Table Of Contents
Home - Teleport Blog - On terminals and sessions - Apr 29, 2022
On terminals and sessions
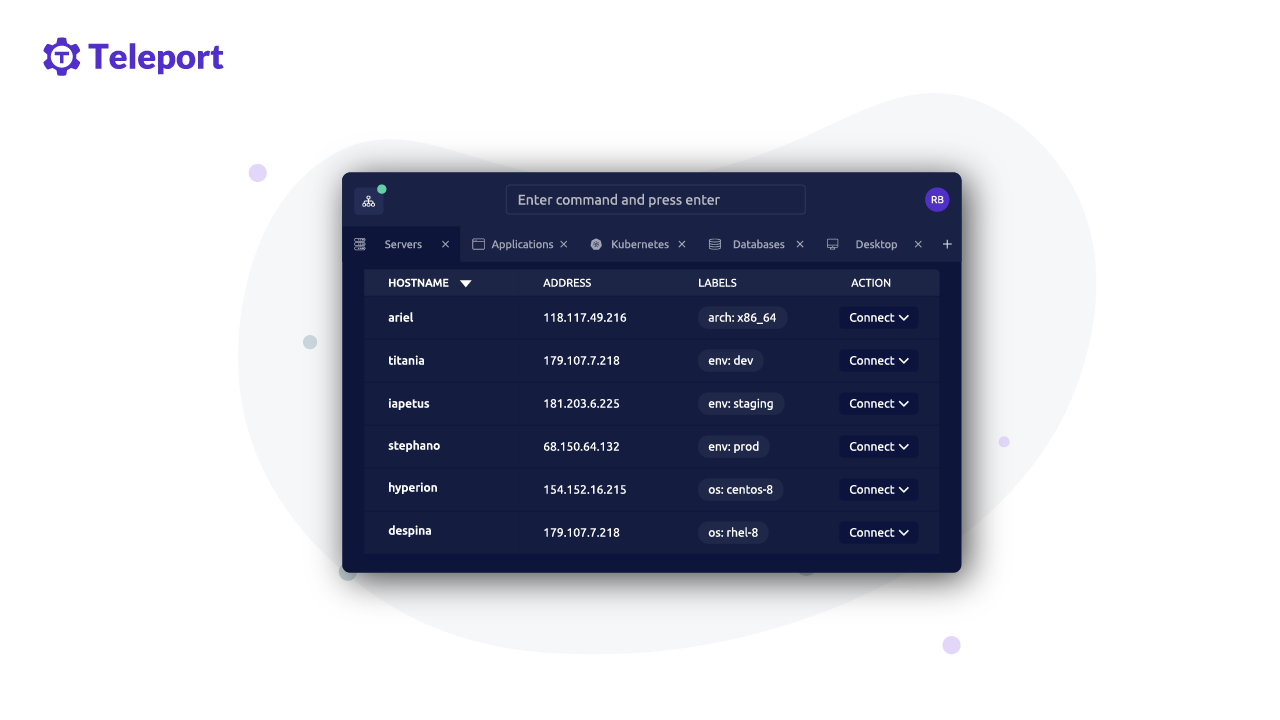
In this post I will be announcing a new open source project: Teleport Connect. It is a dedicated secure web browser for accessing cloud infrastructure.
But first, let me explain why we've decided to build it, starting with a bit of historical context. As a kid I have always enjoyed imagining the process of programming to having a conversation with a machine.
- Computer, would you please do this [type some code]
- Do it now! [hit enter]
- [see results]
The REPL loop is the most obvious example of this interaction. As our code grows it no longer fits in a REPL environment. We store it in a separate file which we can execute, evaluate, edit again, so the “conversation” with a computer continues.
That conversation often takes place in a terminal window. We even ported a common English word into the tech lexicon to describe what's going on: a session. A terminal is a container for a session, a place where the state is stored like the current directory, the cursor position, or the size of a terminal window.
A session also keeps your identity, as evidenced by typing who am I in the bash prompt.
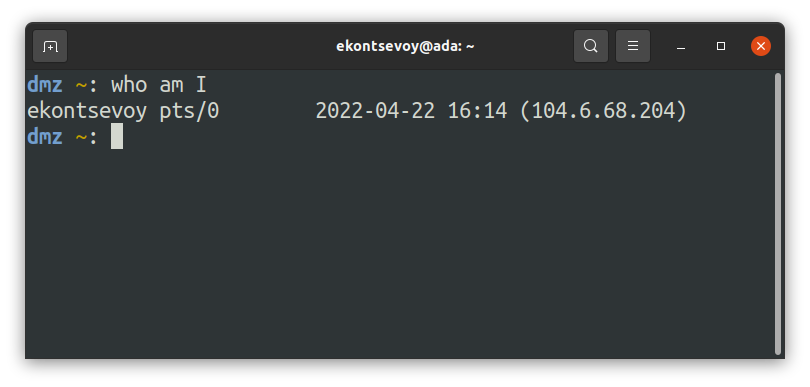

The identity is easy to take for granted, but it's important. When you launch programs during the session, they trust you. They already know who you are. Your identity is managed by the session manager of your OS, and is inherited by the programs you run as part of a session. Just imagine the horror of having programs like top, vi or emacs asking you to login every time you run them! Thank you, Ken Thompson and other co-creators of UNIX, for designing this neat concept of a user session!
Unfortunately, this elegance is largely lost when it comes to programming for the cloud. My code does not run on a single computer anymore, but in a computing environment consisting of numerous machines and other computing resources speaking different languages: from bash, and perl to SQL and kubectl. Moreover, it doesn't stop with command line tools only: there's Grafana, Jenkins, Netlify and other browser-native tools that represent parts and pieces of our computing environments.
There is no such thing as a “session to my AWS environment”. We must open numerous individual sessions for every resource we need: a database, a Linux box, Grafana, a Kubernetes cluster, Netlify, Jenkins, etc. The list is long. Our terminals and browsers are overloaded with tabs. There’s no common session and no common state between them. Not only is this inconvenient, but this leads to costly blunders. Ask around and you’ll hear variations of a story about someone accidentally running DROP TABLE in production because they were in the wrong tab.
A traditional terminal session will print you a list of programs you’ve started, but there is nothing like that for a cloud environment because there’s no common identity.
SSH, Kubernetes, MongoDB and Jenkins each require you to have an account. Our laptops are peppered with configuration files, private keys, API keys and browser cookies for establishing isolated sessions with cloud resources. This presents serious security implications. According to the Infrastructure Access Report conducted in 2021, over 80% of organizations cannot guarantee that their former engineers can no longer access their cloud environments! That’s because cloud environments have no common “session manager” to deprovision access to everything in one place.
We’ve lost plenty of convenience and security by moving from single-machine to computing environments, but we believe it’s time to start reclaiming some of that back.
Let’s start with a single source of identity that can synchronize access to Linux servers, Windows desktops, databases or any other resource. To do this, we need a modern “session manager” equivalent that natively supports authentication, authorization and audit across platforms, cloud providers and protocols. This will bring CLI-based workloads like SSH and HTTP-based protocols like the Kubernetes API or web apps under the same identity realm. After a single login all “cloud” commands like ssh, kubectl, psql, as well as browser sessions to internal web apps will inherit your identity.
The open source project called Teleport does exactly that, by issuing a portable identity for engineers that works across these resources. In 3 short years Teleport has earned the trust of companies like Square, NASDAQ, DoorDash, Elastic, Snowflake, Zynga, Epic Games and others. Turns out, it’s quite valuable to have a single source of truth for who can access what.
But engineers still end up with their terminals and browsers overloaded with tabs. The overall experience of accessing infrastructure with Teleport is still similar to having a dozen unrelated sessions instead of having a single session with a computing environment. There’s only so much we could have done on the infrastructure side.
This changes now. With the latest release of Teleport 9 we are introducing Teleport Connect, a downloadable, open source desktop application which can be used to establish a single session to your entire computing environment. Teleport Connect requires Teleport to be deployed on your infrastructure.
Teleport Connect relies on a hybrid user interface consisting of the command line and a web browser. Here’s what you can do with it:
- It all starts with a single login, paired with industry best practices such as SSO, MFA and a completely secretless/keyless/passwordless security model. Teleport only works with automatically expiring certificates.
- Once inside, you will see a list of computing resources available to you. You will see SSH servers, Windows hosts, Kubernetes clusters, internal web-based tooling such as monitoring dashboards, databases — basically everything you need to get things done.
- When interacting with these computing resources, your identity will be natively passed through into these resources, so your credentials and permissions are always taken care of.
- Your global session state will be preserved, as you switch from one environment to another.
- If you have other tools installed on your laptop, they will work too: Teleport Connect automatically reconfigures your local environment, providing connection bridging, automatic client configuration for commands like
ssh,psql, etc.
While Teleport itself has been production-ready and battle-tested at some of the world’s best tech companies, Teleport Connect is a brand new app. The first release only works with a fraction of protocols supported by Teleport: SSH, MySQL, MongoDB, and PostgreSQL. We expect to be adding new protocols rapidly in each subsequent release. The next iterations will include Kubernetes, and support for web-based applications, think Grafana or any other web-based tools you have running on your VPC/LAN behind firewalls.
Teleport Connect demo
For now, take a look at this quick demo and hopefully you’ll see the direction this project is going in. With Teleport Connect, we are trying to make interacting with cloud environments as simple as interacting with a single machine.
Try Teleport Connect for free
Teleport is open source, which makes it easy to take Teleport Connect for a spin:
- Download and install Teleport on your infrastructure. If you are impatient, you can sign up for a free cloud edition for a limited time.
- Install Teleport Connect on your laptop.
- Add your computing resources (SSH servers or Databases) to it.
- Enjoy!
- Join our community Slack to chat with Teleport developers and other Teleport users.
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

