Table Of Contents
- FIDO, FIDO2, WebAuthn, CTAP, Relying Party?
- Understanding the WebAuthn registration and authentication ceremony
- Is WebAuthn used for passwordless or multi-factor authentication?
- Comparing WebAuthn with other passwordless methods
- 5 Quick wins for authentication system developers supporting WebAuthn
- Recommended resources for WebAuthn based authentication developers
- Conclusion
- WebAuthn-based passwordless access to infrastructure resources using Teleport
- Teleport cybersecurity blog posts and tech news
Home - Teleport Blog - WebAuthn Explained - Jul 7, 2022
WebAuthn Explained

The WebAuthentication API, or WebAuthn, facilitates secure authentication based on public-key credentials. The idea of passwordless and public-key authentication is not new, but the compatibility and interoperability of various elements in the authentication process were always weak. WebAuthn API aims to solve that problem by bringing the uniform authentication API into web browsers. The promise of passwordless authentication is compelling, but implementing a new authentication method to existing software applications is not a simple and quick decision one can make. One reason why password-based authentication is omnipresent is that it's easier to implement for application developers and is universally serviceable by any user.
In this post, I will explain the basic concepts and details related to WebAuthn, including its inner workings, security and operational benefits, and compare it with other popular existing passwordless authentication methods, overall providing enough info to get started with WebAuthn.
First, let's get familiar with WebAuthn terminology to clear out any confusion!
FIDO, FIDO2, WebAuthn, CTAP, Relying Party?
All the passwordless authentication hype goes to WebAuthn. But what good is an authentication API if no standardized authentication agents (authenticators) are available to users? What guarantees the interoperability between the authenticators and the WebAuthn implementers?
The FIDO2 by FIDO alliance serves as an overarching framework that has designed the WebAuthn API in coordination with W3C specification and the Client to Authenticator (CTAP) protocol that defines a generic protocol for implementing authenticators.
So technically, WebAuthn is only a core API specification of the overall authentication framework that is FIDO2. For complete support of the passwordless authentication process:
- Both the authentication system developers and users need user agents, like web browsers that support WebAuthn API.
- The authentication system developers should implement a WebAuthn API client, and
- The user should be in possession of a CTAP-compatible device like Yubikey, Apple TouchID, or Windows Hello.
Below, let's look at all the essential components and terminology associated with the FIDO2 specification in detail:
- FIDO: The FIDO alliance aims to collaborate and standardize passwordless authentication technologies. The alliance has many members, including Paypal, Lenovo, Validity Sensors, Google, Microsoft, NokNok labs, and many more. The popular Universal Authentication Framework (UAF) and Universal 2nd Factor (U2F) protocols were designed by the FIDO alliance.
- FIDO2: Latest passwordless authentication project by FIDO, which overarches the WebAuthn API and CTAP.
- WebAuthn: The API specification that defines the passwordless authentication logic between the software application and users, including cryptographic exchanges to perform public-key-based authentication.
- CTAP: The protocol that interacts with users via authenticator and communicates with WebAuthn API, transporting users' public credentials and signed challenges to fulfill authentication processes. WebAuthn uses CTAP2, and CTAP1 is defined to be backward compatible with U2F, which is the predecessor to the FIDO2.
- User agents: The software applications that implement the WebAuthn API. Web browsers are examples of user agents. In the WebAuthn specification, user agents are also referred to as "clients". Currently, most of the popular web browsers implement the WebAuthn API.
- Relying Party: The software application that wants to authenticate a user. These can be websites, web applications, desktop applications etc.
- Authenticator device: Hardware devices (can also be virtual software) that implements CTAP2 protocol and store the user's private and public-key credential.
- Public key credentials: Public key credentials are based on public-key cryptography, where the private keys are used to sign authentication challenges, and public keys are used to verify the possession of the private key, i.e., the verification processes. Public key credentials are the fundamental authentication base of FIDO2.
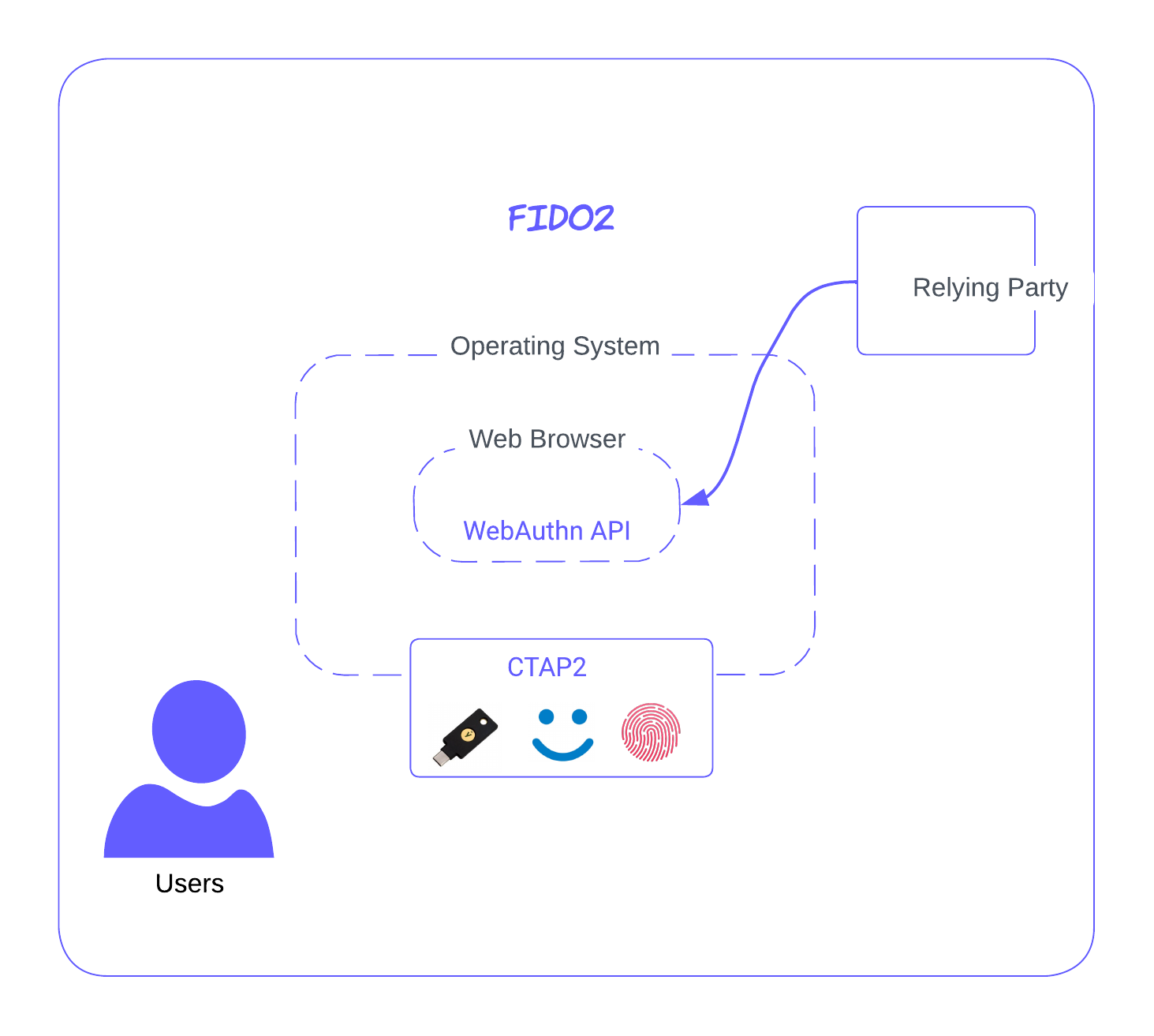

Fig: FIDO2, WebAuthn API and CTAP2
Understanding the WebAuthn registration and authentication ceremony
The WebAuthn specification describes two distinct phases related to the authentication process. A registration ceremony and an authentication ceremony.
WebAuthn registration ceremony involves registering the user's authentication device (authenticators), such as Yubikey, USB security tokens, Windows Hello, etc., to the Relying Party (RP) server. The process is RP initiated where RP data such as ID and additional information along with ClientDataHash(SHA256 hash of the client data) is sent to the user authenticator. The authenticator then creates a public-private key pair, signs the clientdatahash and sends it back to the RP. Each public key credential is scoped to a specific RP.
Below is a representation of ClientData:
{
type: webauthn.create
challenge: a random cryptographic challenge
origin: http://examplerp.com
…
}
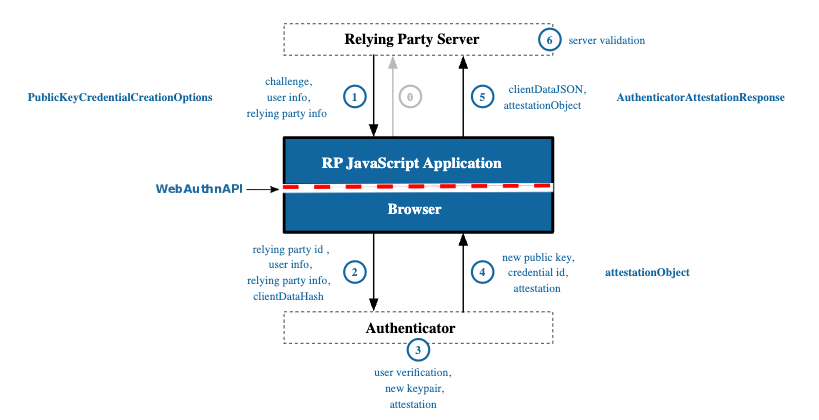

Fig: WebAuthn Registration Ceremony. https://www.w3.org/TR/webauthn-2/#fig-registration
WebAuthn authentication ceremony involves signing an authentication challenge with a public key that has been previously registered to the Relying Party during the registration ceremony. The RP receives the authenticator data via WebAuthn API (which communicates with the authenticator via CTAP2) and verifies the signed authentication data.
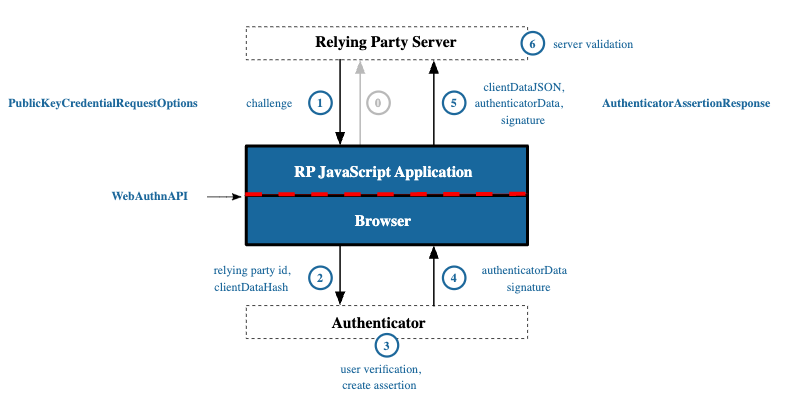

Fig: WebAuthn Authentication Ceremony. https://www.w3.org/TR/webauthn-2/#fig-authentication
Is WebAuthn used for passwordless or multi-factor authentication?
WebAuthn authentication method is passwordless based on public-key credentials. The public-key credentials (public-private key pairs) are derived/attached to various supported factors such as PINs or biometrics (Apple's Touch ID, Windows Hello, etc.). So at the minimum, WebAuthn supports multi-factor passwordless authentication schemes. But it is up to the Relying Party to decide how they want to use WebAuthn. The following are four different ways a WebAuthn-based authentication can be implemented:
- Single-factor authentication: Combination of a username and FIDO2 public-key credentials.
- Second-factor authentication: Combination of username+password and FIDO2 public-key credential as the second factor.
- Passwordless single factor: Username-less authentication using discoverable credentials.
- Passwordless multi-factor method: Username-less authentication with additional PIN/Push/Biometrics as a second factor.
Comparing WebAuthn with other passwordless methods
WebAuthn vs. One-time passcodes
One-time login codes may be in the form of one-time-password (OTP) codes, magic links (one-time login links sent to users via email) are server-generated codes that are sent to the users via email, SMS, or push notifications. Emails and SMS-based OTP codes are long considered insecure due to the high risks of interception. Although OTP methods such as TOTP and HOTP are synced between server and client authenticator devices and therefore remove the chance of interception, all of these methods are susceptible to phishing attacks.
WebAuthn, on the other hand, does not require users to enter any codes into the websites and software applications (Relying Party), which removes the chance of phishing. And since the authentication is performed in the background using WebAuthn API and CTAP, the chance of credential interception is reduced because the private key never leaves the authenticator.
WebAuthn vs. certificate-based authentication
Certificates are an excellent form of passwordless authentication method. But when compared to FIDO2/WebAuthn authentication, certificate-based authentication harbors two challenges that are worth mentioning:
-
Security and Operational challenge to maintain certificate authority. Operating a Certificate Authority (CA) is not a simple task. Although open source solutions like Teleport have made it super easy to manage certificate-based authentication for infrastructure access, the same remains challenging for relying parties whose web solutions are consumer-oriented. The challenges of maintaining CA are not the case with WebAuthn, as the authenticity of the credentials is verified based on the public-private key pair stored in the authenticators.
-
No uniform API or method for authentication. Concepts of PKI and certificate-based authentication have been around for decades. But its ubiquitous is still a far cry because there is no standard way to implement authentication logic. The buy-in from web browser vendors makes the WebAuthn API uniform and accessible to anyone who wishes to implement passwordless authentication without the need to think about operational overhead.
Operational challenges aside, it's hard to beat the security benefits of using certificates, such as auto expiry and additional contextual data such as roles, permissions, etc., for granular access control, which is not possible with the case of WebAuth. In an optimal situation, using WebAuthn for authentication and then issuing short-lived certificates for session management is a great combination for secure access control.
WebAuthn vs. U2F
Developed by the FIDO alliance itself, Universal Second Factor (U2F) is designed to be used as a second-factor authentication method, with an aim to replace phishable one-time codes based on SMS, email links, TOTP, and HTOP. The authentication method of U2F is also based on public-key credentials and is a passwordless method. So why use WebAuthn instead of U2F? The first thing is that WebAuthn has the buy-in from all major web browser vendors, which makes the API universal. Second, the WebAuthn with discoverable credentials has optimization for complete passwordless login flows. Lastly, WebAuthn API supports U2F with CTAP1 as backward compatible, so there is little reason to use something deprecated instead of a future-proof authentication specification.
5 Quick wins for authentication system developers supporting WebAuthn
Okay, I've mentioned more than once the benefits of WebAuthn.
1. Unphishable
During the WebAuthn authentication process, the authentication ceremony happens all in the background, i.e., there are no codes or PINs that the user needs to enter into the websites or software applications (Relying Party). This means that there is no way to phish users by tricking them into giving away their secrets. Further, the FIDO2 takes the Relying Party ID (RPID), meaning that the public credentials are only used with the web origin of the credentials.
2. Protection to replay attacks
Unless the attacker finds a way to exploit a web browser or application vulnerability that can capture the authentication ceremony, the authentication ceremony is hard to compromise. But assuming that even if the data exchange during the authentication ceremony is compromised, the WebAuthn regenerates a new unique cryptography challenge for each authentication ceremony. This causes previously captured authentication data to be unusable for attackers.
3. Uniform API across all environments
The biggest win for WebAuthn as a specification is that it is widely implemented by browser vendors. The specification is well supported and guaranteed to be confronting, relieving the operational overhead of managing compatibility and from low-level plumbing. There is very little space for DIY-implementations-gone-wrong security incidents when using WebAuthn.
4. Bring your own authenticator
The CTAP2 is a clearly defined protocol that describes how an authenticator can exchange authentication data with the WebAuthn API. And there are plenty of options for users to pick up their own authenticator from vendors like Yubikey, Microsoft, Apple, etc.
As long as the popularity and adoption of WebAuthn and CTAP2 supporting authenticators keep growing, authentication system developers need not worry about distributing bespoke authentication devices to users. Further, WebAuthn supports attestation, which allows accepting authenticators built by specific vendors. Attestation can be handy to organizations where they want to allow authenticators from only certain trusted and authorized vendors.
5. No need to store secrets on servers
The public-private key pairs are generated inside the authenticator, and the private keys never leave the device. This means that there is no form of secrets that needs to be stored on the server, no reason for attackers to target organizational databases for authentication secrets, and no secret leakage in the data breach!
Recommended resources for WebAuthn based authentication developers
The first recommended resource to get started is to read the WebAuthn API specification. Mozilla's tutorial on Web Authentication API is another good resource to learn both WebAuthn and how it is implemented in the context of the Firefox browser. Both the webauthn.guide and webauthn.io websites give an interactive introduction to WebAuthn and API.
Bonus: Check out this awesome-webauthn repository, which lists lots of resources and projects related to FIDO2 and WebAuthn.
Conclusion
Should you start supporting WebAuthn-based authentication in your application? You should! FIDO2 and WebAuthn have been around since 2018, and their popularity and adoption are growing. FIDO2 usage of public-key credentials for authentication, WebAuthn standardization by W3C and adoption by major web browser vendors, and the adoption of CTAP2 protocol by major hardware device manufacturers make FIDO2 WebAuthn a compelling choice of technology for moving forward with passwordless authentication. FIDO2 is probably the only complete package for implementing passwordless authentication.
WebAuthn-based passwordless access to infrastructure resources using Teleport
Teleport is an open-source Access Platform that consolidates connectivity, authentication, authorization and audit into a single platform to improve security & agility. Teleport has long supported WebAuthn-based second-factor authentication for infrastructure access. With Teleport 10, our team is bringing a complete passwordless authentication solution. Subscribe to our newsletter for updates on Teleport's passwordless features.
Teleport cybersecurity blog posts and tech news
Every other week we'll send a newsletter with the latest cybersecurity news and Teleport updates.
Interested to learn more about WebAuthn? Join our Slack channel to discuss - https://goteleport.com/community-slack!
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

