Home - Teleport Blog - Passkeys for Infrastructure - Jan 12, 2023
Passkeys for Infrastructure

I predict that 2023 will be the year of Passkeys.
Passkeys are a new passwordless authentication method allowing users to create online accounts and sign in without entering a password. Passkeys have been years in the making and finally, industry fido alliance collaboration (fido2) and the adoption between Apple, Microsoft, and Google have now made it a reality.
Passkeys leverage the WebAuthn API to let users log into various websites and applications. At Teleport, we’ve always been strong advocates for providing the best security for our users. As part of adding WebAuthn and passwordless with Teleport 10, we laid the foundation for passkey support once rolled out in iOS 16, Ventura, and Windows 11.
To understand how passkeys work, it’s important to understand how passwordless works, but there are a few specific passkey quirks necessary to their functionality. Instead of going at length, the easiest way to explain is to show passkeys in action.
There are a few differences for passkey support vs traditional passwordless. The first difference is the ability to login across platforms and browsers. Prior to passkeys, if someone was to enroll Touch ID as a passwordless authentication method, they could only log in using that same Mac. If they wanted to switch to Windows or log into a mobile device, they would need to enroll in that device.
Passkeys come into their own when using a mobile device. When a passkey is stored in the cloud, but backed by the secure enclave on the phone, there are some features that make Passkeys phish-proof. Part of FIDO2 protocol requires a proximity proof.
When a QR code is scanned, passkeys include proximity proof. This means that the client has a local Bluetooth beacon, providing a strong claim the two devices are within proximity. This means a remote hacker isn’t able to phish without getting physical access to the device and the biometrics to log into it.
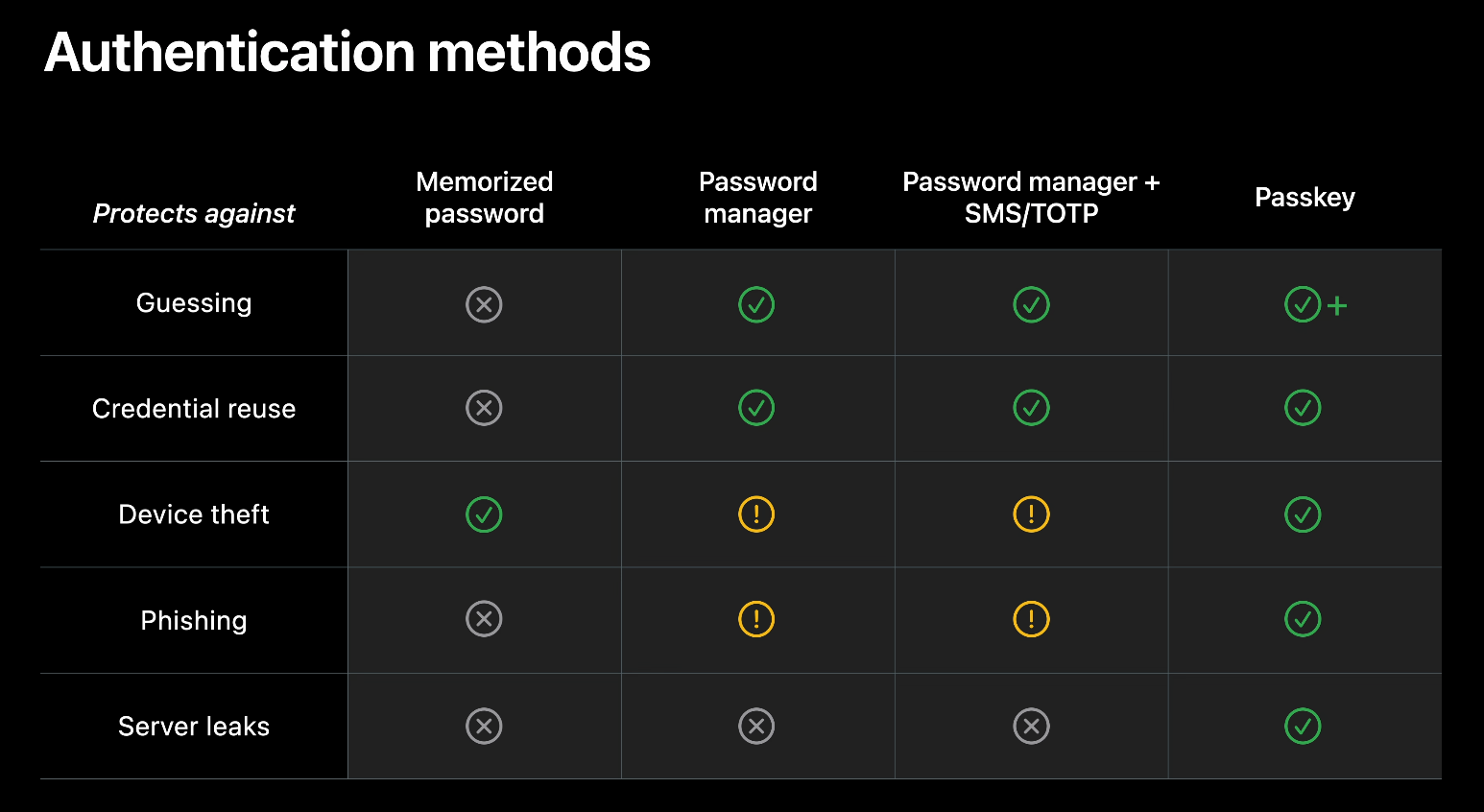
With all of the features combined, it’s important to understand that passkeys also remove the need for 2FA. This is possible because passkeys combine multiple verification factors into one. Combining presence (Bluetooth beacon), possession (private key on secure enclave) and user verification (passkey verified by FaceID), Apple has a good video introducing passkeys. This diagram is a good explanation of how these different authentication methods stack up.

Example passkey UI: Chrome and Safari.
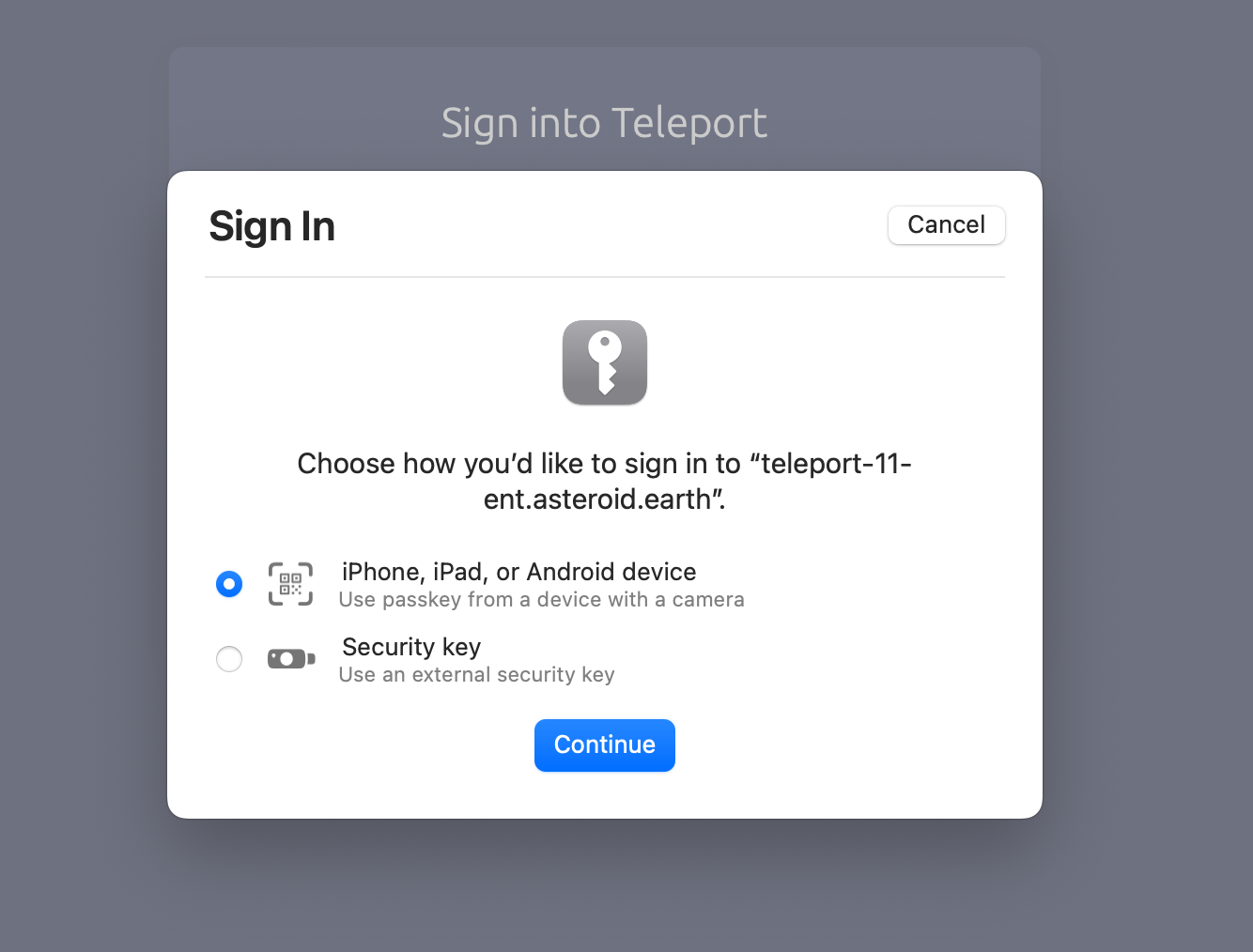

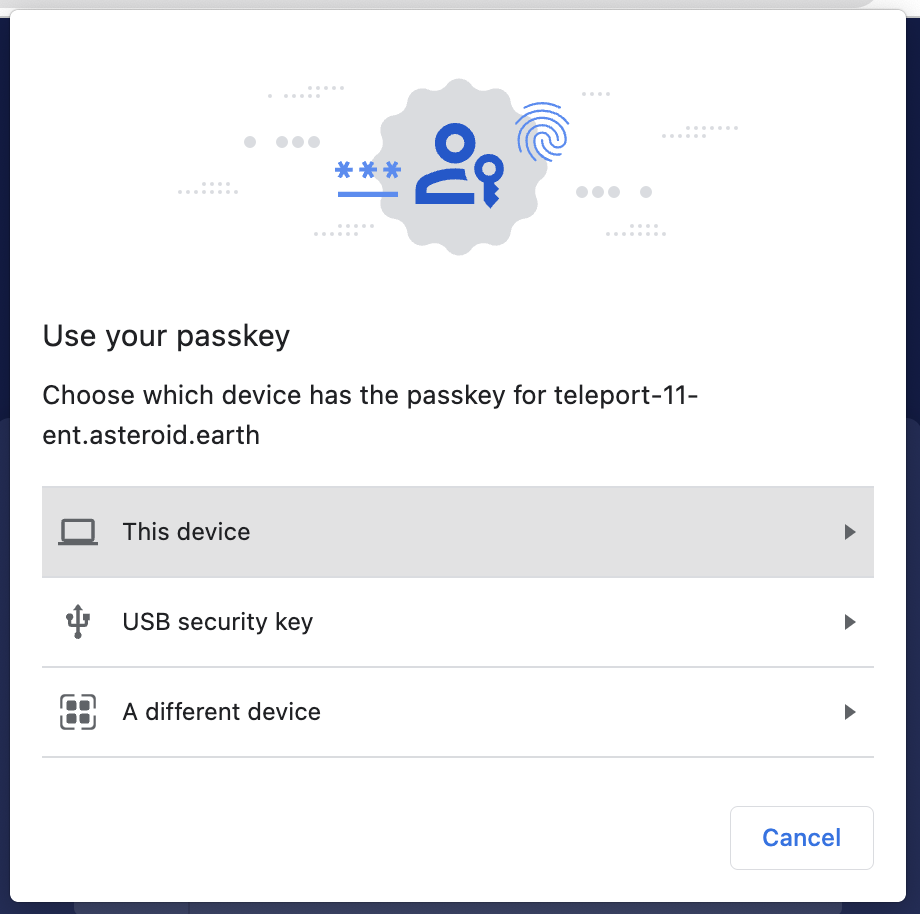

Once I’ve enrolled my iPhone or Android, it stores the passkey for future use, making it very easy to switch access between devices. Passkeys are synced across devices and stored in the cloud, using iCloud keychain or Google Password Manager .This has the added benefit of being a strong 2nd factor, without the need for OTP apps such as Google Authenticator or Authy.
Passkeys are supported with Teleport 10 and 11; the one limit is that passkeys aren't supported within the terminal for tsh; however, passwordless is supported. For this, we would recommend using a USB Security key, such as a Yubikey. Passkeys also don’t currently work with Firefox.
Why use Passkeys for infrastructure?
You might wonder why passkeys are important for accessing infrastructure. Over the past year, we’ve started to see cracks within SSO + MFA providers. For example Madiant noted MFA and push fatigue, leading to attackers getting a foothold into a system.
Many MFA providers allow for users to accept a phone app push notification or to receive a phone call and press a key as a second factor. The threat actor took advantage of this and issued multiple MFA requests to the end user’s legitimate device until the user accepted the authentication, allowing the threat actor to eventually gain access to the account.
Attacks on Okta during 2022 have shown the importance of rolling out MFA security keys and not allowing for SMS-based 2FA.
But why use passkeys and passwordless? Passkeys bring a wider flexibility and convenience compared to previous passwordless deployments. Prior to passkeys, a user would have to register devices independently and if the initial registration was performed using TouchID it was difficult to register another computer or operating system. By registering a hardware token, it made it possible to easily login on different devices but requires carrying an extra token all the time. After registering a phone as a device, it’s a much more convenient and equally secure way to log in and access Teleport.
How to set up Passkeys with Teleport.
To use passkeys with Teleport, you’ll need to:
- Enable WebAuthN within Teleport.
- Enroll a device, it could be TouchID or a YubiKey.
- Add a 2nd two-factor device: https://teleport.example.com/web/account/twofactor
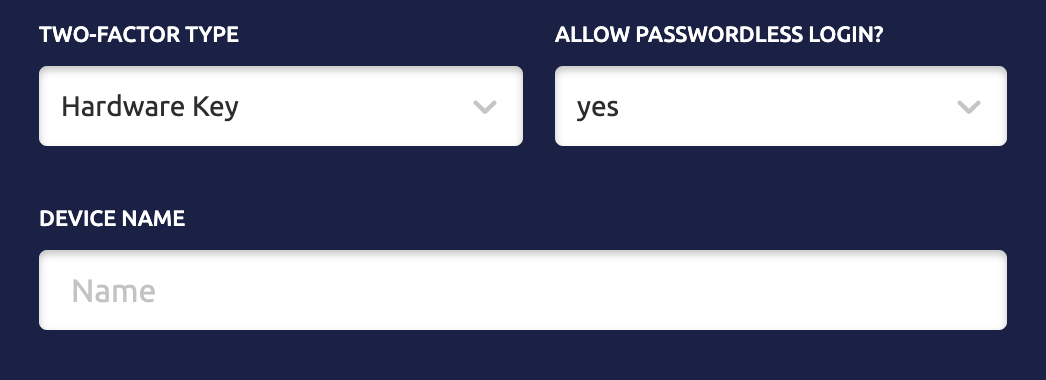

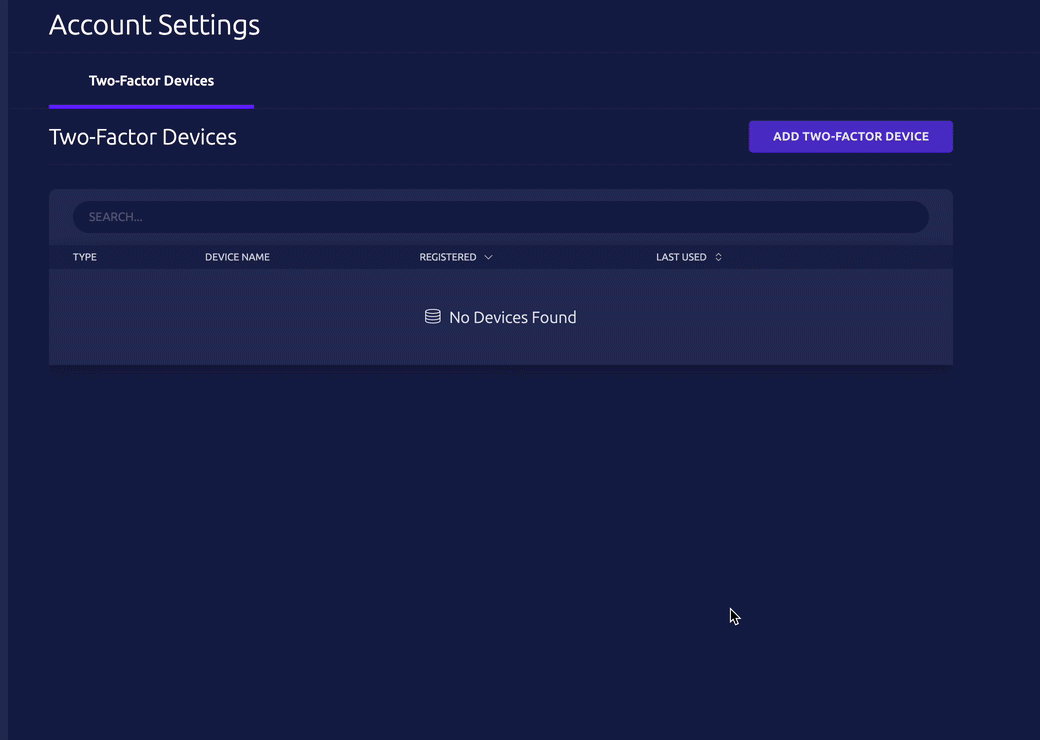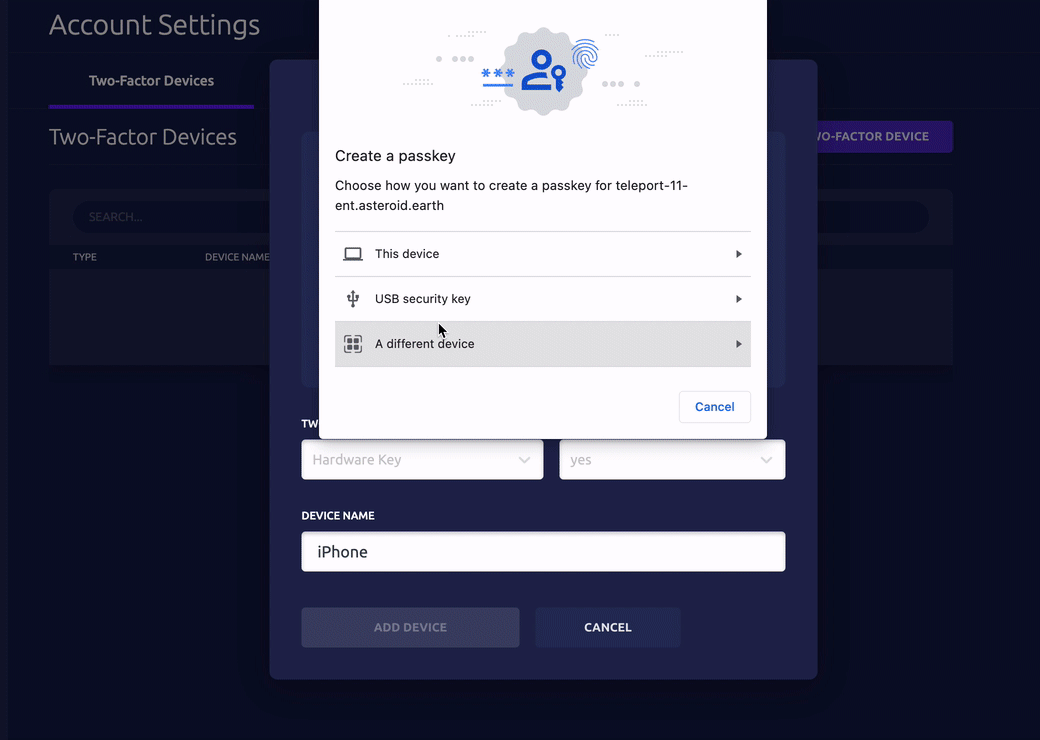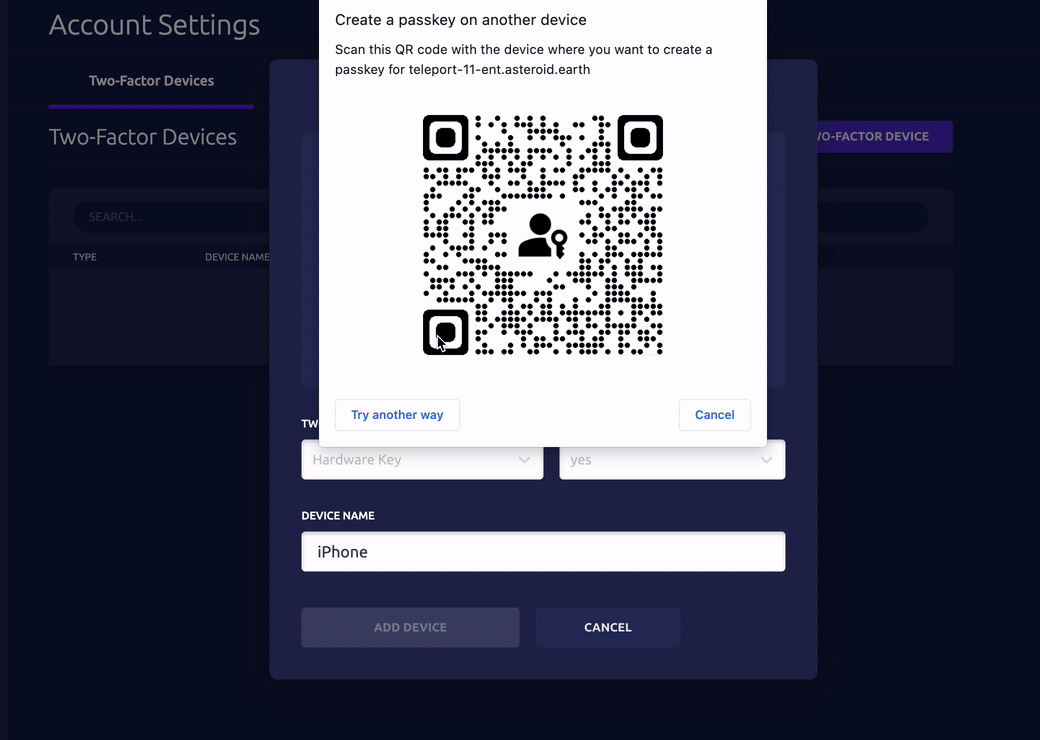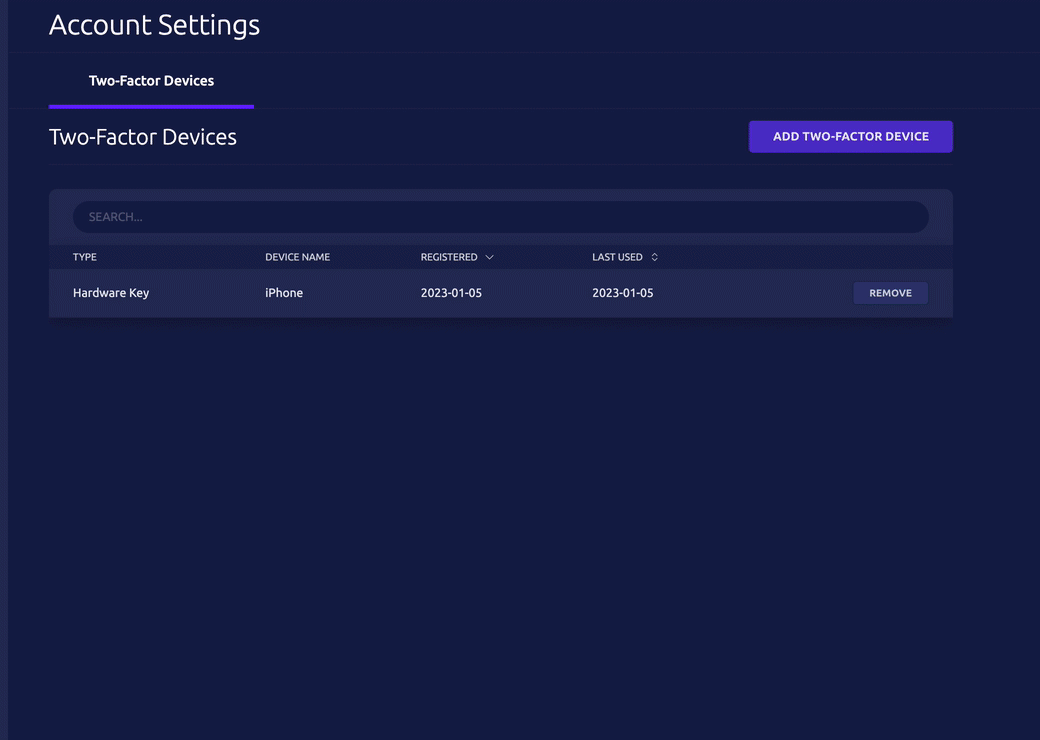
- To enroll an iPhone, select Hardware Key, and allow Passwordless. Scan the QR code with your device.

Passwordless and Passkeys are available in both Enterprise and Community editions of Teleport. Are you planning to adopt them?
We would love to know; join our Slack channel to let us know.
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

