Home - Teleport Blog - Teleport 4.2 Released - Enhanced Session Recording, Workflows, and GCP - Jan 7, 2020
Teleport 4.2 Released - Enhanced Session Recording, Workflows, and GCP
Introducing Teleport 4.2
Teleport 4.2 delivers a strong foundation of new features. We have a full list of improvements and fixes attached to our Teleport 4.2.0 GitHub release. Below are a couple of the highlights:
-
Teleport now provides greater visibility into what's happening during a Teleport session with our Enhanced Session Recording.
-
We've also laid the groundwork for a world of possibilities with our enterprise-only Role Escalation via a Workflows API.
Read on for more details into how these foundational changes enhance Teleport's auditing capabilities and integrate with your existing workflows.
Enhanced Session Recording - Alpha Release
Teleport has offered session recording since it's inception and it still can blow people away to view detailed live recordings of sessions. Teleport 4.2 takes session recording to the next level with the ability to not only see the commands that are run but detailed information about the commands run, plus network connections and file activity. How detailed?
If you tried to audit...
echo Y3VybCBodHRwOi8vd3d3LmV4YW1wbGUuY29tCg== | base64 --decode | sh
What do you think is happening?
Apart from looking like gobbledygook, the user has base64 encoded something to obfuscate their command.
With Enhanced Session Recording you'll be able to see exactly what's happening when someone tries to do this during a session.
It turns out the user is running three commands, sh, base64 to decode the message, and curl which was hidden in the string which was base64 encoded.
The resulting output will is returned in Teleports Audit log.
{
"event": "session.command",
"path": "/bin/sh",
"program": "sh",
"argv": [],
"login": "centos",
"user": "jsmith"
}
{
"event": "session.command",
"path": "/bin/base64",
"program": "base64",
"argv": [
"--decode"
],
"login": "centos",
"user": "jsmith"
}
{
"event": "session.command",
"path": "/bin/curl",
"argv": [
"http://www.example.com"
],
"program": "curl",
"return_code": 0,
"login": "centos",
"user": "jsmith"
}
{
"event": "session.network",
"program": "curl",
"src_addr": "172.31.43.104",
"dst_addr": "93.184.216.34",
"dst_port": 80,
"login": "centos",
"user": "jsmith",
"version": 4
}
"_comment": "Extra log info has been removed for clarity",
From this Audit Log, it's now possible to know that the user ran curl http://www.example.com.
What else can this be used for?
-
Understand shell scripts. For example if a user uploads and executes a script, the commands run within the script are not captured, only the output is captured. With Enhanced Session Recording turned on, you'll be able to see any network requests and subsequent Linux commands which are run.
-
Terminal controls. Terminals support a wide variety of controls, including the ability for users to disable terminal echo. This is frequently used when requesting credentials. Disabling terminal echo allows commands to be run without being captured. This is fixed when Enhanced Session Recording is on, pleasing the most paranoid of CISOs.
Usually session recordings are unstructured, making them difficult to ingest and perform monitoring and alerting on. The Enhanced Session Recording's logs output and makes it easy to send session monitoring data to SIEM solutions or a centralized logging solution for alerting and monitoring.
What magic is this? 🔮
Teleport 4.2 has the ability to capture low-level Linux activity via the magic of Extended BPF. This method has been recently popularized by Brendan Gregg at Netflix for observability and he coined a BPF a ‘New Type of Software’. Many of these new features are available in 4.19 Linux Kernel.
To obtain this new superpower, we require a few things.
-
All Teleport components should be upgraded to 4.2. We recommend starting with the Auth Server.
-
Teleport Nodes with the
ssh_serviceenabled should be running the4.19 Linux Kernel or higher. For a list of compatible distros, see our docs. -
BCC tools should be compiled and built on the node. Follow instructions per distro here. We plan to use the packaged tools in future releases.
-
Enhanced Auditing should be turned on from within
teleport.yaml.# snippet from teleport.yaml ssh_service: enabled: yes enhanced_recording: enabled: true🎉 Success: It should be setup. Check
/var/lib/teleport/log/You can now easily alert and monitor on session activity.
👨🔬Coming Soon: We'll have the ability to replay and view the logs in the Teleport UI. Contact [email protected] for early access.
Visit our Enhanced Session Recording documentation to learn more.
Warning: This feature uses cutting edge software & kernels. Administrators should be comfortable with using new distros and patching kernels. In testing we've found small VMs can't build the supporting tools to compile BCC tools, it often requires 4G+ of RAM.
Role Escalation via a new Workflows API
Role Based Access Control is a cornerstone feature of Teleport Enterprise. It lets administrators define roles for users with a granular level of detail, allowing admins to apply the principle of least privilege. Sometimes the role you have isn’t enough.
Teleport 4.2 lets users request another role and provides a streamlined admin workflow to approve requests.
# User is requesting an escalated DBA Role.
$ tsh login teleport-cluster --request-roles=dba
Seeking request approval... (id: bc8ca931-fec9-4b15)
# Admins can use tctl to view role escalation requests.
$ tctl request ls
Token Requestor Metadata Created At (UTC) Status
------------------ --------- -------------- ------------------- -------
bc8ca931-fec9-4b15 alice roles=dba 07 Nov 19 19:38 UTC PENDING
## An admin can now approve or deny the request.
$ tctl request approve bc8ca931-fec9-4b15
We are currently working on integrations with Jira and Slack to provide approval workflows. If you have a tool we should integrate with, please mail it to [email protected]
Visit our Access Controls documentation to learn more.
High Availability Teleport on Google Cloud Platform
Thanks to an external contributor, gh:joshdurbin, Teleport can now be setup in a high availability mode on GCP using Google Firestore and Google Storage. We’ve outlined all of the components needed to run Teleport in HA mode in our new GCP Infrastructure Guide.
Other Updates
There are many other improvements, upgrades, and bug fixes in Teleport 4.2. For full details, visit the Teleport Github Release page
Teleport cybersecurity blog posts and tech news
Every other week we'll send a newsletter with the latest cybersecurity news and Teleport updates.
Upgrading
Minor versions are compatible within major releases, but we do recommend rolling out the upgrade across the whole fleet and updating
clients’ tsh libraries as you upgrade. We always recommend backing up your Auth Server and updating it first. Enterprise and Pro customers
should be sure to reach out to our support team if they run into any issues.
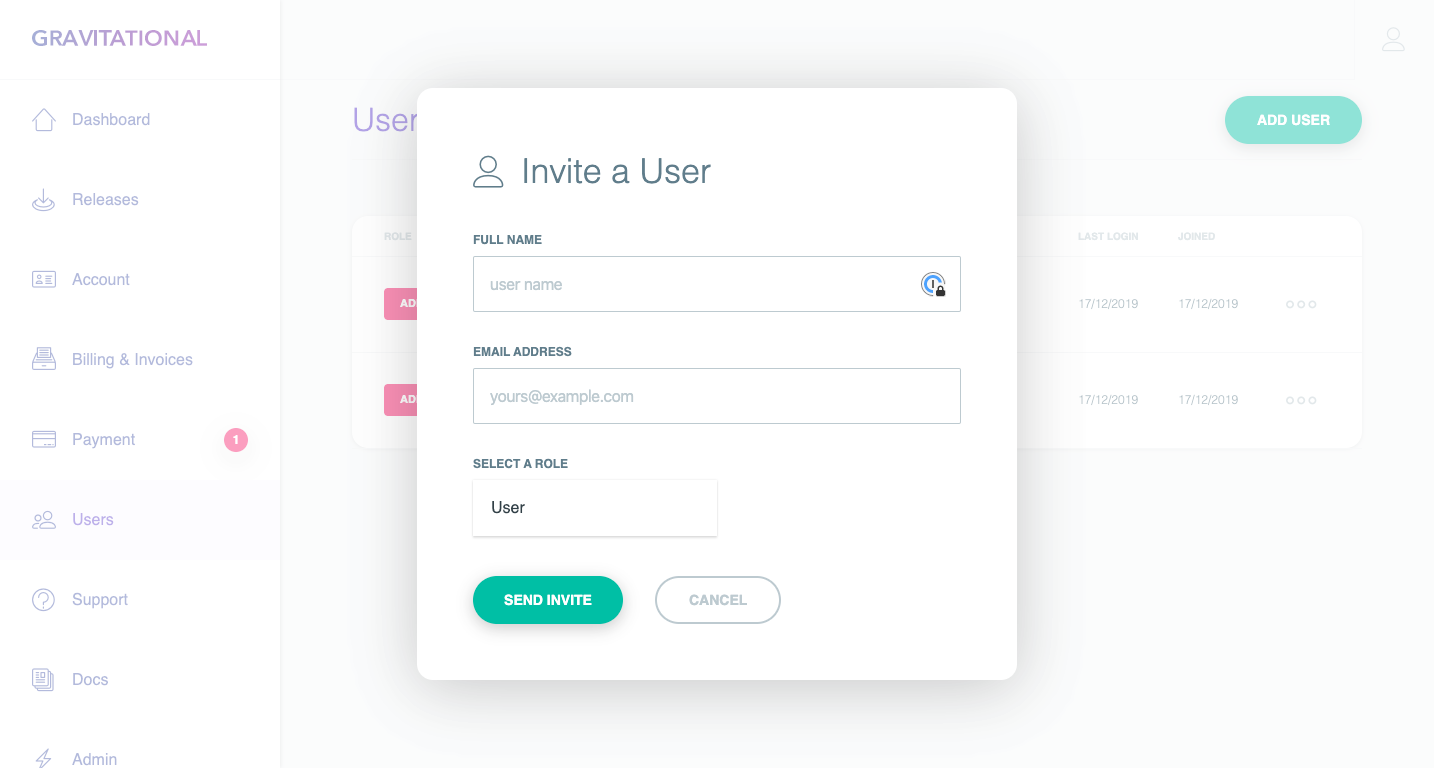
Bonus.. Invite the whole team to the Teleport Dashboard.
You can invite additional team members to the Teleport Dashboard. This can be helpful if you have different people in the organization rolling out Teleport and who require access to the Teleport License or to invite Milton from Accounting.

Try it now.
Download the latest packages from the Teleport Dashboard or if you are an OSS user, you can download from the Teleport Download page.
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

