Home - Teleport Blog - Teleport Automatic Agent Updates: The Details
Teleport Automatic Agent Updates: The Details
The recent release of Teleport 13 brings a much-anticipated feature allowing Teleport agents and Teleport Kubernetes Agents to be updated automatically.
In this blog post, we'll look at why that's so important as well as how automatic agent updates work.
Why update Teleport agents?
Like any other software, regular updates are important. And it's no different with Teleport or Teleport agents. Here are a few 'Teleport specific' reasons why you need to keep Teleport agents updated:
- Compatibility. It's best practice to align the Teleport agent version with the Proxy and Auth service versions. This helps to maintain the integrity of your infrastructure as each update helps to ensure compatibility with latest features and security implementations. As you update the Teleport proxy, agents should follow suit with that latest version.
- Security and Stability. While new updates often introduce new and exciting features, they also come with additional, less exciting, updates that enhance the security and stability of the system. Regular updates ensure that you have the latest protection and performance that these updates bring.
- Avoiding cluster alerts. Teleport monitors the inventory of cluster components and when one is lagging behind, cluster notifications may be generated to encourage users to upgrade.
I think we all see the importance here.
But we also know that with the importance of updating often comes the annoyance of execution. You know — updating each and every agent for each and every update that's released.
Well this is why we've implemented an auto-updating feature.
Let's see how automatic agent updates can smooth this out.
What makes automatic agent updates so special?
With agent auto-updates, it's a one-time setup that will then automate the process going forward. Put in the work up front and Teleport will take it from there.
When enrolled with agent automatic updates, the updater will receive a pre-configured maintenance schedule from the Teleport cluster, and when a schedule is available it will run and update if applicable.
The updater is also designed to be decoupled from Teleport in such a way that it can update an agent even if that agent cannot join the Teleport cluster. This is helpful if an agent requires an update to fix the issue stopping it from joining the cluster.
Finally, a critical flag can be toggled to specify that an update is critical and will apply even if outside the regular maintenance window. This is necessary for critical security issues or exploits that need to be patched immediately.
How do automatic agent updates work?
So how does all this work?
Currently, Teleport supports automatic agent updates for systemd-based Linux distributions using apt or yum package managers, and Kubernetes clusters.
Also, note that the automatic updates are for the agents only. Instructions for updating the Teleport Cluster itself can be found in the documentation.
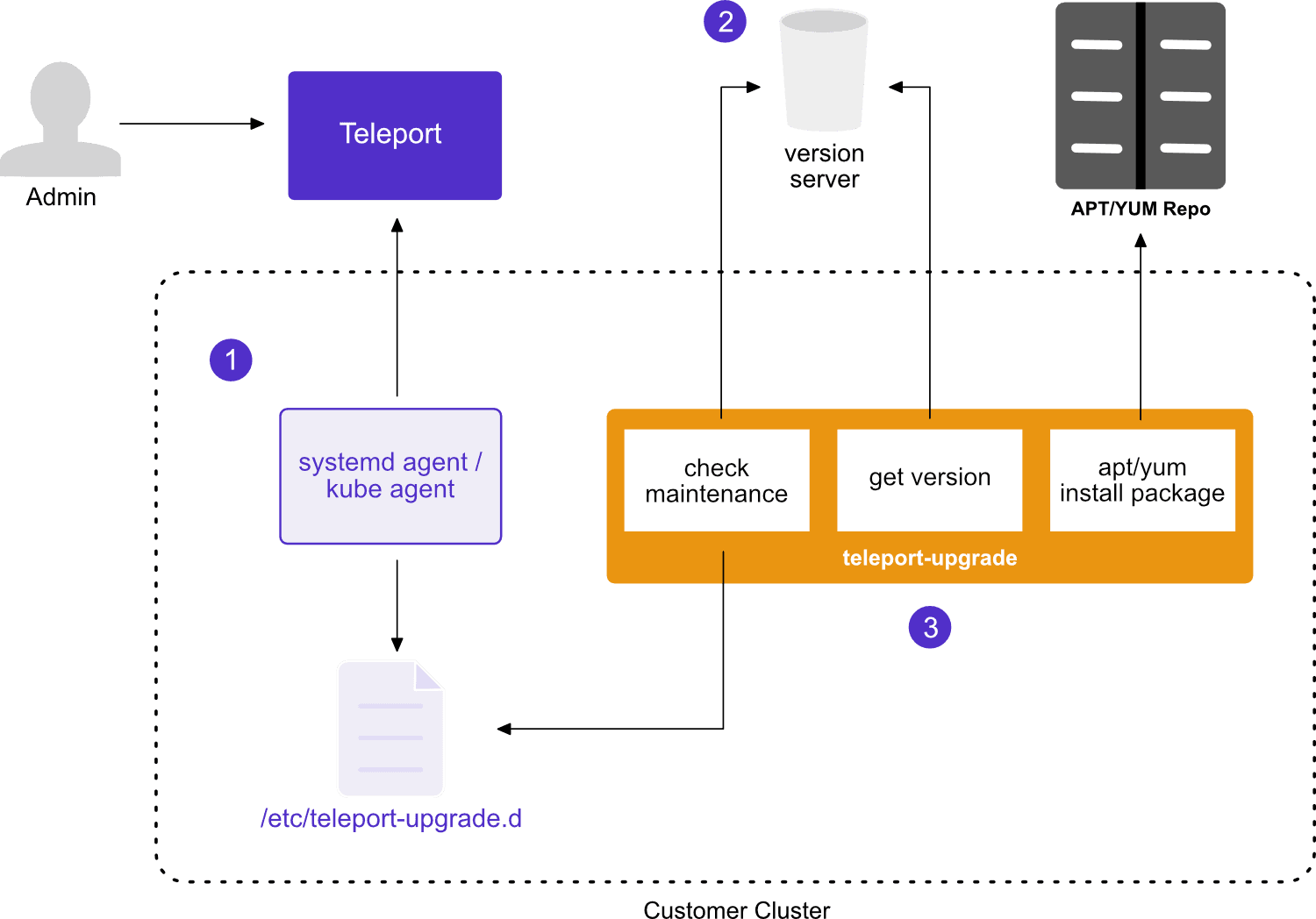
With that information, let's take a look at this overview:

-
One major part of the automatic agent upgrade process is the maintenance window. An admin will create a maintenance window on the Teleport cluster consisting of the maintenance window start time as well as days of the week maintenance is allowed. The systemd agent/kube agent will fetch this maintenance window and write it to the server in the /etc/teleport-upgrade.d folder.
-
Next we have the Version Server. This must be a webserver with trusted TLS certificates, and reachable by all agents. It can be a simple Amazon S3 bucket, Google Cloud Storage, or even a regular webserver like nginx over https. This server must include a file specifying the targeted version, and another file specifying whether this update is critical or not. This serves as the source of truth as to what version the Teleport agents will be updated to and whether critical or not. This server endpoint will also be written to the /etc/teleport-upgrade.d folder on the agent server.
-
Finally, we have the teleport updater package. It's a separate binary altogether from the agent, allowing the agent to be updated even if the agent has broken connection with the cluster. The updater performs a number of tasks like:
-
checking the version server to see if the update is marked critical or not
-
checking whether a maintenance window is active or not
-
retrieving the specified agent version from the version server
-
updating the agent if conditions are met
-
This flow will differ a bit between a systemd enrollment vs a teleport kube agent enrollment, as well as if you are self-hosting Teleport or in Teleport Cloud, with the latter requiring less steps.
Teleport Cloud users can use Teleport Cloud's hosted version server if they enroll in automatic updates whereas self-hosted installations will need to host their own version server. Other differences between the two are noted in the docs.
Learn more
So if you're using Teleport Enterprise Cloud or Teleport Enterprise self-hosted, you can now enroll your agents in Teleport's new auto-update feature and skip having to put in the extra work for each new future release.
To get started implementing automatic agent update functionality for your cluster, follow along in our documentation.
If you aren't using Teleport, you can get started today with a 14-day free trial.
Table Of Contents
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.
Tags

Subscribe to our newsletter

