Home - Teleport Blog - Teleport Workload Identity
Teleport Workload Identity
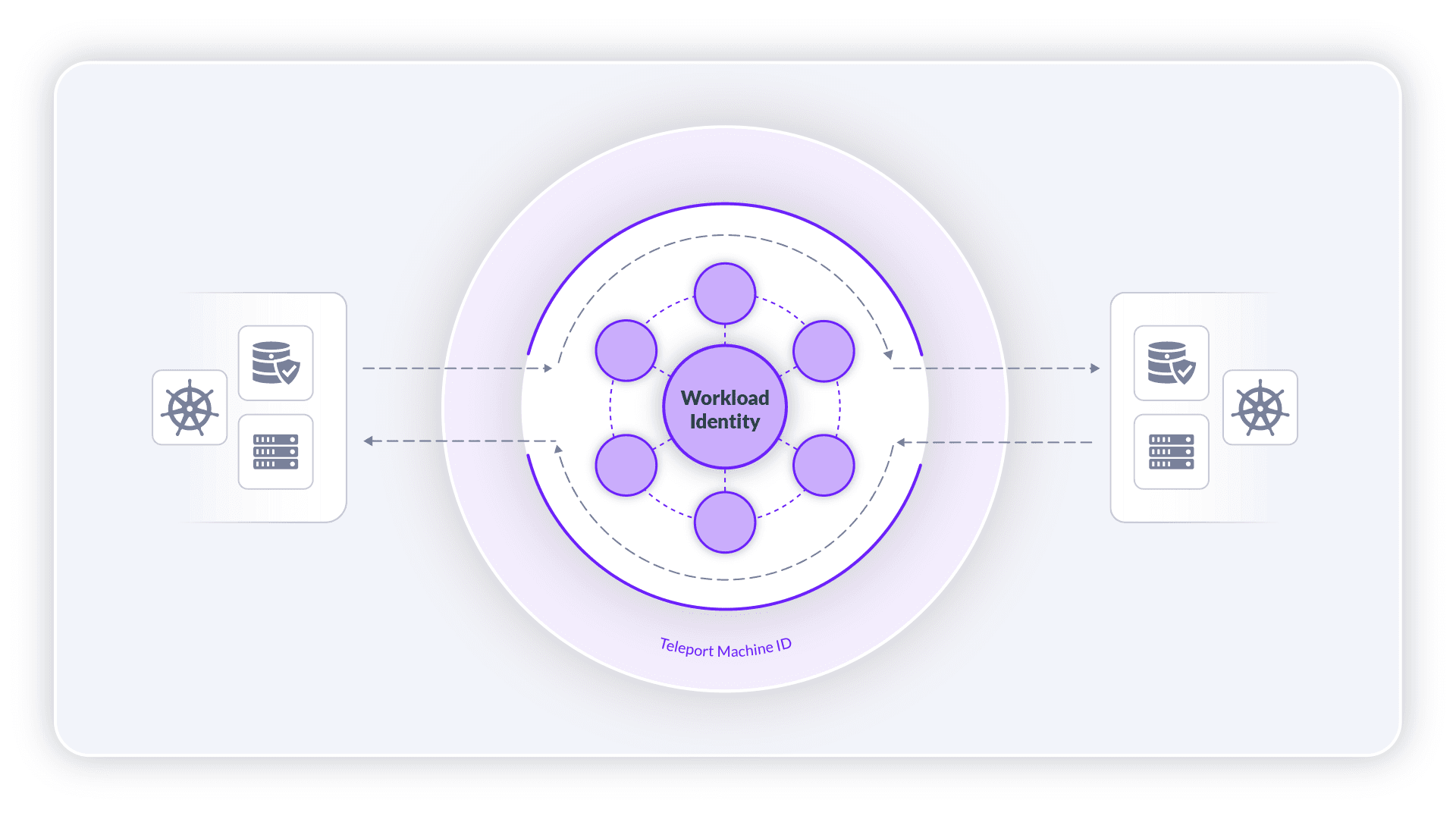
With Teleport 15.2, we’ve added a preview for Teleport Workload Identity. Teleport Workload Identity lets teams bootstrap and issue identities to services across heterogeneous environments and organizational boundaries.
A core value of Teleport comes from having a central access platform, and we believe that humans and machine access need to join and access using the same zero-trust best practices.
Building on top of SPIFFE, the Secure Production Identity Framework for Everyone, Teleport Workload Identity extends Teleport Machine ID with a SPIFFE workload API endpoint, the ability to issue SVIDs, new TPM server attestation* and support for AWS Roles Anywhere. These new additions let teams secure their workloads across clouds and organizations.
What is SPIFFE?
SPIFFE, the Secure Production Identity Framework for Everyone, is a framework and standard for identifying and securing communications between application services. SPIFFE does this by defining a standard for defending how services identify themselves to each other. This is done via SPIFFE IDs, and are implemented in a standard URL format. spiffe:// . Each SVID contains is a cryptographically verifiable document, called a SPIFFE Verifiable Identity Document. Lastly, SPIFFE offers a standard API for issuing and/or retrieving SVIDs.
SPIFFE is a graduated CNCF project, and if you want to understand the problem of providing uniform identity across modern infrastructure I would recommend reading the free PDF eBook Solving the Bottom Turtle. SPIFFE has been deployed at scale at growth companies such as Coinbase, Uber and Pinterest, among many others. For people familiar with SPIFFE, they will often use SPIRE. SPIRE is an implementation of SPIFFE principles. With this release, Teleport Machine ID is another implementation of the SPIFFE principles. Letting teams consolidate machine-to-machine communication using one tool. We believe Identity-Native Infrastructure Access Management is critical for all companies; by supporting SPIFFE we’re bringing a standard framework for providing identity management for machine-to-machines.
Key Use Cases for Teleport Workload Identity
There are multiple use cases for deploying a workload identity solution; once deployed, teams often don’t look back. A few key use cases are:
- Secure microservices communication with TLS & x509 PKI: When using Workload Identity applications can communicate using mTLS with X509 SVIDs over HTTP, improving security by ensuring mutual authentication, encryption, and fine-grained access control via SPIFFE SVIDs.
- Cross-service authentication for zero trust security model: As teams adopt a zero trust security network model, they’ll start to remove traditional authentication such as IP whitelists and account groups. Teleport Workload Identity can issue SVIDs that can be used by microservices, apps, and data pipelines to ensure consistent, secure communication across infrastructure.
- Build, bridge, and extend services across organizational boundaries: Large orgs often work within multiple regions, cloud accounts, and cloud providers. Teleport Workload Identity can work in all cloud environments, making it easy for teams to have a standard authentication and authorization framework for easily communicating across services.
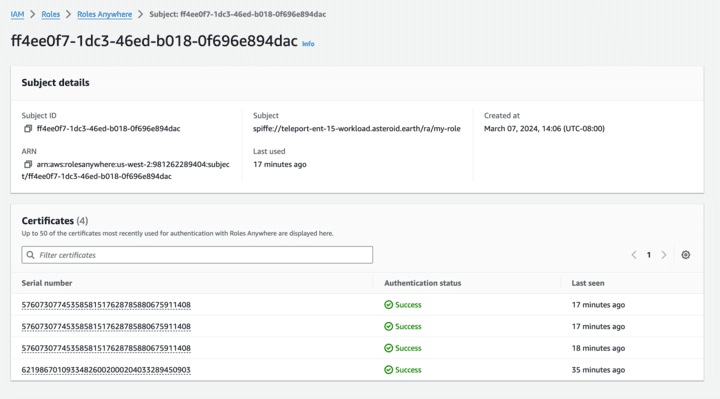
- Easy setup and maintenance for AWS Roles Anywhere: Roles Anywhere to let non-AWS services talk to AWS: Teleport Workload Identity can be used as a Trust anchor for Roles Anywhere, making it easy to connect to AWS services from non-AWS infrastructure.
- Streamlined Developer Productivity: Once a team deploys SPIFFE, it can be hard for Developers to debug services. Developers can now connect to Teleport Workload Identity protected services with a one time short lived SVID to connect.
- Simplified Identity Management: By consolidating machine identity into a centralized access platform, this allows for easier rollout, greater security and increased governance into the overall security of a system.
How Teleport Workload Identity Works
Teleport Workload Identity is an addition to Teleport Machine ID. Teleport Machine ID allows users to create bots, with unique join tokens, RBAC and config to obtain permissions. Once tbot, the Teleport Machine ID Agent, is deployed, it’ll join, obtain and auto-rotate credentials for us. tbot runs on a machine or in a container sidecar. Tbot has a new feature that allows it to store SVIDs on the filesystem, and serve them up via the SPIFFE workload API via a Unix socket. Applications can then leverage the TLS certs to secure endpoints. Teleport Workload Identity is compatible with all widely adopted spiffe libraries, such as go-spiffe, java-spiffe, python-spiffe, node-spiffe.
Diagram for Teleport Workload Identity
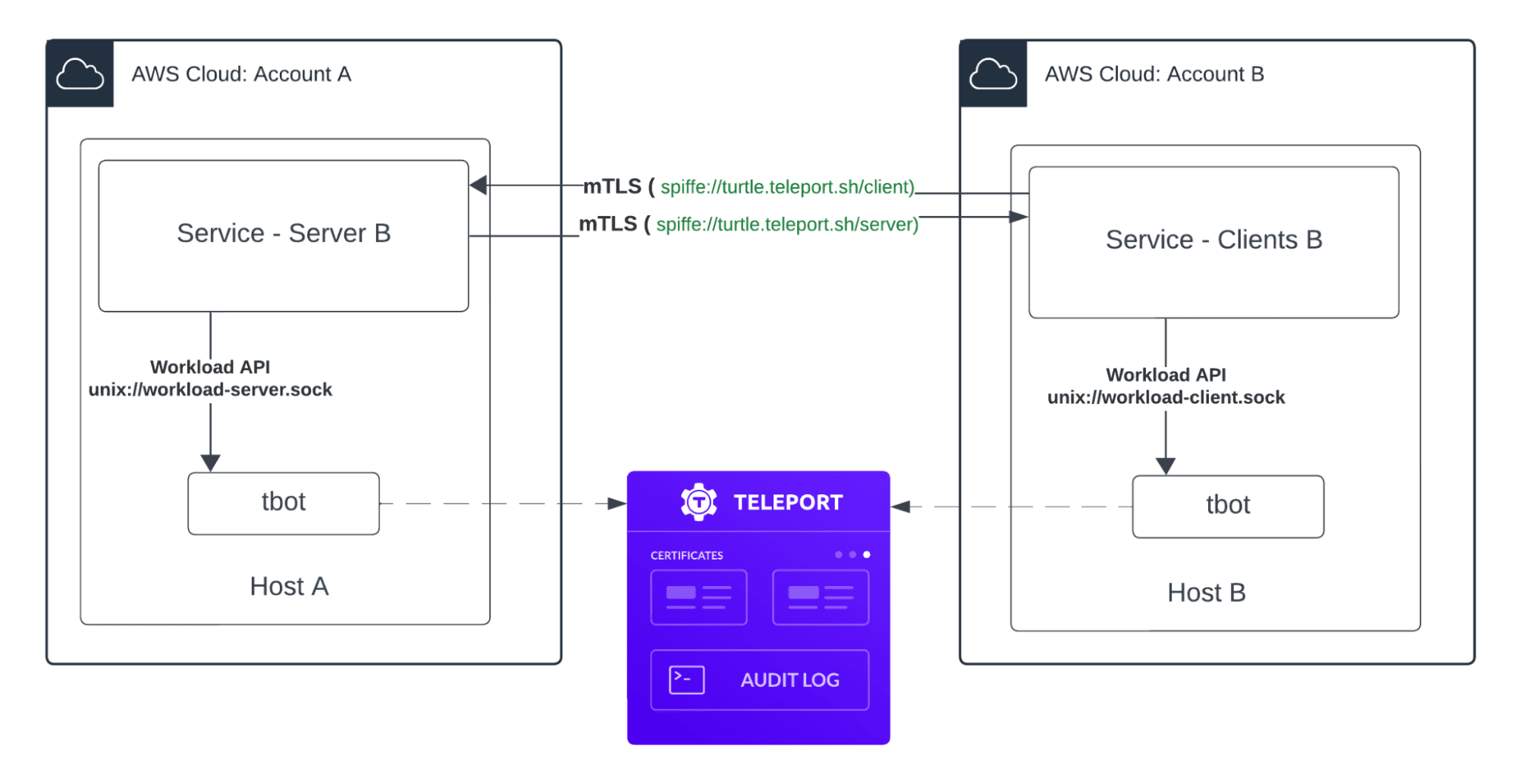

Example tbot Config for tbot running on Host A
The below yaml config highlights two config options, first is issuing SPIFFE SVIDs as an output and the 2nd is creating a unix endpoint that can be used to issue SVIDs.
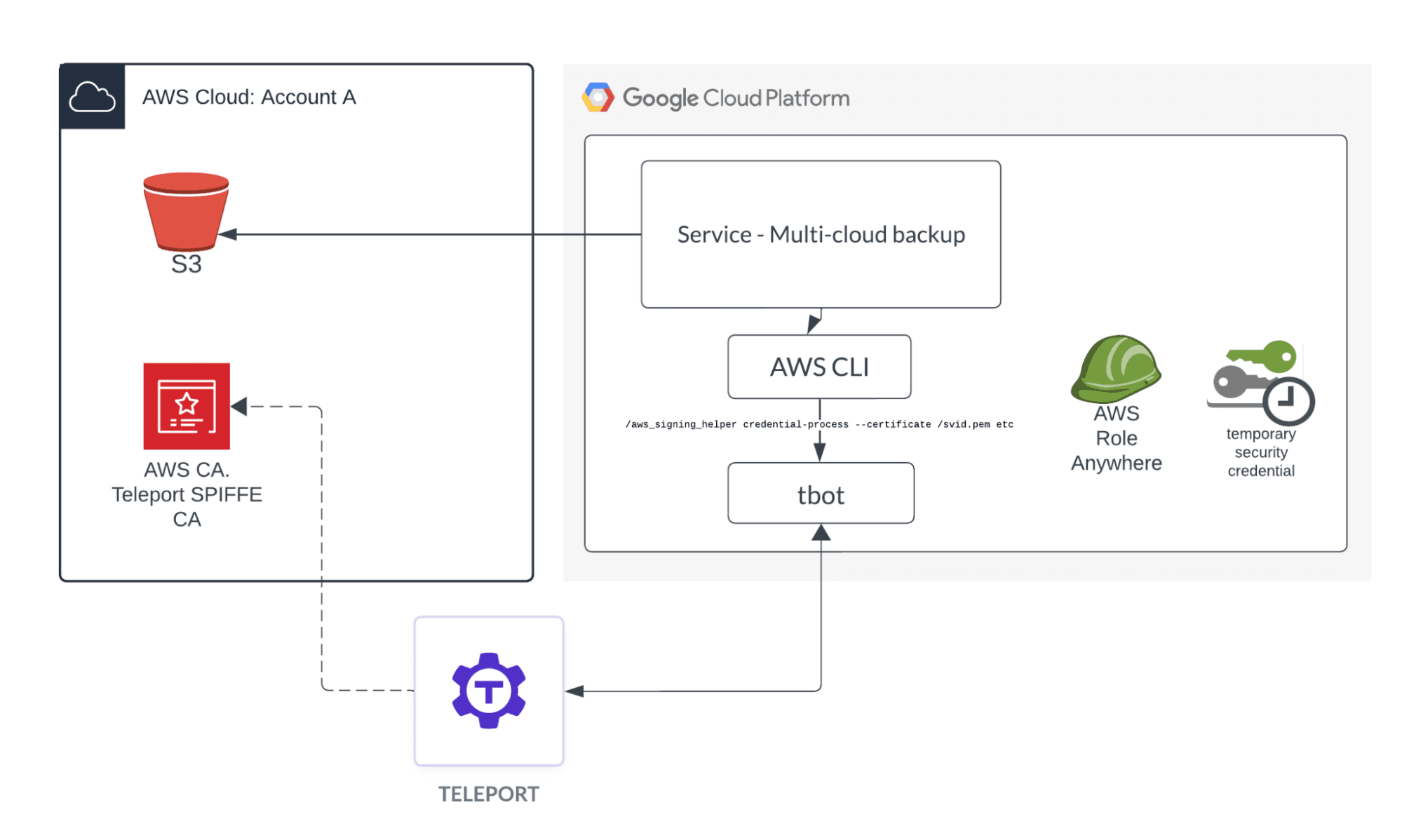
Diagram for Teleport Workload Identity with AWS Roles Anywhere
In the example below, we leverage AWS Roles Anywhere to connect to AWS resources without the need for long-term credentials. Teleport Workload Identity simplifies the setup by providing the Teleports Certificate Authority as the CA for the trust anchor. This also has the benefit of saving $400/month compared to using AWS Private CA.

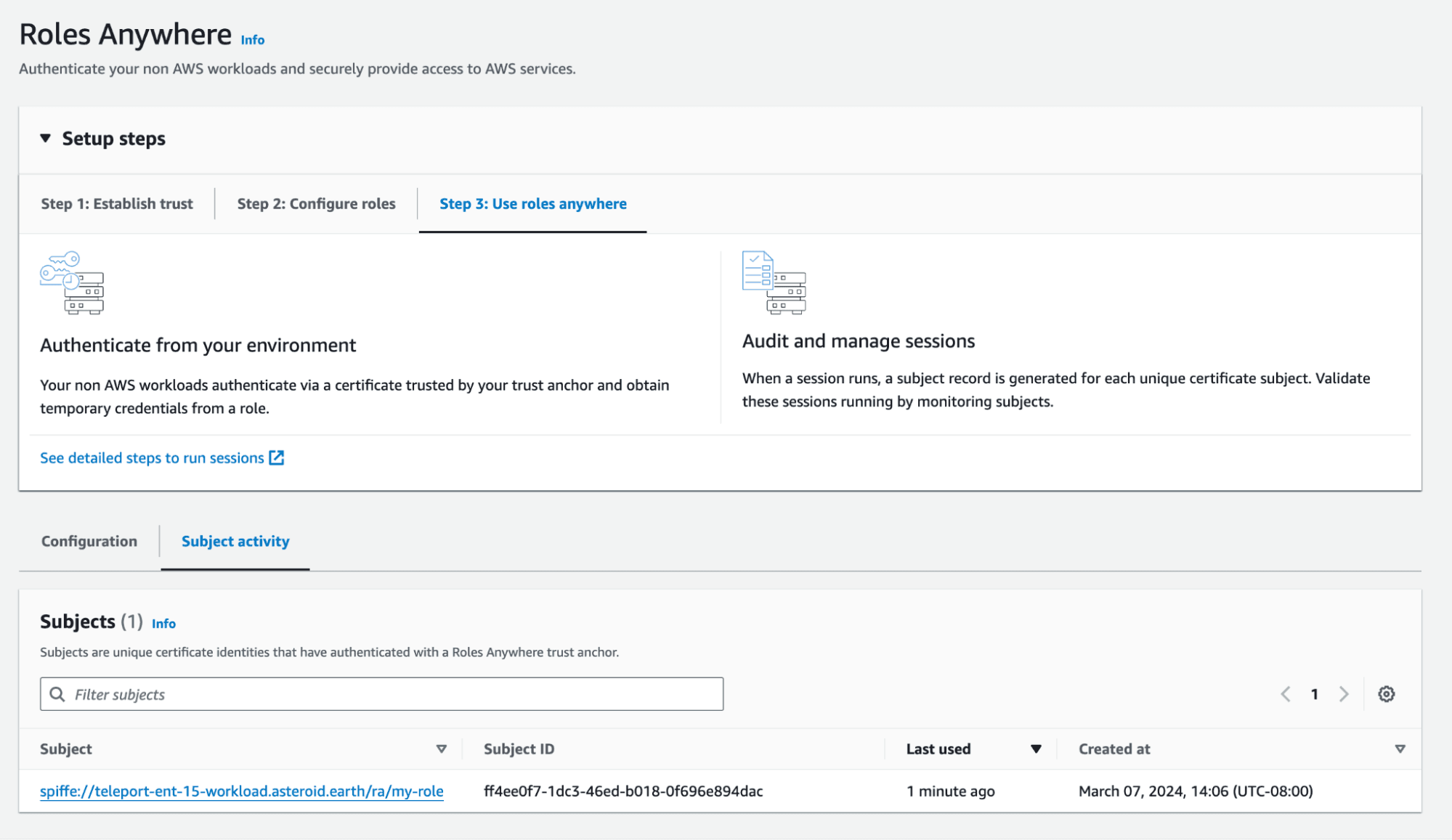
Example Roles Anywhere with Teleports SVID added to it’s subject. This allows for easier RBAC and permissions when deploying AWS roles anywhere.


Visibility into Workload Identity
Teleport can help teams adopt SPIFFE by providing easier tooling and visibility for the whole team. From infrastructure, developer, and security teams, the Teleport Platform offers a range of easy-to-use features to make adopting workload identity a breeze.
These are some features that’ll make adoption easier:
- Infrastructure: Infra teams can quickly deploy workload identity by leveraging tbot cloud join methods, along with our Terraform provider, to quickly scale the rollout.
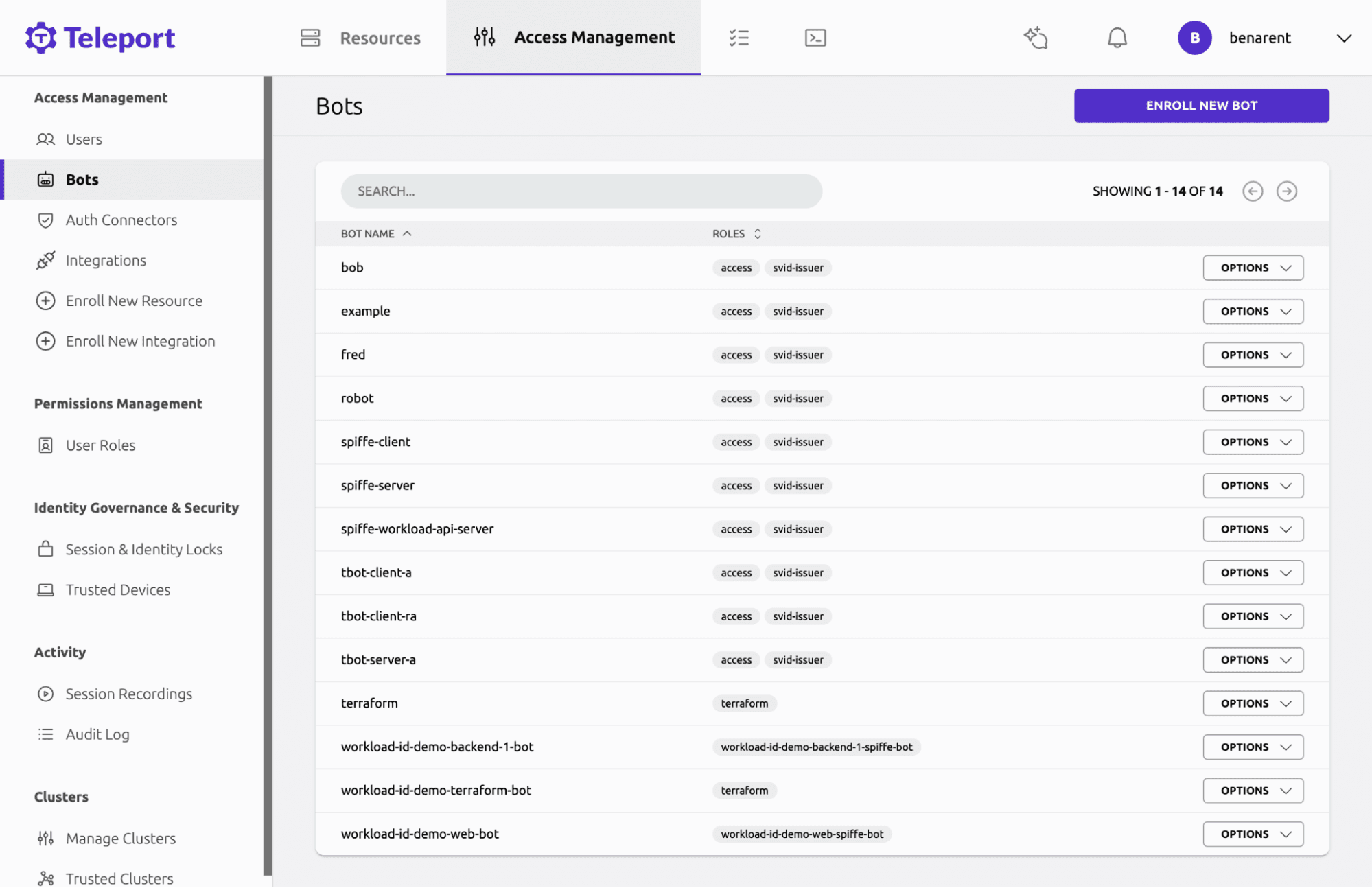
- Developers: When modifying an application to support workload identity, it’s critical to obtain the SVIDs the app requests. Developers can quickly find these out via the bot details page**.
- Security: Security teams can quickly lock bots, and rotate SPIFFE CAs in the event of a compromise. Access Monitoring supports Workload Identity so teams can see a breakdown of which SVIDs are being issued by which services.

Try Teleport Workload Identity
Teleport Workload Identity is now available in Teleport 15.2; read our documentation for how to get started or reach out to our team for more information.
Be a Workload Identity Pioneer
As with all preview features, we’re looking for feedback on how to improve Teleport Workload Identity. If you’re interested in being a design partner, please reach out to myself or fill in this form to be a part of our design partner program.
Join us for Workload ID Webinar
Join us for a webinar - Teleport Workload Identity with SPIFFE: Achieving Zero Trust in Modern Infrastructure on May 23rd, 2024, to learn more about Teleport Workload Identity.
* - tbot TPM Joining will be an Enterprise-only feature in an upcoming version of Teleport. This addition will make it easier for Machine ID and Workload Identity to work with non-cloud workloads.
** - tbot details page is expected later this year. If you’ve feedback on improving the UI for tbot please reach out to me. [email protected]
Table Of Contents
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.
Tags

Subscribe to our newsletter

