Home - Teleport Blog - You Accidentally Hired a DPRK IT Worker. What Next? - Oct 26, 2023
You Accidentally Hired a DPRK IT Worker. What Next?
Last week, the US Justice Department put out another memo about the Democratic People’s Republic of Korea (DPRK) IT working for US companies with an aim to generate illicit revenue for the North Korean government to fund its ballistic missile program. On Oct 18th, the US government seized 17 websites and over $1.5M of revenue. A screenshot of a DPRK IT Worker company/agency is shown below.

A homepage for one of the DPRK IT Freelancing Firms: via Internet Archive.
DPRK IT Workers seem to offer both legitimate IT freelancers and in some instances, infiltrating the computer networks of unwitting employers to steal information and maintain access for future hacking and extortion schemes. This year, there is an increased sophistication for these workers, including using US IPs to look like they have a US presence. These individuals mostly passed background checks, and there are a few things to look out for if you think Chad* from IT might be working from DPRK.
These are:
- Unwillingness or inability to appear on camera or video meetings
- Undue concern about requirements of a drug test or in-person meetings and having the inability to do so
- Indications of cheating on coding tests or when answering employment questionnaires and interview questions
The above-mentioned memo has more guidelines, but this person could be a bad hire or overemployed.
Detecting DPRK IT workers
To look specifically for DPRK IT Workers, there are a few from the Fact Sheet "Guidance on the Democratic People's Republic of Korea Information Technology Workers." This fact sheet has some more practical tips that you can use to alert on. Some are:
- Multiple logins into one account from various IP addresses in a relatively short period of time, especially if the IP addresses are associated with different countries.
- Inability to conduct business during required business hours, and inability to reach the worker in a timely manner, especially through “instant” communication methods.
- Regularly geo-locate company laptops to verify they match the logins of employees' addresses.
Below is a hypothetical scenario in which we’ve accidentally hired a DPRK IT Worker named Chad.
Detect with Teleport Access Monitoring
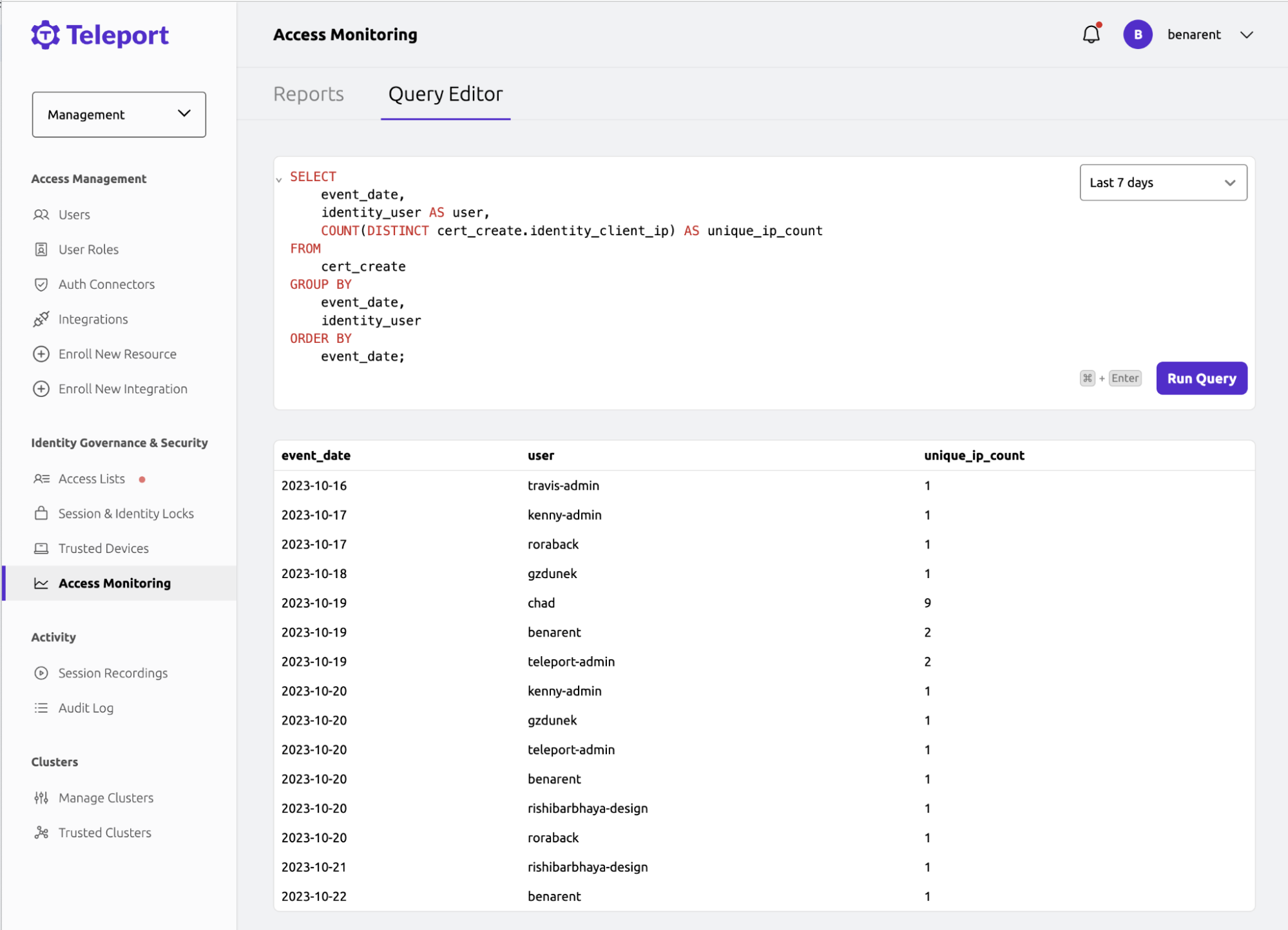
We have some suspicions about a freelance contractor Chad. We’ll start by asking if they have accessed systems with multiple IPs, thinking they could be using multiple jump hosts. We’ll be using Teleport’s latest Athena-based Access Monitoring. We'll create a new query instead of using the default Privileged Access Report.
SELECT
event_date,
identity_user AS user,
COUNT(DISTINCT cert_create.identity_client_ip) AS unique_ip_count
FROM
cert_create
GROUP BY
event_date,
identity_user
ORDER BY
event_date;
We can quickly run this query in Teleport without jumping into our SIEM... Chad has reported WFH the last week, so why are they using 9 IPs? Time to investigate further…

There are still possible reasons for the multiple IPs. We’ll run a query to see if Chad does most of their SSH Sessions after hours. To do this, I will create a query looking for interactive SSH Sessions happening between the hours of 10pm and 5am.
SELECT
DATE(from_iso8601_timestamp(time) AT TIME ZONE 'America/Los_Angeles') AS event_date,
COUNT(*) AS count,
user
FROM
session_start
WHERE
EXTRACT(HOUR FROM from_iso8601_timestamp(time) AT TIME ZONE 'America/Los_Angeles') >= 18
OR EXTRACT(HOUR FROM from_iso8601_timestamp(time) AT TIME ZONE 'America/Los_Angeles') < 5
GROUP BY
DATE(from_iso8601_timestamp(time) AT TIME ZONE 'America/Los_Angeles'),
user
ORDER BY
event_date;
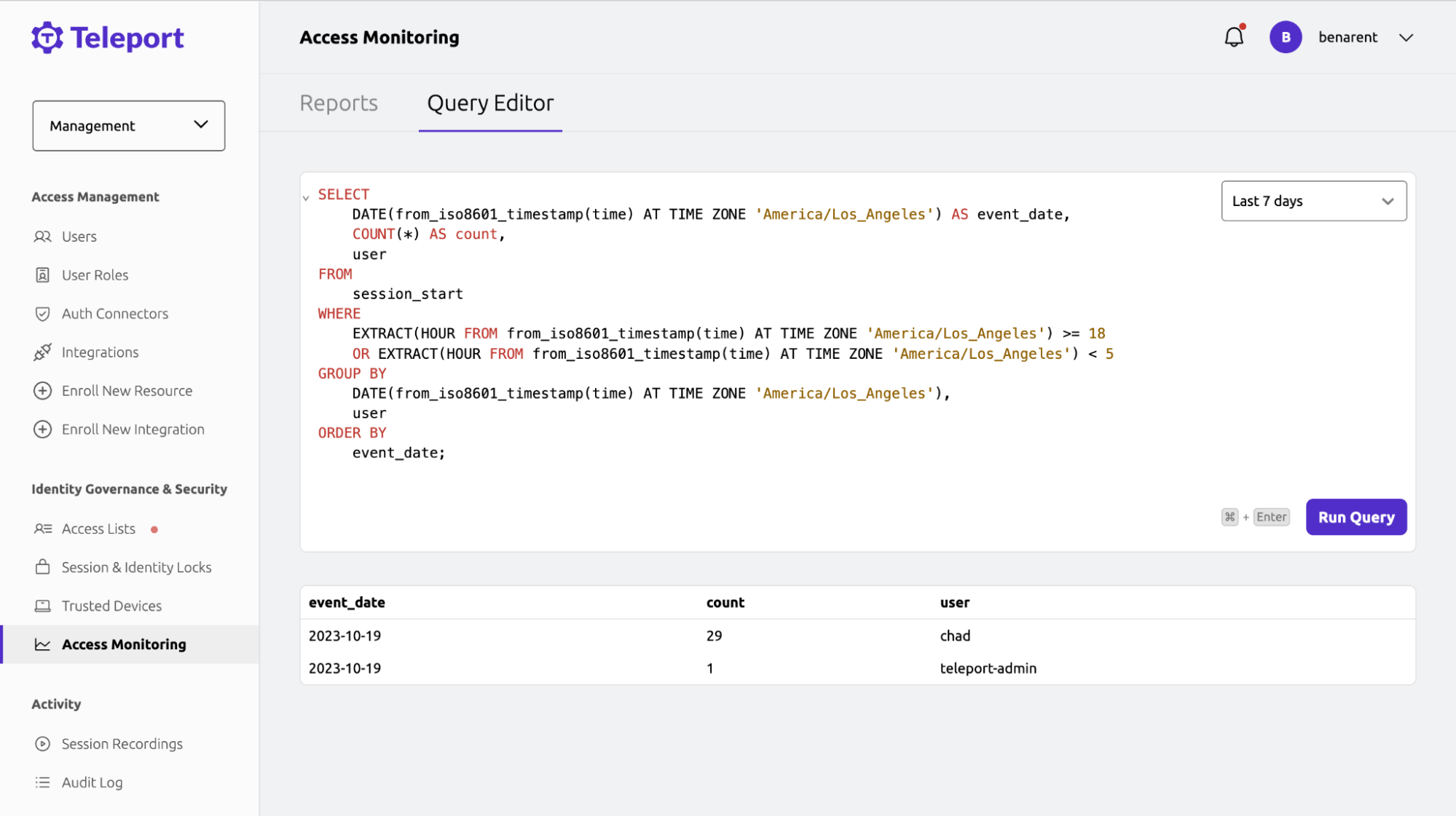

Chad had 29 interactive SSH Sessions in the early morning, easily mapped to the DPRK timezone. It looks like Chad is up to something funky — time to lock Chad's access.
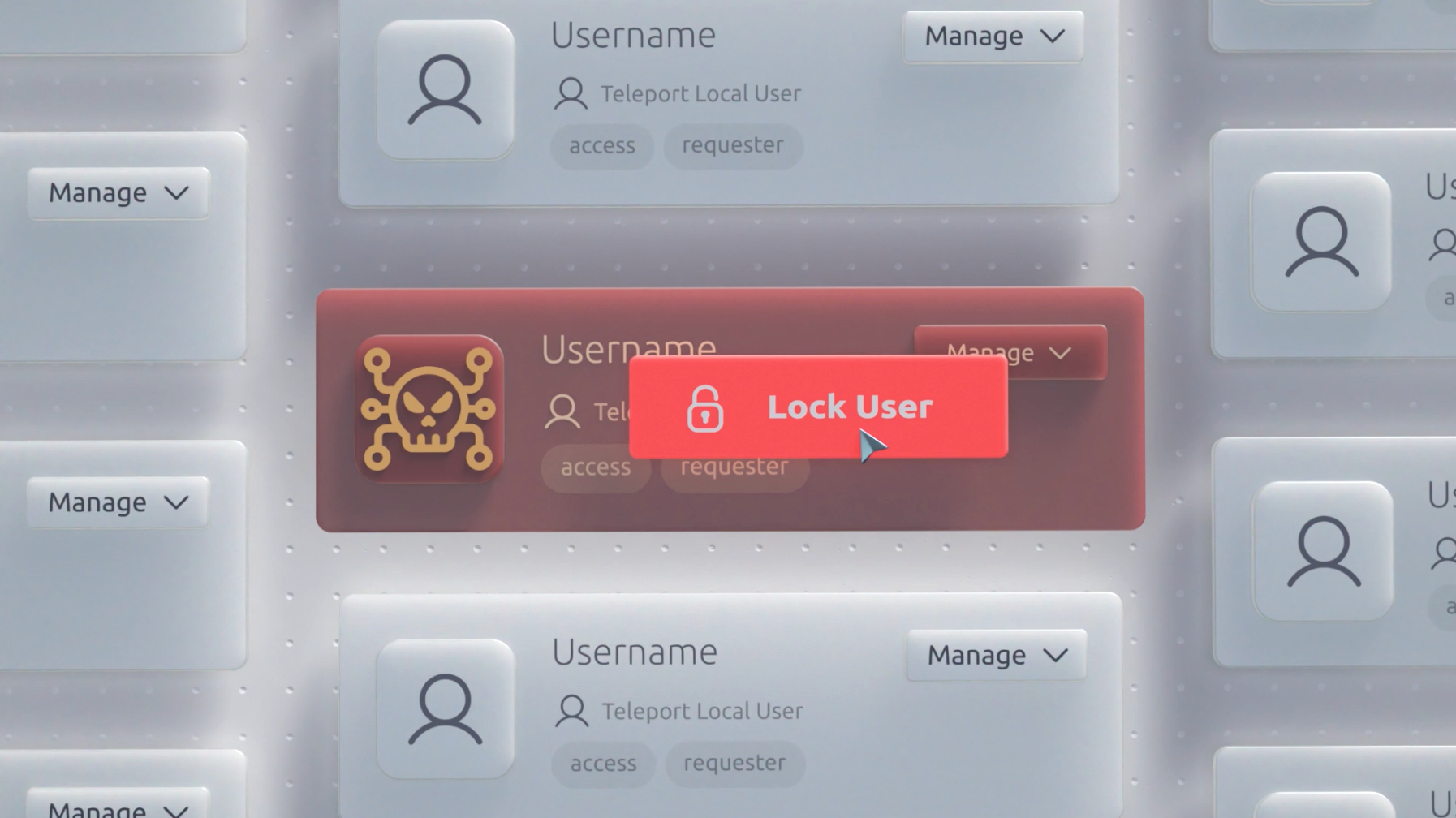
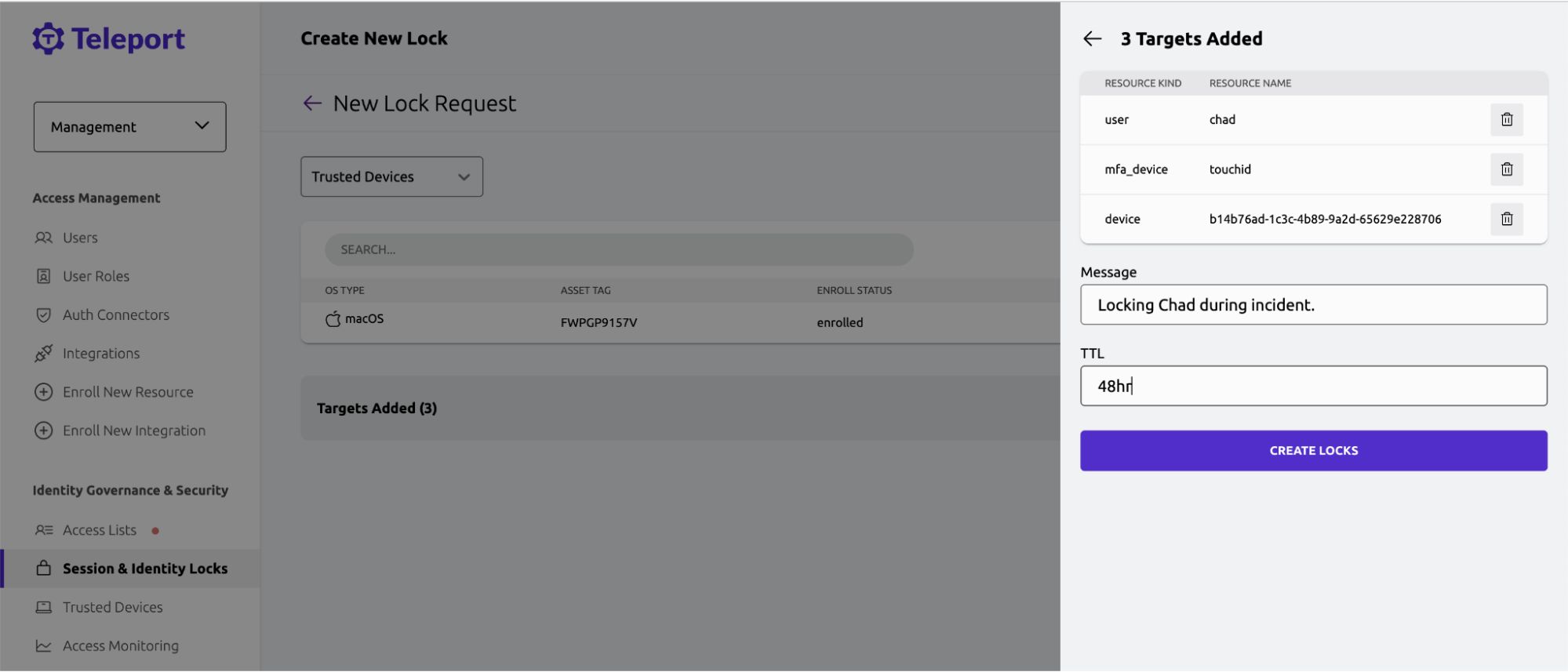
Lock access
We’ve now identified that Chad's access pattern is out of the normal, and we want to lock access immediately. Instead of locking all freelancers, we’ll use Teleport’s Locks to only target Chad.
We’ll start by locking the:
- Chad user account
- Laptop and MFA Token we shipped to Chad
Using Teleport to lock the user has the benefits. It’s instant and doesn’t require the immediate rotation of credentials for the freelancer. Locks can be created using the Teleport UI or using the CLI admin tools.

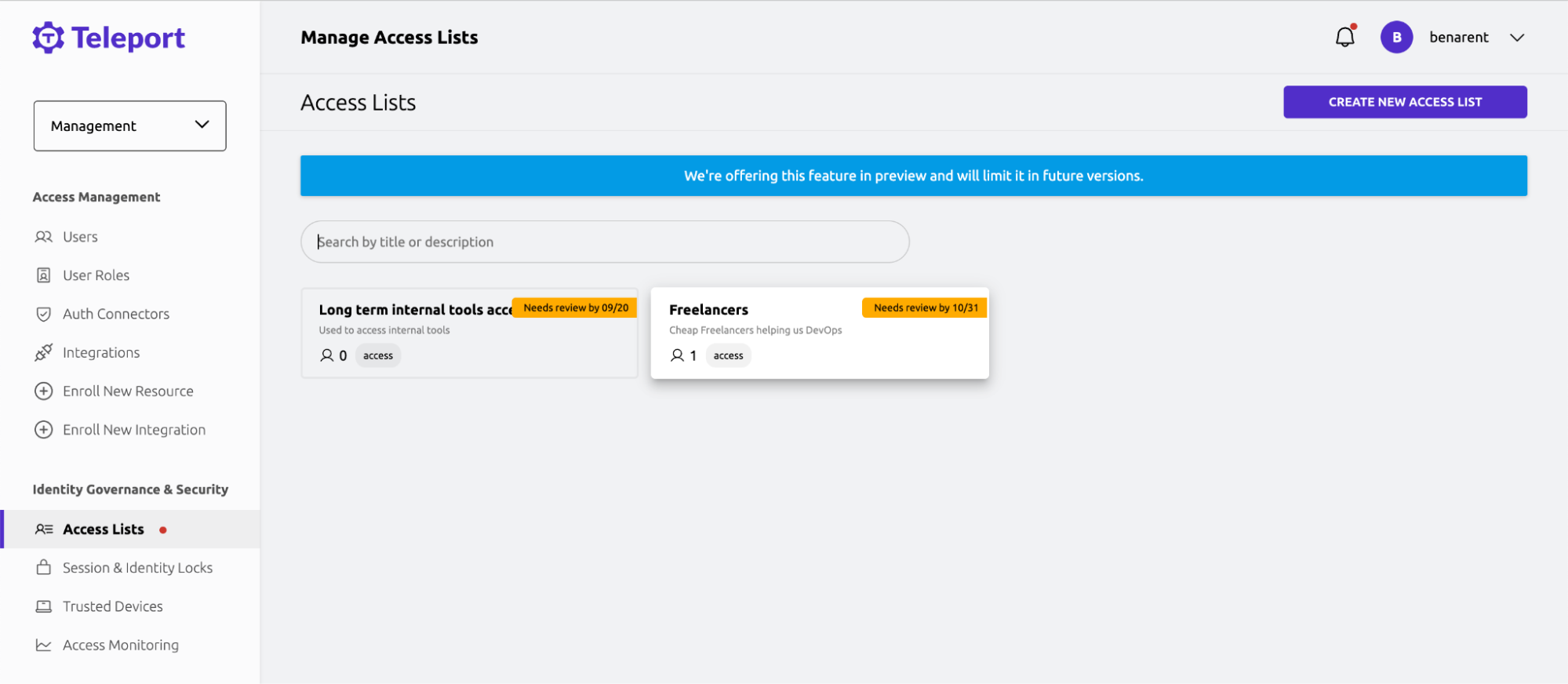
Review freelancers’ access
This organization hires many freelancers, and most have been amazing, but now is a time for us to review the Access Lists for freelancers access. Access Lists lets the team easily create groups of access, with in-built auditing and reviews. This makes it easy for security teams to provide the tools and sandbox for access but lets the freelancers’ recruiter divvy out access.

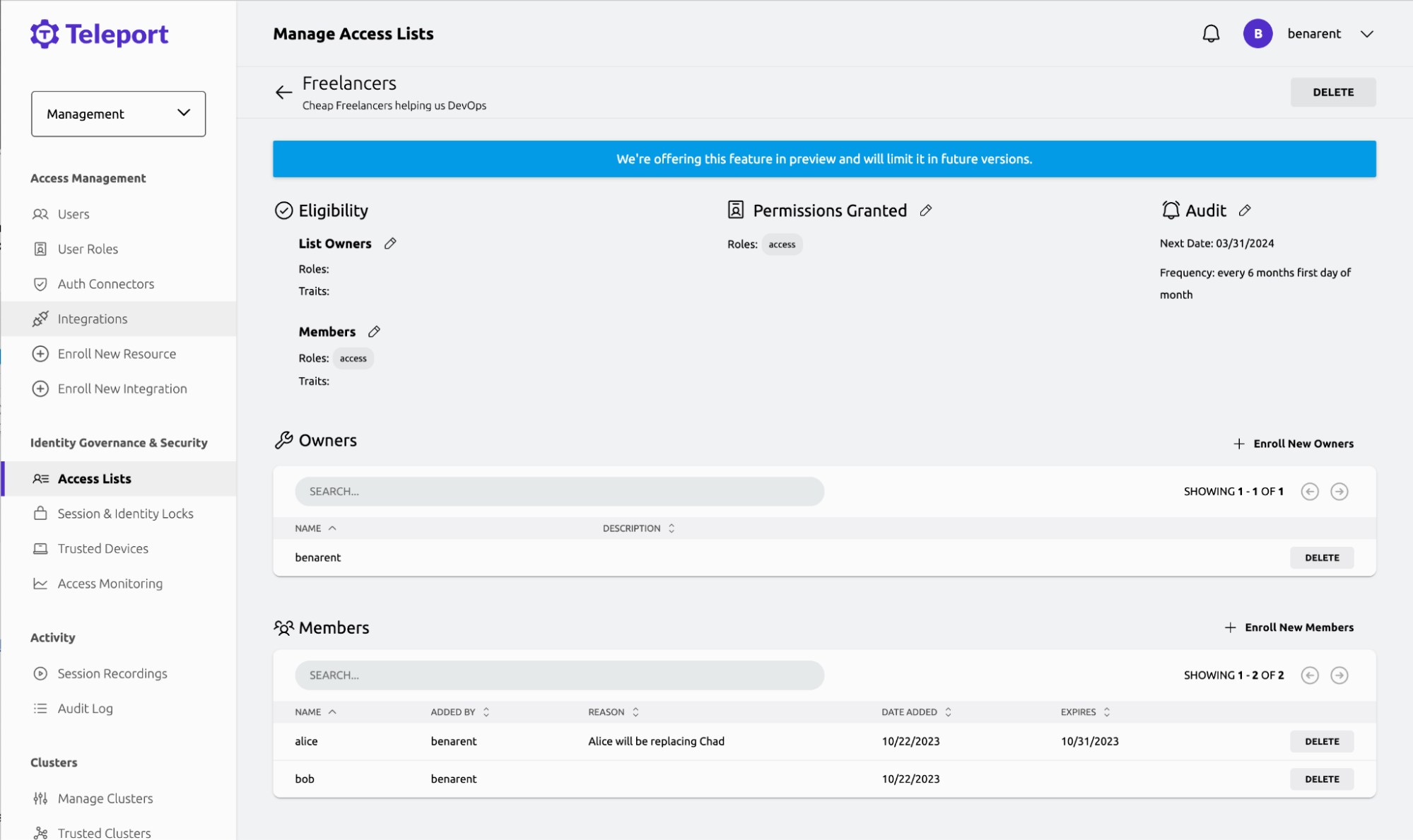
Since Chad is now locked, we’ll add a new freelancer to the access list. Access Lists have a few benefits for providing access, such as adding a freelancer to a project and having their access auto-expire at the end of their contract. This significantly reduced the possibility of an ex-contractor having overly defined permissions.

Remediation
We’ve now locked Chad and found a replacement for their work. The next step might be more serious, depending on your organization. A team's incident response should have already created an incident and will start to review the possible exposure of access.
On a serious note, if teams think they accidentally hired a DPRK IT Worker, they should contact their local FBI field office and report an issue to ic3.go. It’s best to get to know your local FBI Field Office before an incident; we go in-depth with the SF Field Office with the When a Startup Should Call the FBI podcast.
Identity Governance & Security
The recent events in DPRK provided a perfect scenario for today's Identity Governance & Security launch. The combination of Access Lists, Access Monitoring and Access Requests provides a solid foundation for an Identity Governance & Security solution. You can use it to help protect teams from attacks on engineers' identity or to address and thwart insider threats quickly.
We’ll have an in-person session and demo at Teleport Connect 2023. Otherwise, catch this upcoming webinar on Oct. 31 at 10 am: Infrastructure Auditing Made Easy.
Request a demo of Identity Governance & Security
If you would like a complete demo of Teleport Identity Governance & Security, please reach out to our team.
Misc: *Why Chad? According to the “Cast of characters” from Alice and Bob - Wikipedia, Chad is “A third participant, usually of malicious intent[15]” Sorry to all the Chads in my life.
**DPRK remote IT workers may be subjected to forced labor and constant and close surveillance by government security agents. IT workers have also been forced to work 12-16 hours per day, which may be an indicator of forced labor and an abuse of their human rights.
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

