
Teleport
Sync EC2 Tags and Teleport Node Labels
- Version 16.x
- Version 15.x
- Version 14.x
- Version 13.x
- Older Versions
When running on an AWS EC2 instance, Teleport will automatically detect and import EC2 tags as
Teleport labels for SSH nodes, Applications, Databases, and Kubernetes clusters. Labels created
this way will have the aws/ prefix. When the Teleport process starts, it fetches all tags from
the instance metadata service and adds them as labels. The process will update the tags every hour,
so newly created or deleted tags will be reflected in the labels.
If the tag TeleportHostname (case-sensitive) is present, its value will override the node's hostname.
$ tsh ls
Node Name Address Labels
-------------------- -------------- -----------------------------------------------------------------------------------------------------------------------
fakehost.example.com 127.0.0.1:3022 env=example,hostname=ip-172-31-53-70,aws/Name=atburke-dev,aws/TagKey=TagValue,aws/TeleportHostname=fakehost.example.com
For services that manage multiple resources (such as the Database Service), each resource will receive the same labels from EC2.
Prerequisites
-
A running Teleport cluster. If you want to get started with Teleport, sign up for a free trial or set up a demo environment.
-
The
tctladmin tool andtshclient tool version >= 15.2.4.On Teleport Enterprise, you must use the Enterprise version of
tctl, which you can download from your Teleport account workspace. Otherwise, visit Installation for instructions on downloadingtctlandtshfor Teleport Community Edition.
- One Teleport agent running on an Amazon EC2 instance. See our guides for how to set up Teleport agents.
Enable tags in instance metadata
To allow Teleport to import EC2 tags, tags must be enabled in the instance metadata. This can be done via the AWS console or the AWS CLI. See the AWS documentation for more details.
Only instances that are running on the Nitro system will update their tags while running. All other instance types must be restarted to update tags.
AWS EC2 Console
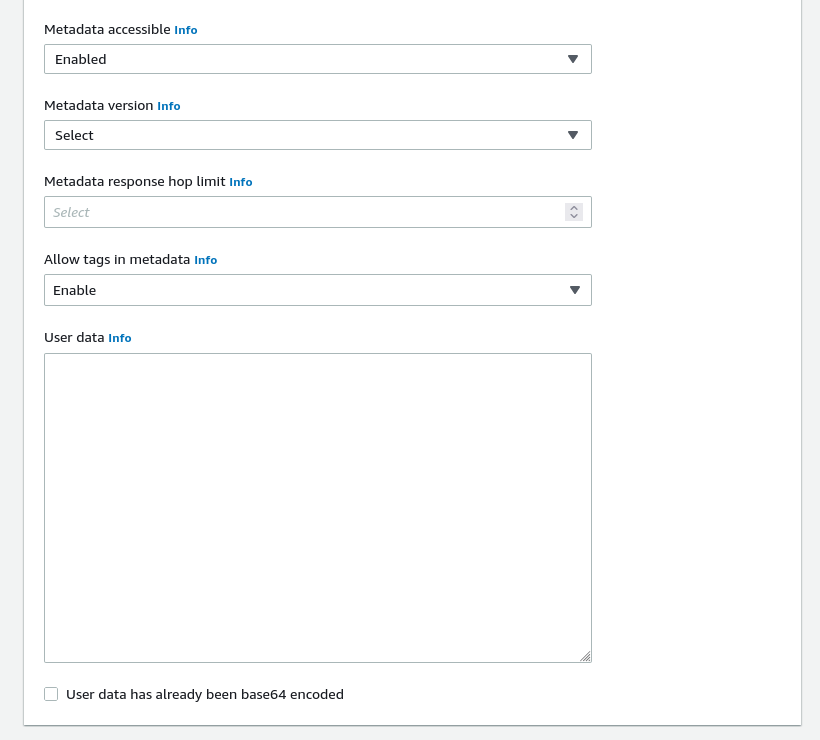
To launch a new instance with instance metadata tags enabled:
- Open
Advanced Optionsat the bottom of the page. - Ensure that
Metadata accessibleis not disabled. - Enable
Allow tags in metadata.
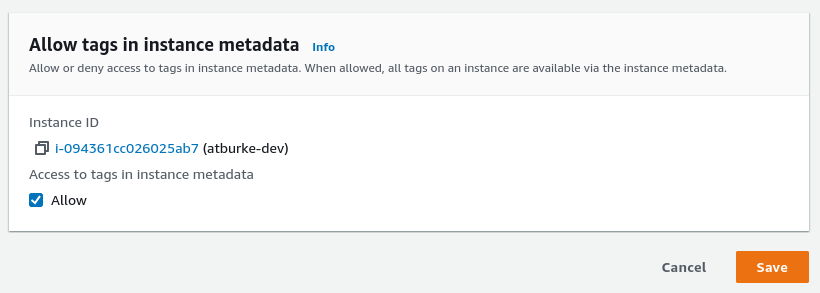
To modify an existing instance to enable instance metadata tags:
- From the instance summary, go to
Actions > Instance Settings > Allow tags in instance metadata. - Enable
Allow.
AWS CLI
To modify the instance at launch:
aws ec2 run-instances \ --image-id <image-id> \ --instance-type <instance-type> \ --metadata-options "InstanceMetadataTags=enabled"...
To modify a running instance:
aws ec2 modify-instance-metadata-options \ --instance-id i-123456789example \ --instance-metadata-tags enabled