Teleport Blog - Teleport 14 - Sep 25, 2023
Teleport 14

Once again it’s time for everyone’s favorite announcement: a brand new Teleport release! This release marks version 14 of Teleport and is packed with features, including a UI makeover. Let’s dive in! Teleport 14 brings the following new major features and improvements:
Below are a few highlights:
- Access lists [Enterprise]
- Limited passwordless access for local Windows users [Community Edition]
- Unified resource view [All]
- ClickHouse support for database access [All]
- Advanced audit log [All]
- Kubernetes apps auto-discovery [All]
- Extended Kubernetes per-resource RBAC [All]
- Oracle database access audit logging support [All]
- Enhanced PuTTY support [All]
- Support for TLS routing in Terraform deployment examples [All]
- Machine ID: Kubernetes Secret destination [All]
- Discord and ServiceNow hosted plugins [Cloud]
In addition, this release includes several changes that affect existing functionality listed in the “Breaking changes” section below. Users are advised to review them before upgrading.
Teleport Release notes are also available in GitHub and via automated changelog generation on our #releases Slack channel.
Product Updates
Unified resources view
The web UI in Teleport 14 has been updated to show all resources in a single unified view.
This is the first step in a series of changes designed to support a customizable Teleport experience and make it easier to access the resources that are most important to you.
Access lists
Teleport 14 introduces foundational support for access lists, an extension to the short-lived access requests system targeted towards longer-term access. Administrators can add users to access lists, granting them long-term permissions within the cluster.
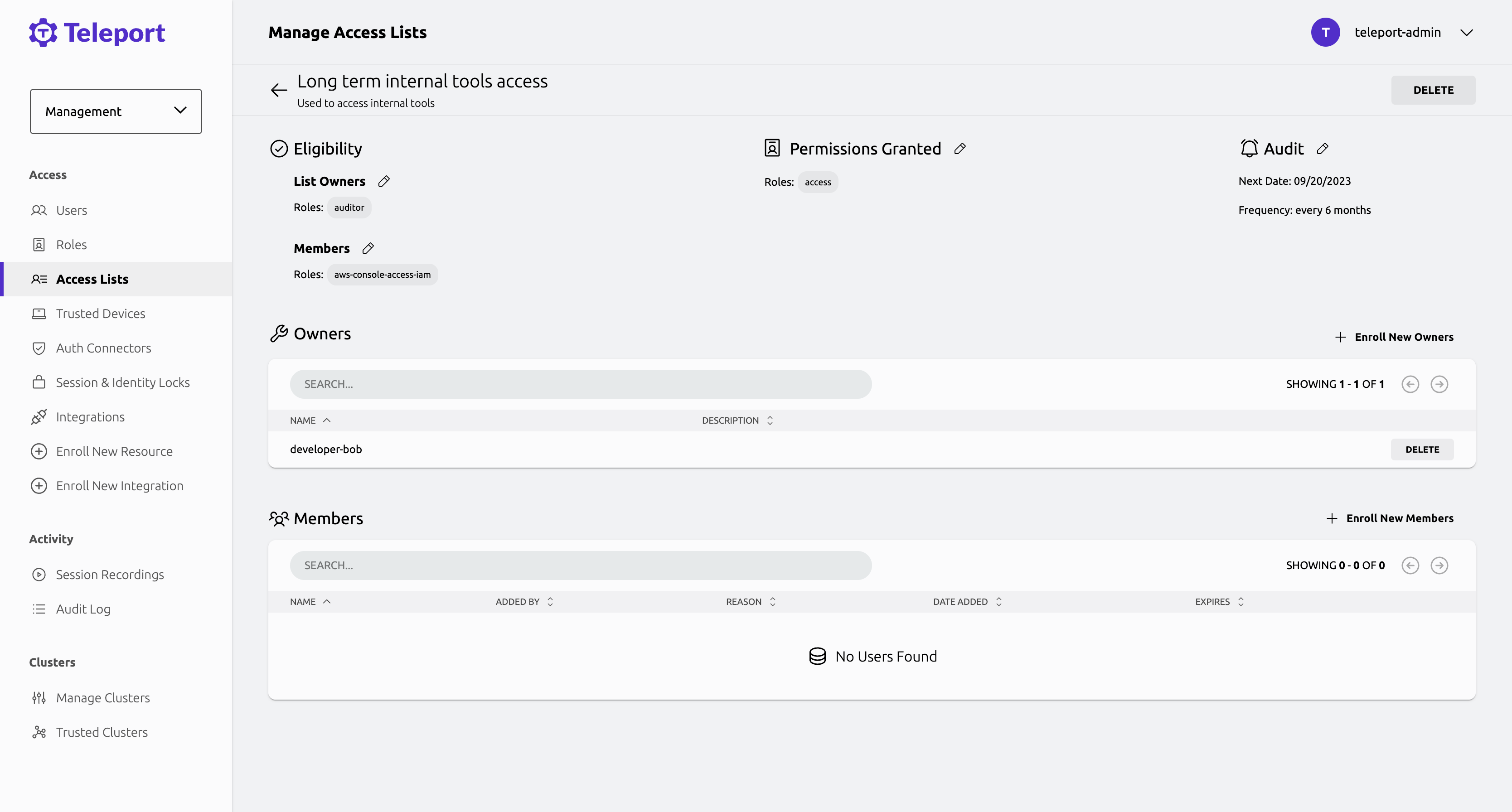

As the feature is being developed, future Teleport releases will add support for periodic audit reviews and deeper integration of access lists with Okta. This feature is available in Teleport Enterprise Edition.
You can find existing access lists documentation here: Access lists
Advanced audit log backend
Teleport 14 includes support for a new audit log powered by Amazon S3 and Athena that supports efficient searching, sorting, and filtering operations. Teleport Cloud customers will have their audit log automatically migrated to this new backend.
See the documentation here: Advanced audit log backend
Kubernetes Access
Kubernetes apps auto-discovery
Teleport 14 updates its auto-discovery capabilities with support for web applications in Kubernetes clusters. When connected to a Kubernetes cluster (or deployed as a Helm chart), Teleport discovery service will automatically find and enroll web applications for use with app access.
See documentation here: Kubernetes apps auto-discovery
Extended Kubernetes per-resource RBAC
Teleport 14 extends resource-based access requests to support more Kubernetes resources than just pods, including custom resources, and verbs. Note that this feature requires role version v7.
See Kubernetes resources documentation to see a full list of supported resources: Extended Kubernetes per-resource RBAC
Machine ID: Kubernetes Secret destination
In Teleport 14, tbot can now be configured to write artifacts such as credentials and configuration files directly to a Kubernetes secret rather than a directory on the local file system. This allows other services to more easily consume the credentials output by tbot .
For more information, see Machine ID: Kubernetes Secret destination
Database Access
ClickHouse support for database access
Teleport 14 adds database access support for ClickHouse HTTP and native (TCP) protocols. When using HTTP protocol, the user's query activity is captured in the Teleport audit log.
See how to connect ClickHouse to Teleport here: ClickHouse support for database access
Oracle database access audit logging support
In Teleport 14, database access for Oracle integration is updated with query audit logging support.
See documentation on how to configure it in the Oracle guide: Oracle database access audit logging support
Desktop Access
Limited passwordless access for local Windows users in OSS Teleport
In Teleport 14, access to Windows desktops with local Windows users has been extended to Community Edition. Teleport will permit users to register and connect to up to 5 desktops with local users without an enterprise license.
For more information on using Teleport with local Windows users, see Setup Desktop Access in Teleport Community Edition
TSH
Enhanced PuTTY Support
tsh on Windows now supports the tsh puttyconfig command, which can easily configure saved sessions inside the well-known PuTTY client to connect to Teleport SSH services.
For more information, see Enhanced PuTTY Support
Plugins & Misc
Discord and ServiceNow hosted plugins
Teleport 14 includes support for hosted Discord and ServiceNow plugins. Teleport Cloud users can configure Discord and ServiceNow integrations to receive access request notifications.
Support for TLS routing in Terraform deployment examples
The ha-autoscale-cluster and starter-cluster Terraform deployment examples now support a USE_TLS_ROUTING variable to enable TLS routing inside the deployed Teleport cluster.
Breaking changes and deprecations
Please familiarise yourself with the following potentially disruptive changes in Teleport 14 before upgrading.
SSH node open dial is no longer supported
Teleport 14 no longer allows connecting to OpenSSH servers not registered with the cluster. Follow the updated agentless OpenSSH integration guide to register your OpenSSH nodes in the cluster’s inventory: OpenSSH Guide
You can set TELEPORT_UNSTABLE_UNLISTED_AGENT_DIALING=yes environment variable on Teleport proxy to temporarily re-enable the open dial functionality. The environment variable will be removed in Teleport 15.
Proxy protocol default change
Starting from version 14, Teleport will require users to explicitly enable or disable PROXY protocol in their proxy_service/auth_service configuration using proxy_protocol: on|off option.
Users who run their proxies behind L4 load balancers with PROXY protocol enabled, should set proxy_protocol: on. Users who don’t run Teleport behind PROXY protocol enabled load balancers, should disable proxy_protocol: off explicitly for security reasons.
By default, Teleport will accept the PROXY line but will prevent connections with IP pinning enabled. IP pinning users will need to explicitly enable/disable proxy protocol like explained above.
See more details in our documentation: Proxy protocol
Legacy deb/rpm package repositories are deprecated
Starting from the next major release Teleport 15, legacy package repositories deb.releases.teleport.dev and rpm.releases.teleport.dev will stop receiving new releases.
All users are recommended to switch to apt.releases.teleport.dev and yum.releases.teleport.dev repositories: deb/rpm package repositories.
Cf-Access-Token header no longer included with app access requests
Starting from Teleport 14, Cf-Access-Token header containing signed JWT token will no longer be included by default with all app access requests. All requests will still include Teleport-JWT-Assertion containing the JWT token.
See documentation for details on how to inject the JWT token into any header using headers rewriting configuration: Injecting JWT headers.
tsh db CLI commands changes
In Teleport 14 tsh db sub-commands will attempt to select a default value for --db-user or --db-name flags if they are not provided by the user by examining their allowed db_users and db_names.
The flags --cert-file and --key-file for tsh proxy db command were also removed, in favor of the --tunnel flag that opens an authenticated local database proxy.
MongoDB versions prior to 3.6 are no longer supported
Teleport 14 includes an update to the MongoDB driver.
Due to the MongoDB team dropping support for servers prior to version 3.6 (which reached EOL on April 30, 2021), Teleport also will no longer be able to support these old server versions.
Symlinks for ~/.tsh/environment no longer supported
In order to strengthen the security in Teleport 14, file loading from home directories where the path includes a symlink is no longer allowed. The most common use case for this is loading environment variables from the ~/.tsh/environment file. This will still work normally as long as the path includes no symlinks.
Deprecated audit event
Teleport 14 deprecates the trusted_cluster_token.create audit event, replacing it with a new join_token.create event. The new event is emitted when any join token is created, whether it be for trusted clusters or other Teleport services.
Teleport 14 will emit both events when a trusted cluster join token is created. Starting in Teleport 15, the trusted_cluster_token.create event will no longer be emitted.
Other changes
v7 Roles
The default role version in Teleport 14 is v7, which enables support for extended Kubernetes per-resource RBAC, and changes the kubernetes_resources default to wildcard for a better getting started user experience.
You can review role versions in the documentation: Teleport Roles Versions.
DynamoDB billing mode defaults to on-demand
In Teleport 14, when creating new DynamoDB tables, Teleport will now create them with the billing mode set to pay_per_request instead of being set to provisioned mode.
The old behaviour can be restored by setting the billing_mode option in the storage configuration.
Stricter name validation for auto-discovered databases
In Teleport 14, database discovery via db_service config enforces the same name validation as for databases created via tctl, static config, and discovery_service.
As such, database names in AWS, GCP and Azure must start with a letter, contain only letters, digits, and hyphens and end with a letter or digit (no trailing hyphens).
Access Request API changes
Teleport 14 introduces a new and more secure API for submitting access requests. As a result, tsh users may be prompted to upgrade their clients before submitting an access request.
Desktop discovery name change
Desktops discovered via LDAP will have a short suffix appended to their name to ensure uniqueness. Users will notice duplicate desktops (with and without the suffix) for up to an hour after upgrading. Connectivity to desktops will not be affected, and the old record will naturally expire after 1 hour.
Machine ID: Config Change
Teleport 14 introduces a new configuration schema (v2) for Machine ID’s agent tbot. The new schema is designed to be simpler, more explicit and more extensible:
version: v2
onboarding:
token: gcp-bot
join_method: gcp
storage:
type: memory
auth_server: example.teleport.sh:443
outputs:
- type: identity
destination:
type: kubernetes_secret
name: my-secret
- type: kubernetes
kubernetes_cluster: my-cluster
destination:
type: directory
path: ./k8s
- type: database
service: my-postgres-service
database: postgres
username: postgres
destination:
type: directory
path: ./db
- type: application
app_name: my-app
destination:
type: directory
path: ./app
tbot will continue to support the v1 schema for several Teleport versions but it is recommended that you migrate to v2 as soon as possible to benefit from new Machine ID features.
For more details and guidance on how to upgrade to v2, see Upgrade to v2 Machine ID
Try Teleport 14 Today!
👉 Download Teleport 14 from our download page.
👉 Follow our product documentation to get started.
👉 Deep Dive with Teleport 14 Webinar.
👉 Join the Slack channel where Teleport users and developers hang out for community support.
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

