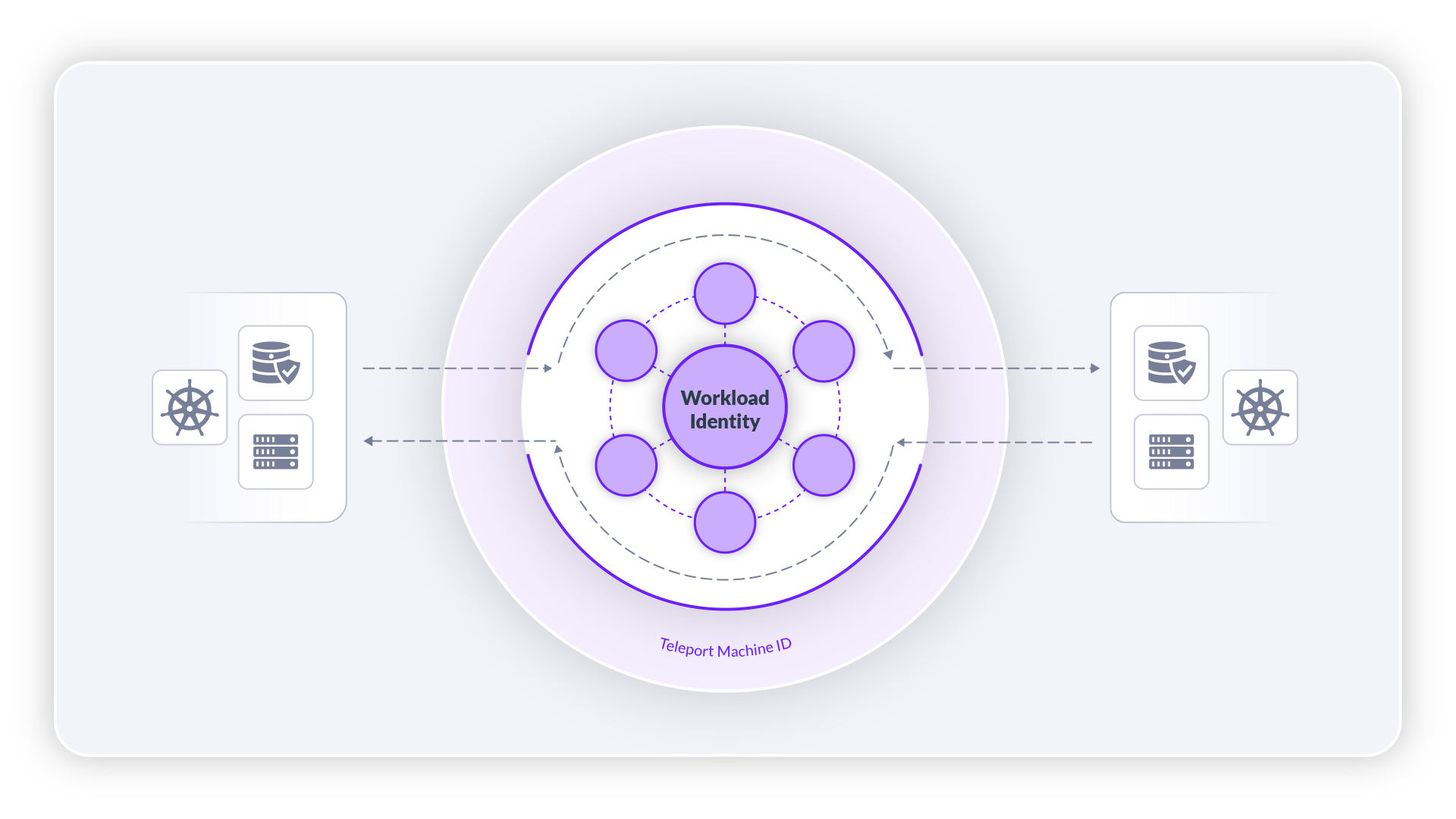
Teleport Workload Identity
An introduction to the preview feature Teleport Workload Identity. A feature that lets teams bootstrap and issue identities to services across heterogeneous environments and organizational boundaries.
Oss
Teleport Community Edition will restrict commercial usage starting with version 16
A detailed explanation, schedule, and FAQ on why we have switched Teleport Community Edition to a commercial software license.
Company
2024 Predictions from Teleport CEO Ev Kontsevoy
The blog forecasts cybersecurity shifts in 2024, emphasizing secretless access, role changes in security teams, M&A consolidation, and regulatory pressures. It advocates for least privilege access and secret removal to strengthen security.
Articles by topic
- All
- AWS
- RBAC
- access-requests
- announcements
- applications
- audit
- bastion
- certificates
- company
- compliance
- cybersecurity
- databases
- device-trust
- engineering
- featured
- governance
- gravity
- kubecon
- kubernetes
- machine-id
- mongodb
- newsletter
- okta
- oss
- pam
- passwordless
- postgres
- programming
- saml
- security
- snowflake
- ssh
- sso
- teleport
- teleport-platform-security
- terraform
- vpn
- webauthn
- windows
- z3
- zero-trust
Blog Posts

Subscribe to our newsletter