
TELEPORT ACCESS PLATFORM
Teleport Policy
Unify and control access policies across
all of your infrastructure

Trusted by Market Leaders


















Identify and Lock Threat Actors
It takes an adversary 84 minutes to pivot from an initial breach to the rest of your infrastructure. (Crowdstrike 2023 Global Threat Report)


Stop threat actors in their tracks and manage access paths and policy with Teleport Policy.
Gain Visibility and Control
Without Teleport, it takes the fastest companies a couple of hours to identify who has access to specific infrastructure. With Access Graph, you can view access relationships in seconds.
Comprehensive Visibility
View unified, up-to-date relationships and policies between all users, groups, and computing resources with Access Graph.
Instant Discovery
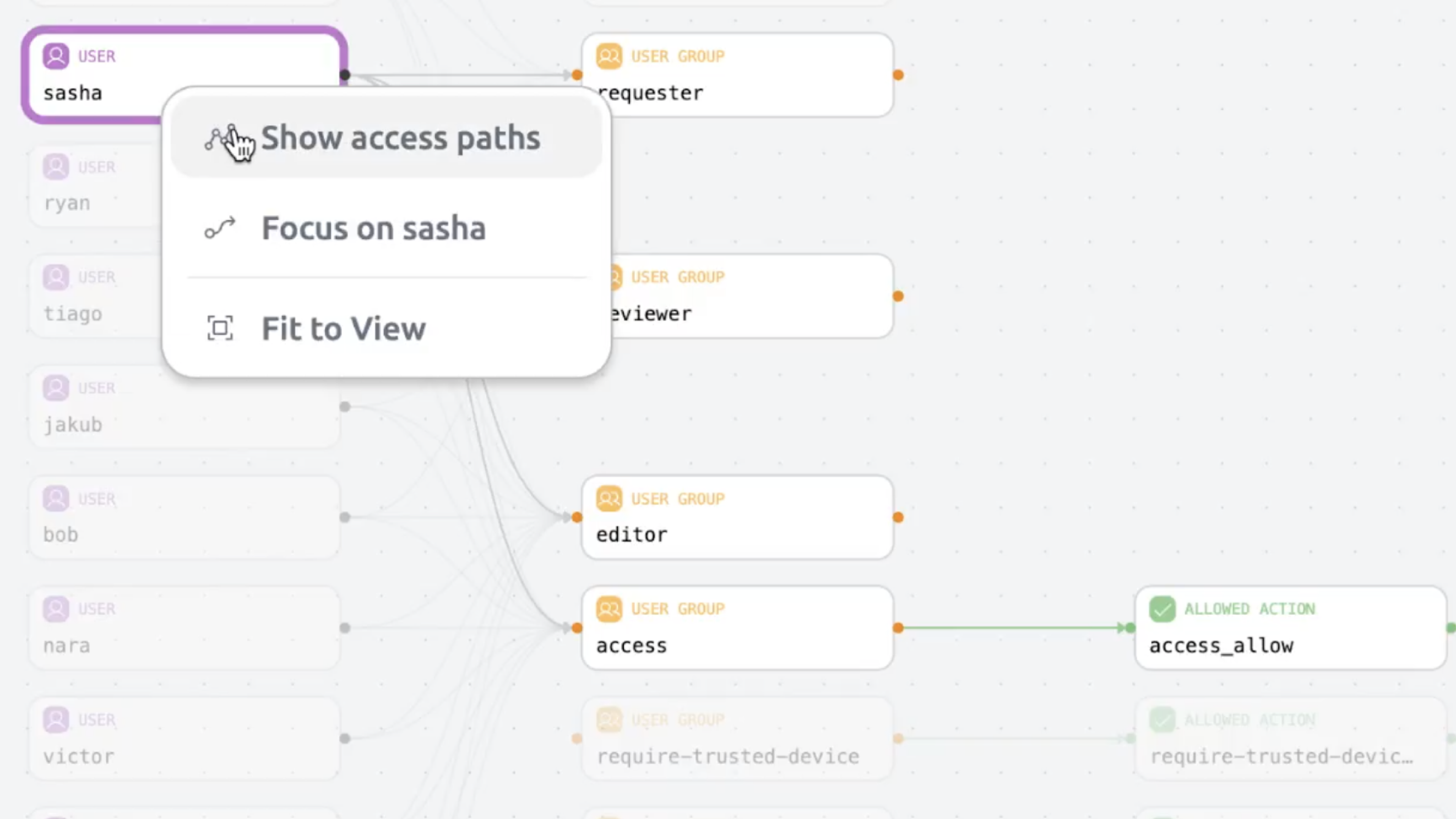
Explore users, policies, and resources to instantly uncover who has access to what resource.
Eliminate Shadow and Risky Access
Uncover shadow and risky access patterns. Achieve fine-grained oversight and continuous tuning of privileges and access behavior.
Query Access Graph
Dive into detailed access paths for users, protocols, and resources through powerful queries.
Optimize Access
Strategically analyze and refine access paths to proactively eliminate potential risks and fine-tune access behavior.
Unify Policy Management
Manage policy across your infrastructure in one place. Get rid of esoteric languages and numerous file formats and templates.
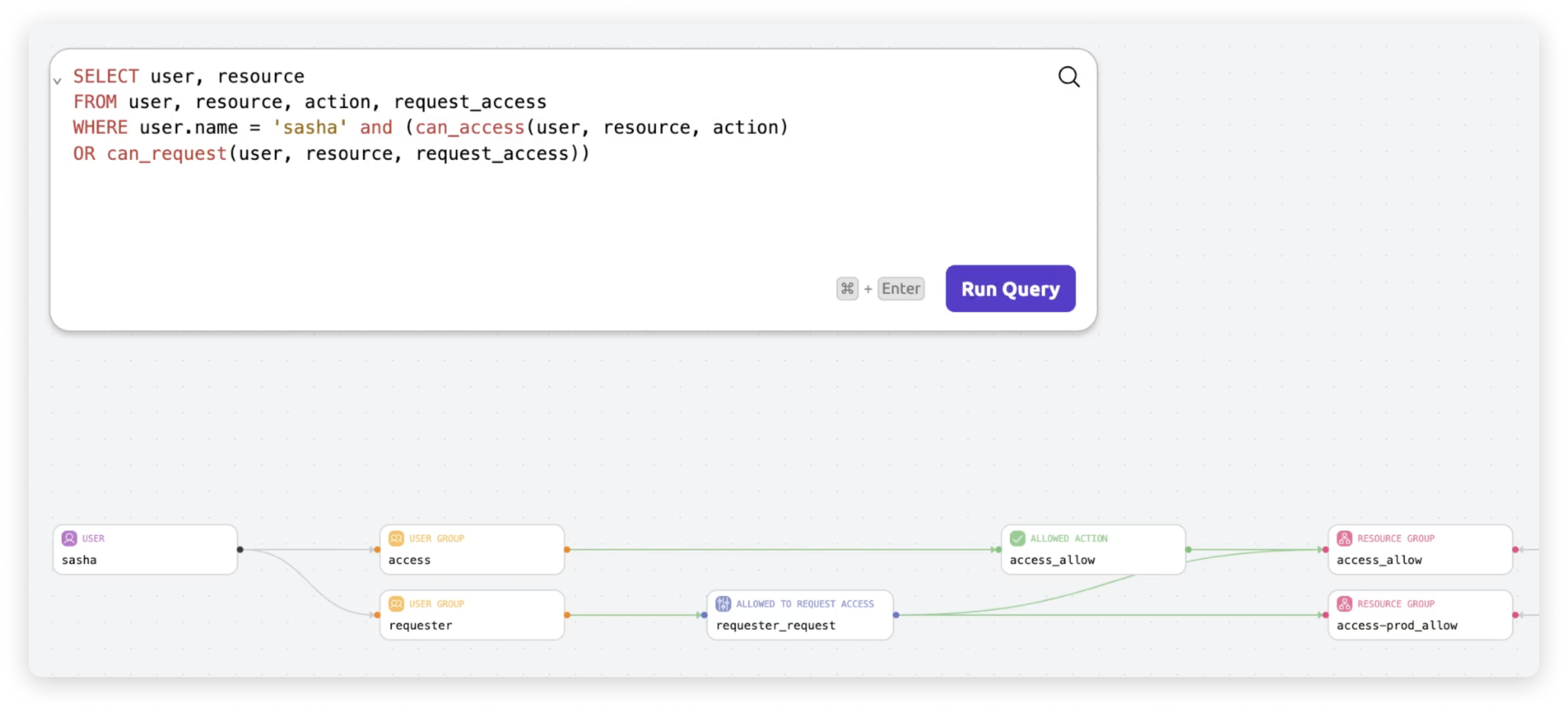
Query Policy
Query policy across AWS, Azure, GCP, on-premises, services and custom apps. Get rid of esoteric, discrete forms and templates and standardize query language with SQL.
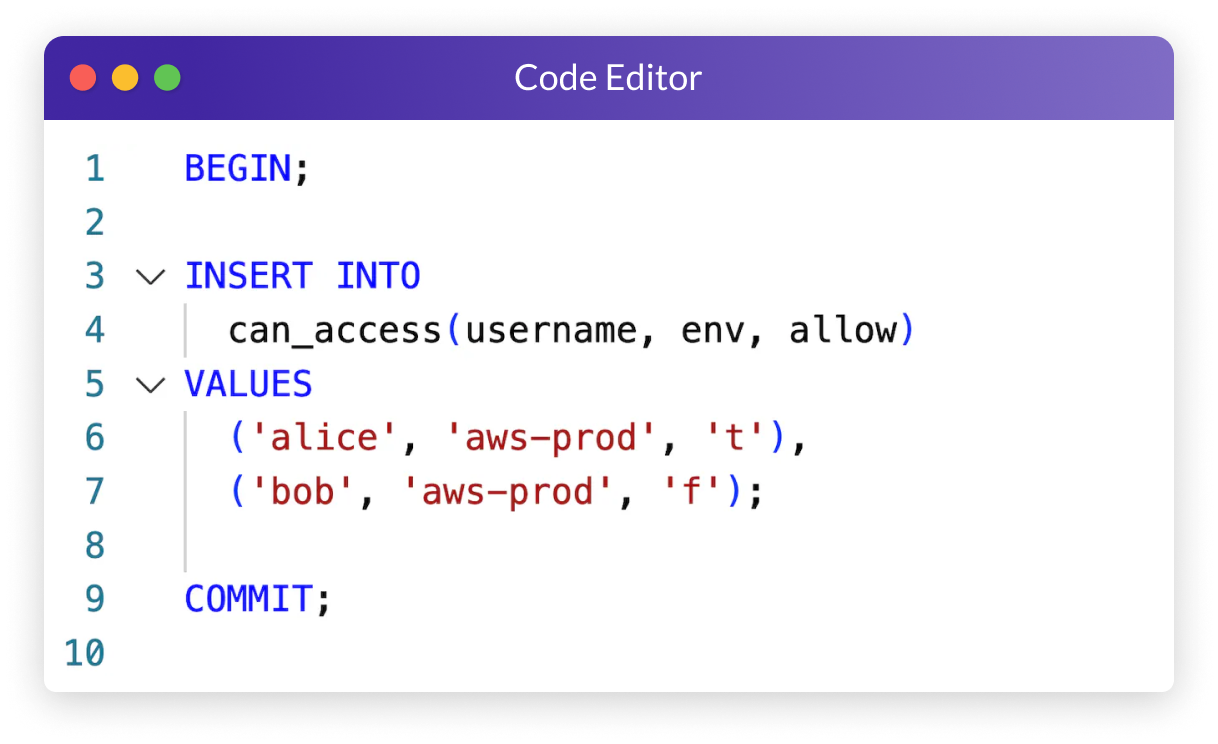
Manage Policy
Manage policy for your infrastructure. Write policy in one place and deploy everywhere. (Management with SQL coming in April 2024)

Protect Your Infrastructure Today
What Our Customers Say
Learn More
TELEPORT ACCESS PLATFORM
Teleport Access
On-demand, least privileged access, with identity security and zero trust
Teleport Identity
Harden your infrastructure with identity governance and security
Teleport Policy
Unify and control access policies across all of your infrastructure