THE AI INFRASTRUCTURE IDENTITY COMPANY
Unified Identity Securing Classic & AI Infrastructure
Faster engineering. Resilient infrastructure.
Teleport unifies identities — humans, machines, and AI — with strong identity implementation to speed up engineering, improve resiliency against identity-based attacks, and secure AI in production infrastructure.
TRUSTED BY GLOBAL LEADERS




















How Do You Teleport?
Remove identity and access friction while making infrastructure more resilient.
Everyone wins.
Secure AI infrastructure in data centers
Gain visibility, unify access control, and secure identities for agents, LLMs, and MCP tools across your AI infrastructure.
Accelerate engineering
Eliminate secrets and VPN complexity, and cut time needed for audits, on/off-boarding, forensic investigations, automation and more.
Vault-free privileged access (PAM)
Protect infrastructure with zero trust and zero standing privileges (just-in-time access) that technical teams and auditors love.
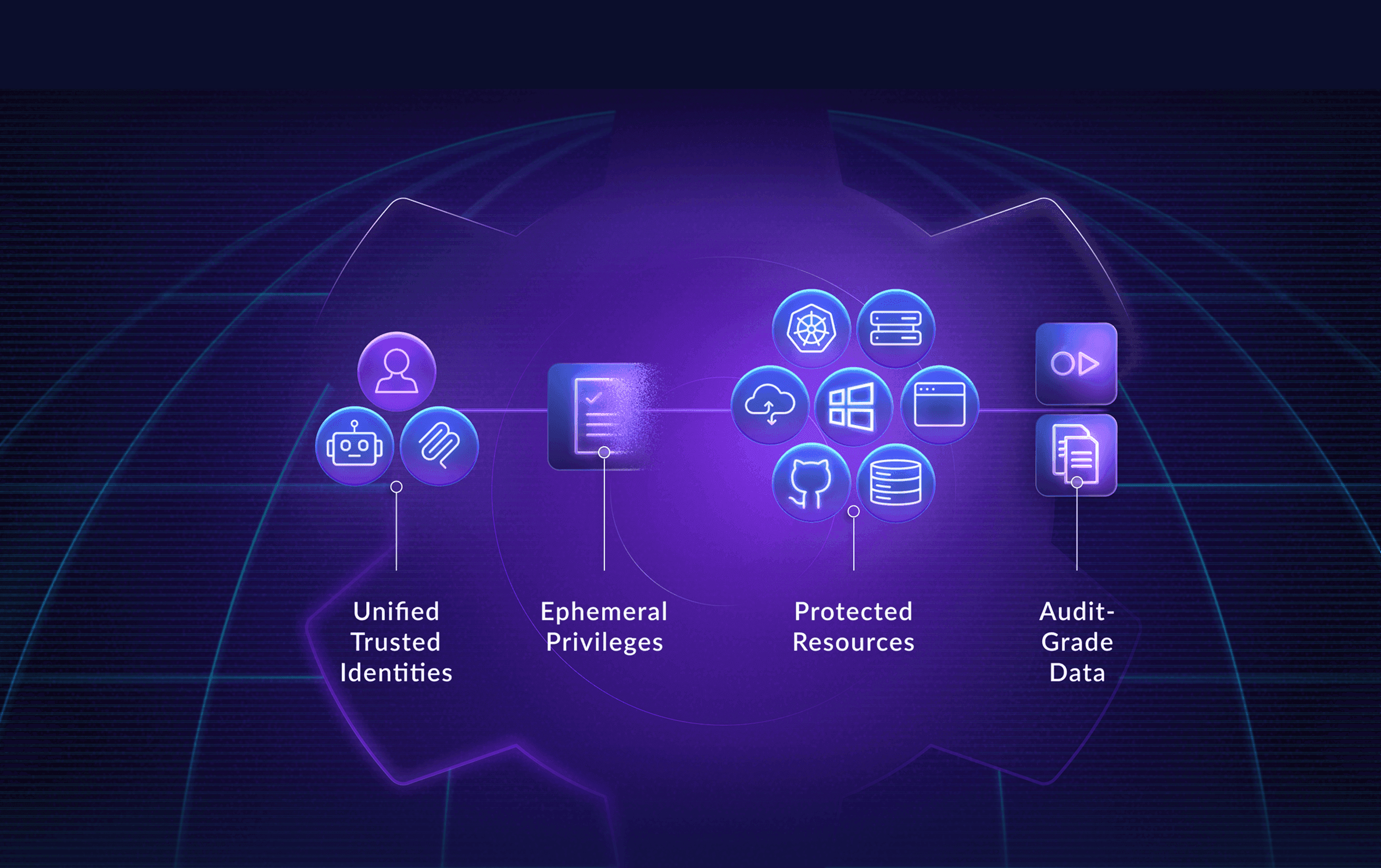
Ditch complexity and create trusted environments for customers, 3rd party, and engineers.
Achieve zero standing privileges, with just-in-time controls for humans, machines, and AI.
Instant access through web/CLI with interactive session controls and audit-grade reporting.
Flag real-time anomalies as identities move across identity providers, code & infrastructure.
The Fastest Way to Implement
Guardrails for AI Infrastructure in Your Datacenters
How do we know? We secure the infrastructure of the largest AI companies in the world.

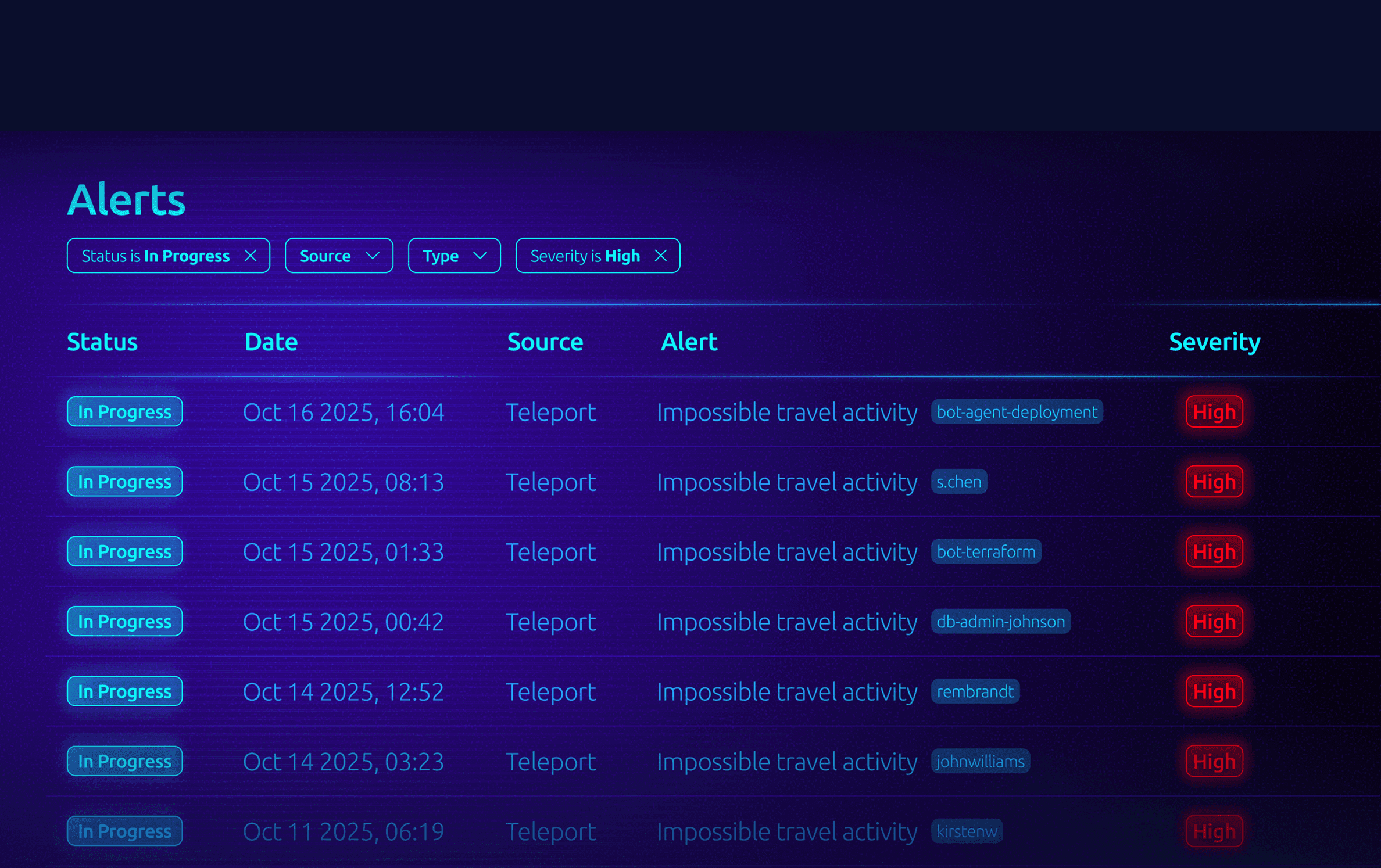
Security that Delights Engineers
Stop thinking that to move fast, you need to bypass security. Instead, expect security to accelerate engineers and improve your business velocity.
Customers have used Teleport to:
Cut audit toil
by 80%

Reduce policy violations
to zero

Reduce on/off-boarding
from days to minutes

Reduce forensic investigation
from weeks to minutes

Eliminate credentials
handling toil

Make automation fun
(their words, not ours)

An Active Open Source Community
Enterprise-Grade Features, Deployed Your Way
Teleport adapts to your environment to keep infrastructure secure, compliant,
and supporting your business velocity objectives.
Deployment flexibility | Run Teleport on-premises, in any public or private cloud, or self-host for maximum control. |
High performance | Fast, low latency access around the world without VPNs, bastions, or jump hosts. |
Premium high availability | Up to 99.99% high availability with global multi-region failover across nine availability zones. |
Built for regulated environments | Supports air-gapped, highly regulated, and legacy infrastructure. Certified for SOC2, GDPR, and HIPAA. |
Teleport has made obtaining a FedRAMP-Moderate ATO that much more achievable via their FIPS 140-2 endpoints, ease in integration with our SSO and MFA , and the view into audit logs of remote connection sessions provide the appropriate insight for Continuous Monitoring.
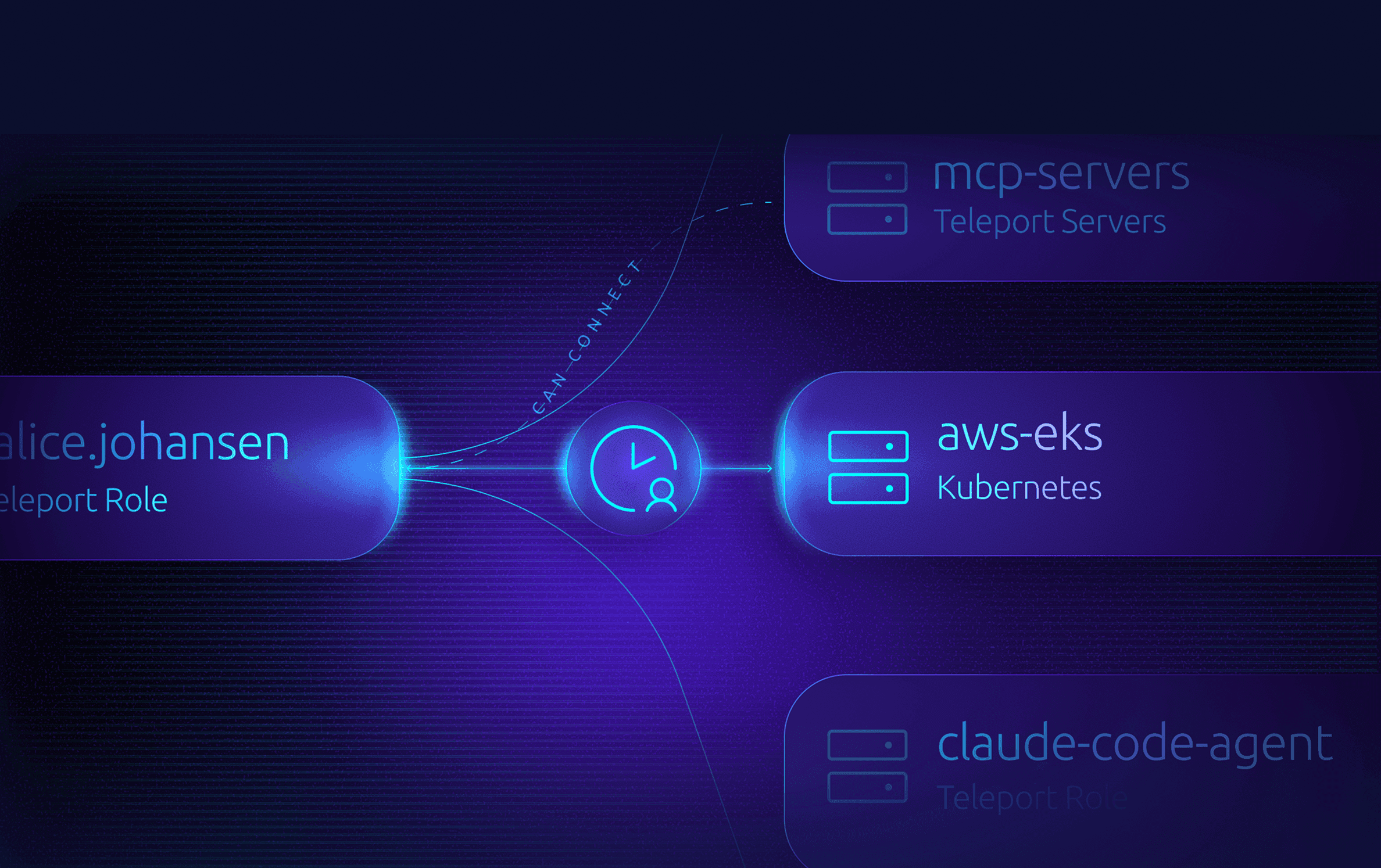
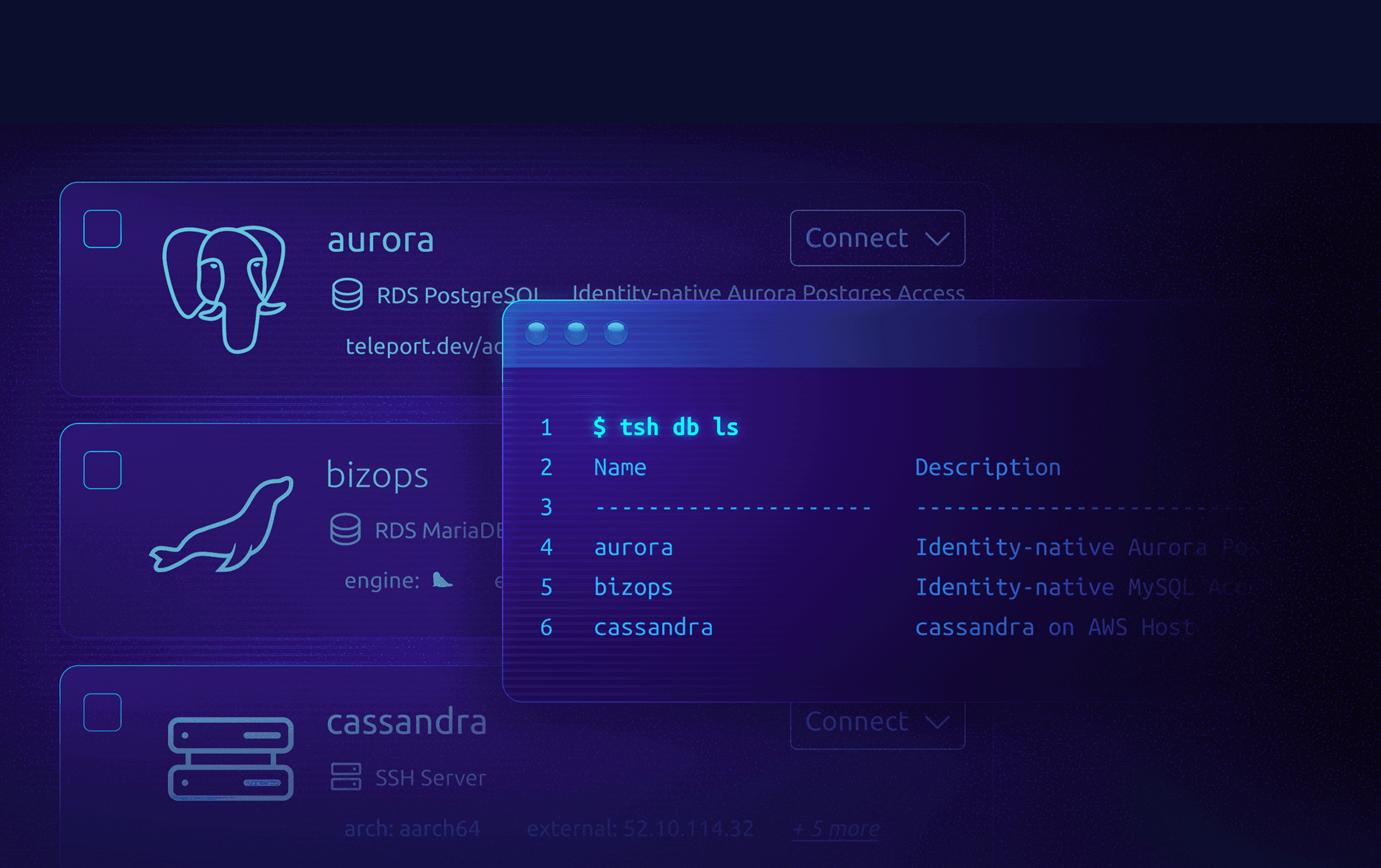
For All Identities:
Human, Machine, Workload, AI Agent, Endpoint
With deep integration to Cloud Consoles, Windows RDP, Kubernetes, GitHub, Servers, Databases, MCP Servers
Teleport Infrastructure Identity Platform
Simplify your identity stack. Secure with confidence.
Control, manage, and investigate all identities and infrastructure from one unified platform.
Zero Trust
Access
Eliminate credentials &
adopt least privileged access
Machine & Workload
Identity
Secure and govern
inter-machine interactions
Identity
Governance
Harden & govern
identities
Identity
Security
Expose and eliminate
hidden risk
What Our Customers Say
Teleport allows us to comply with the regulatory hurdles that come with running an international stock exchange. The use of bastion hosts, integration with our identity service and auditing capabilities give us a compliant way to access our internal infrastructure.
Speed is key to our business. But so is security. The Teleport Access Platform allows our engineers to securely access the infrastructure they need to do their jobs without getting in the way of productivity. Everybody wins.
Teleport has made obtaining a FedRAMP-Moderate ATO that much more achievable via their FIPS 140-2 endpoints, ease in integration with our SSO and MFA , and the view into audit logs of remote connection sessions provide the appropriate insight for Continuous Monitoring.
The Infrastructure Identity solution from Teleport offers a glimpse into the future of more secure, more resilient, and higher-velocity enterprise computing.
We use Teleport Access Requests in combination with Auth0 to easily manage access to our infrastructure. Prior to Teleport, we manually managed SSH keys and a bastion machine and it was an organizational nightmare.
Teleport allows us to comply with the regulatory hurdles that come with running an international stock exchange. The use of bastion hosts, integration with our identity service and auditing capabilities give us a compliant way to access our internal infrastructure.
Speed is key to our business. But so is security. The Teleport Access Platform allows our engineers to securely access the infrastructure they need to do their jobs without getting in the way of productivity. Everybody wins.
Teleport has made obtaining a FedRAMP-Moderate ATO that much more achievable via their FIPS 140-2 endpoints, ease in integration with our SSO and MFA , and the view into audit logs of remote connection sessions provide the appropriate insight for Continuous Monitoring.
The Infrastructure Identity solution from Teleport offers a glimpse into the future of more secure, more resilient, and higher-velocity enterprise computing.
We use Teleport Access Requests in combination with Auth0 to easily manage access to our infrastructure. Prior to Teleport, we manually managed SSH keys and a bastion machine and it was an organizational nightmare.
Teleport’s vision for Infrastructure Identity is a game-changer for securing hybrid infrastructure.
SSO and RBAC support, in combination with Teleport’s unified access control, made secure infrastructure access for humans easy. Machine identity is helping us secure automation. Teleport is simply one of the best privileged access solutions for engineering environments out there.
We used to go through multiple steps just to access cloud resources, and now it happens almost instantly. Our engineers are really happy with the significant improvement in their workflow.
Over the many years of using Teleport, it's been an essential piece of my infrastructure to help secure access, and centralize my infrastructure into one dashboard, without having to jump around… I'm not sure how I could go without it.
Teleport’s vision for Infrastructure Identity is a game-changer for securing hybrid infrastructure.
SSO and RBAC support, in combination with Teleport’s unified access control, made secure infrastructure access for humans easy. Machine identity is helping us secure automation. Teleport is simply one of the best privileged access solutions for engineering environments out there.
We used to go through multiple steps just to access cloud resources, and now it happens almost instantly. Our engineers are really happy with the significant improvement in their workflow.
Over the many years of using Teleport, it's been an essential piece of my infrastructure to help secure access, and centralize my infrastructure into one dashboard, without having to jump around… I'm not sure how I could go without it.




























































