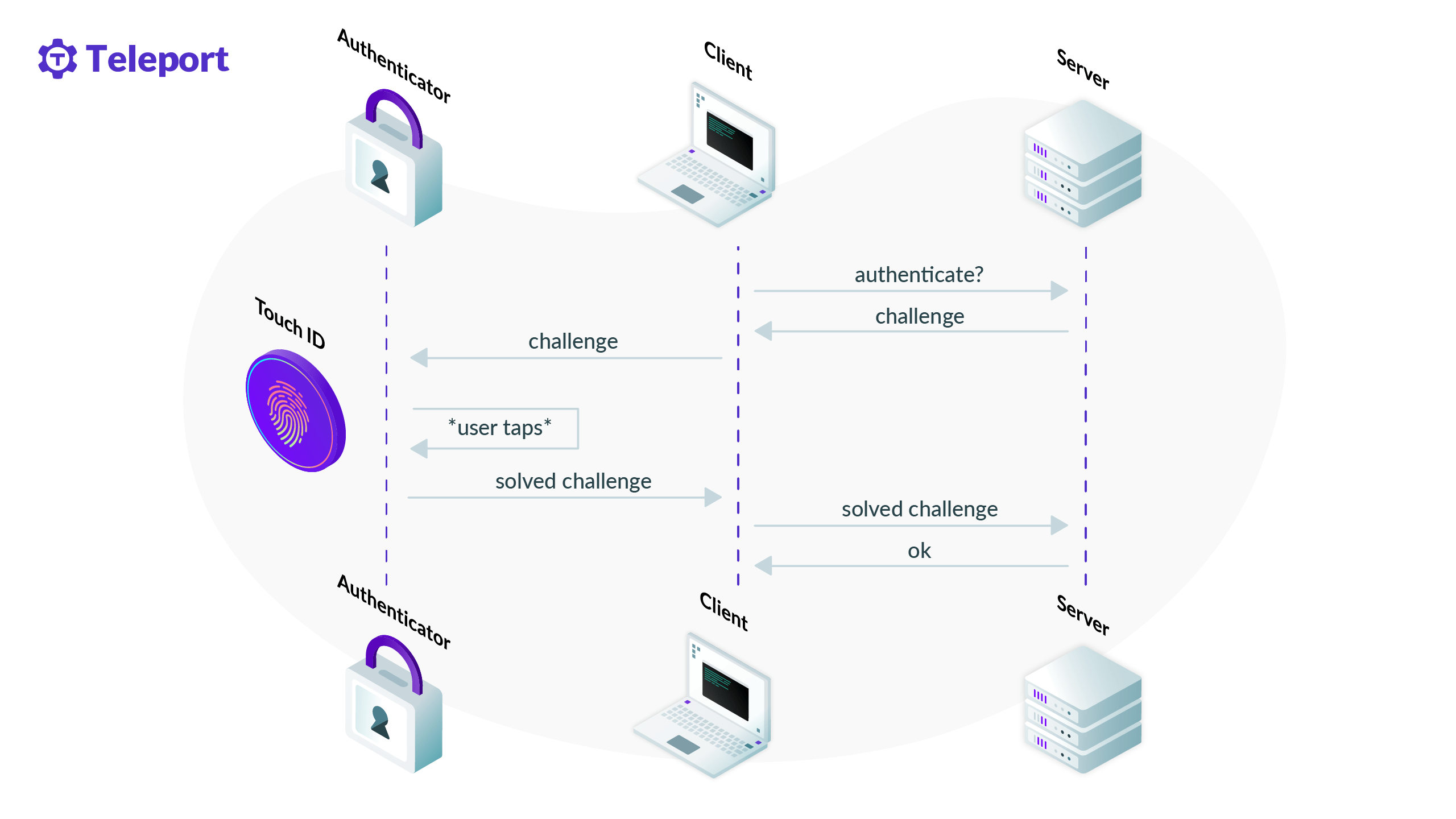
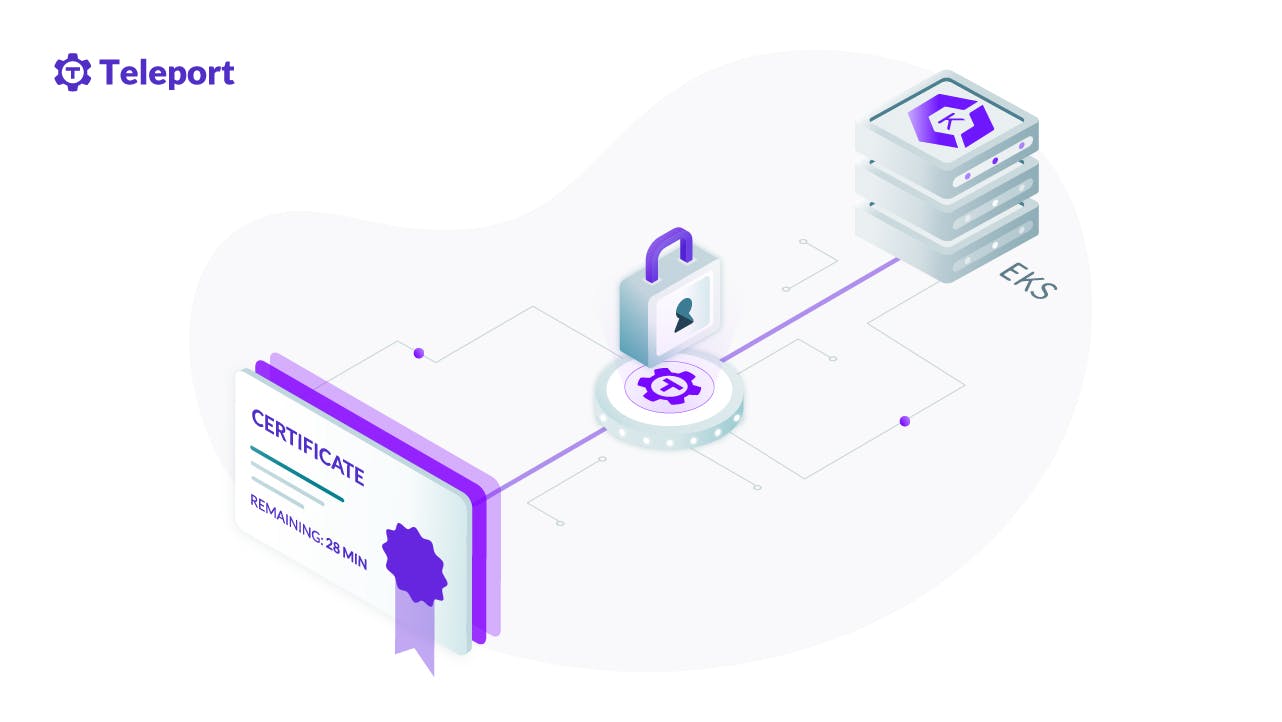
Teleport is a global provider of modern access platforms for infrastructure, improving efficiency of engineering teams, fortifying infrastructure against bad actors or error, and simplifying compliance and audit reporting. The Teleport Access Platform delivers on-demand, least privileged access to infrastructure on a foundation of cryptographic identity and zero trust, with built-in identity security and policy governance.
Global Headquarters
2100 Franklin St, Suite 400, Oakland, CA 94612
+1 (855) 818-9008