Home - Teleport Blog - Teleport 1.3 - SSH authentication with 2FA
Teleport 1.3 - SSH authentication with 2FA
We built the Teleport SSH server to make it easy and secure for teams to access distributed infrastructure.
Teleport supports two factor authentication by default, as we believe that it is a requirement for an SSH tool concerned with security. We originally only supported Google authenticator. Now we are happy to announce that Teleport natively supports the Universal Second Factor (U2F).
What is U2F?
U2F - Universal 2nd Factor is an open authentication standard designed for USB, NFC and Bluetooth devices. U2F is more secure than SMS and it can be a pleasure to use, for example:
- A computer asks you for your username and a password (1st factor auth).
- Then it asks you to plug a tiny USB key into your laptop and press a button on it.
- Profit!
Why is U2F better?
Having a secure second factor that does not depend on your phone is becoming more important given the latest events with attacks on users relying on SMS for two factor authentication or hackers exploiting vulnerabilities in the phone’s operating systems.
Even if we disregard possible OS hacks, we still have to keep in mind that apps like Authy and Google Authenticator are using one-time token algorithms like TOTP/HOTP that are sharing a common secret with applications without sufficient authentication of the application requesting your second factor. Authentication is a two-way street, remember?
To solve these problems, U2F specifies a protocol for a device that can not be easily hacked by the third party remotely, is a magnitude simpler than a phone (reducing possible surface of the attack) and provides many other benefits, like MITM and phishing protection.
In addition, using a separate, dedicated device for your second factor brings us into a more familiar realm of having a physical key to access an environment. This has the benefit of making the key easier to track and gives the owner a more tangible sense of responsibility. According to this report by Google, using U2F keys makes the process of using two factor authentication faster and less prone to errors.
How does U2F work?
Here’s the flow as explained by U2F YubiKey page:
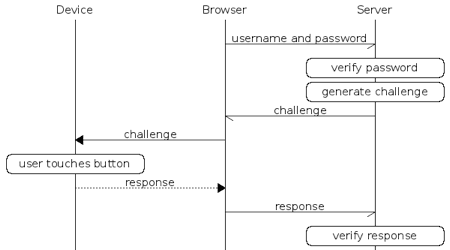

As a second factor, you have to have a U2F device (e.g. YubiKey USB stick as in the photo below) connected and press a button to respond to the authentication request.


Pressing a button is an additional security measure to make sure your device can not be used by some program without you knowing about it. This also means you have a convenient tiny device you can keep plugged into your computer.
An authentication challenge request is generated by the app and is passed via browser to your device. If the challenge response is successful, you will be granted access.
This flow requires some coordination from the browser or command line tools as they need to be able to communicate to the connected device.
Currently only Chrome and Opera are supporting it, or you can install it on linux CLI using u2f-host command line utility.
Some U2F internals
At the heart of the U2F protocol is public key crypto. A U2F device holds private key and signs security challenges verified by public keys stored on the application side.
This approach makes U2F superior to the TOTP/HOTP family of algorithms used for two factor authentication (you have seen it in your Google Authenticator or Last Pass by entering temporary codes) that rely on shared secret key that can be compromised and do not provide any built in protection from phishing or man-in-the middle (“MITM”) attacks. They can also be less convenient, as you have to type in codes many times.
U2F provides strong protection against MITM and phishing attacks by checking the origin of the application that requests the signature and channel IDs of the TLS connection, making sure that unknown applications can not simply ask to authenticate if the YubiKey does not trust them or the underlying connection.
You can read more about the protocol security measures in this overview or do a deep dive into the protocol’s specs.
Is U2F perfect? No, of course there is still the risk of a stolen or cloned device that the protocol tries to solve by keeping a counter. However, it only provides weak protection as if the original token may be never used again or used long after the cloned device.
Nevertheless, U2F is a great alternative for those serious about securing second factor authentication.
Teleport cybersecurity blog posts and tech news
Every other week we'll send a newsletter with the latest cybersecurity news and Teleport updates.
Using U2F with Teleport
You can find and download the latest Teleport release with U2F support here. Then you can easily set up U2F through the Teleport Auth Service configuration file:
auth_service:
u2f:
enabled: true
app_id: https://teleport.gravitational.io
# U2F facets must be set to Teleport proxy server(s):
facets:
- https://teleport.gravitational.io:443
- https://teleport.gravitational.io
You can read more in the Teleport documentation.
Then you can start using U2F from terminal or web. Please let us know if you have any feedback by creating an issue or pull request or emailing [email protected].
Special Thank You
Special thank you to jcj83429, alchar, bibekaur and jdahiya who have contributed the initial U2F implementation.
P.S. Also thanks to LVH for reading drafts of this blog post.
Table Of Contents
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.
Tags

Subscribe to our newsletter

