Home - Teleport Blog - Teleport Starts Issuing CVEs - Feb 13, 2024
Teleport Starts Issuing CVEs
Teleport is an open source company. We develop in the open, including full disclosure of security issues in our changelogs and pull requests. We share our penetration tests and key compliance reports. Despite this, our communication to open source users and integration with automated security tooling needed improvement. We needed a standardized way to refer to our vulnerabilities so that when two people (or systems) talk about a vulnerability, they know they’re talking about the same thing. Fortunately for us, the CVE Program has the answer: Common Vulnerabilities and Exposures (CVEs).
Introducing CVE issuance by Teleport
Teleport has been authorized by the CVE Program as a CVE Numbering Authority (CNA). Dejargon-izing: Teleport can now publish a unique name/identifier to refer to Teleport security issues to the standard database. Security tools will automatically pick up these vulnerability names and notify users about the risk. Users can query these CVEs on cve.org and know exactly which Teleport versions the vulnerabilities impact and which versions are fixed.
Issuing Teleport CVEs is a collaboration between the CVE Program and the Teleport security team. The CVE database's broad monitoring and utilization make it an indispensable resource for vulnerability tracking, and we're perpetually grateful for the CVE Program’s role in managing this database.
Teleport will issue CVEs for critical and high severity findings. At this time, we do not plan to issue CVEs for medium, low, and informational security findings. We exclude lower severity findings to focus on security issues that substantially improve Teleport and to cut down on alert fatigue.
If you’re responsible for upgrading Teleport clusters and suffering from alert/upgrade fatigue, we recommend putting security updates on autopilot with Teleport Automatic Upgrades. If, on the other hand, you’re looking for a way to get more alerts about Teleport vulnerabilities, we have a second announcement.
Launching GitHub Security Advisories
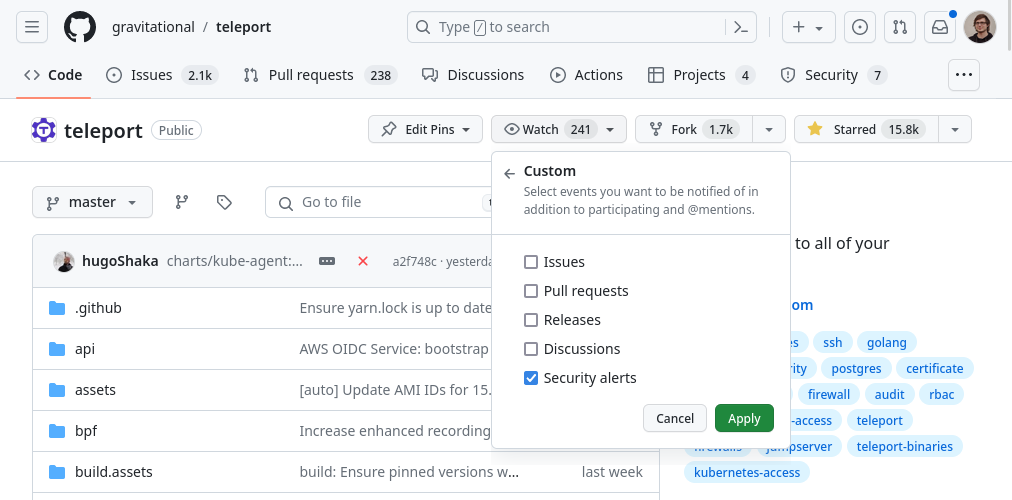
Teleport now publishes CVE-worthy vulnerabilities to GitHub's Security Advisories. To receive these direct notifications from GitHub, please watch our Teleport repository. Because the repository is quite busy with development activity, we recommend using the "Custom" watch setting to specifically select "Security alerts" or add “Releases” if you want to know about all releases.

What isn’t changing
All paying customers will continue to receive direct, private, security notices for critical and high severity issues prior to any public disclosure. Additionally, our cloud customers can trust that Teleport Cloud will be fully patched prior to public disclosure.
CVE and GitHub security advisories are published shortly after a fully patched open source release is available and our security embargo lifts.
Looking forward
Issuing CVEs and GitHub Advisories represents significant strides in our ongoing commitment to security transparency. We hope this streamlines the notification process for security updates! If you want to talk to our security team directly, please join the #security channel in our community Slack.
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

