Home - Teleport Blog - New Features in Teleport Identity Security provide more insight into infrastructure policy risks
New Features in Teleport Identity Security provide more insight into infrastructure policy risks
New Features in Teleport Identity Security 16
As modern organizations grow in size and complexity, managing secure access to computing infrastructure becomes a top priority. Teleport has introduced new features in Teleport Identity Security 16 aimed at making this easier and more efficient. With these enhancements, organizations can take a more proactive approach to security, ensuring better oversight and reducing potential risks.
Teleport Policy unifies the management of access policies across computing infrastructure for all types of identities: human, machine, and computing resources like Kubernetes, databases, and services.
Teleport Identity Security enables you to view access paths and uncover risky access patterns in seconds, and provides fine-grained oversight of privileges and access policies across hybrid infrastructure.
Questions that Teleport Identity Security can quickly answer:
- Who has access to a specific infrastructure resource or data?
- Which infrastructure resources does a specific user have access to?
- Are there indirect paths that give a particular user access to a resource?
- How did a particular user gain access to a particular resource?
Below are the key new features introduced in the latest update to Teleport Policy.
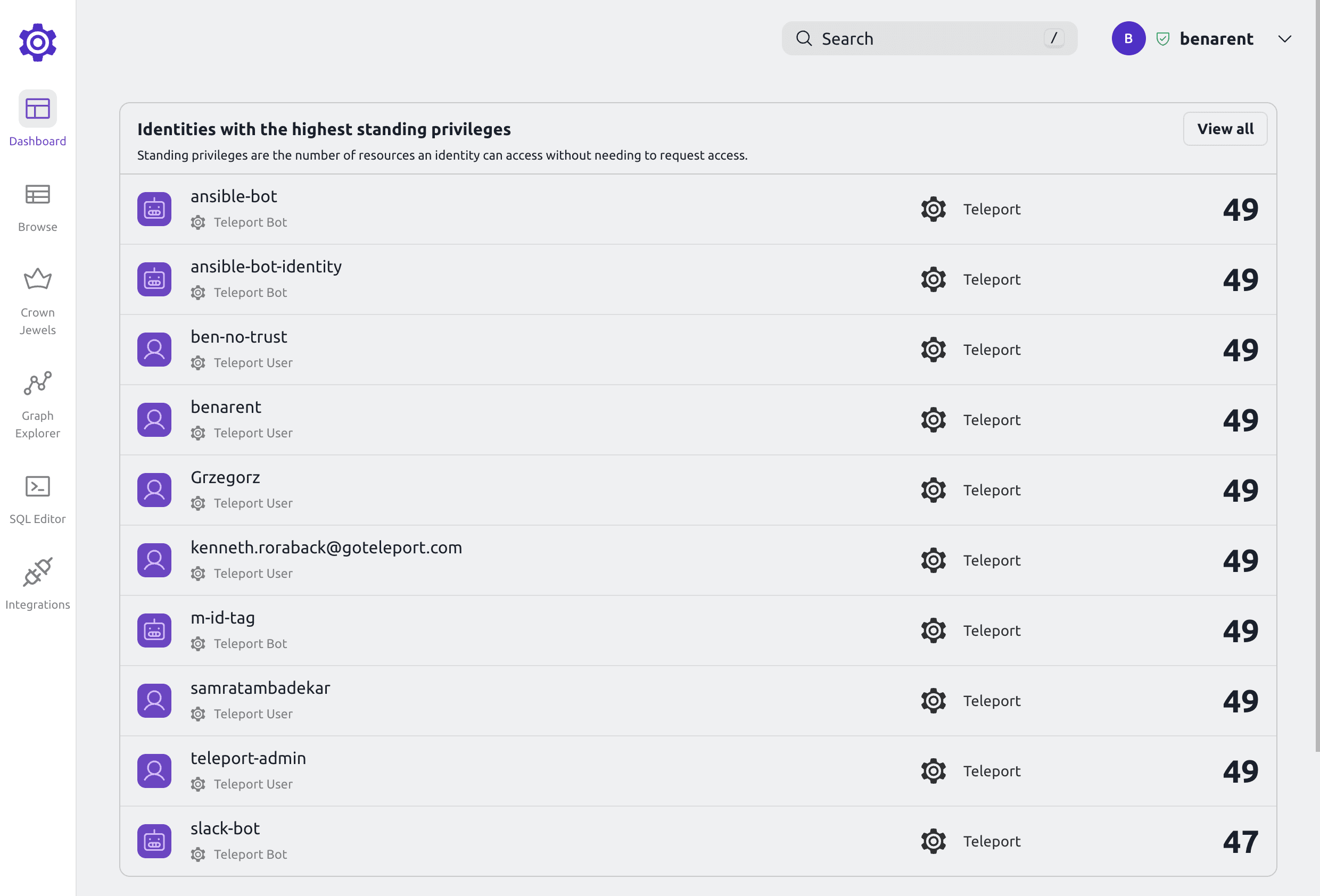
Visibility into Standing Privileges
One of the most significant challenges for security teams is the inability to easily identify and prioritize users with standing privileges or recognize policies that leave resources exposed. Without this visibility, potential security risks could go unnoticed, leaving critical resources vulnerable to breaches.
A new dashboard tackles this challenge head-on by providing a clear, real-time view of all standing privileges and identifying the most at-risk policies. It allows users to easily identify which accounts have the most privileges and what resources might have overly permissive access, such as world-open permissions. By bringing this information front and center, teams can immediately take action to reduce risk, improving the overall security posture of the organization.
This feature also facilitates better communication across teams. IAM leaders can use the insights gained from the dashboard to engage in informed conversations with other departments, emphasizing the urgency of addressing specific issues before they escalate into larger problems.

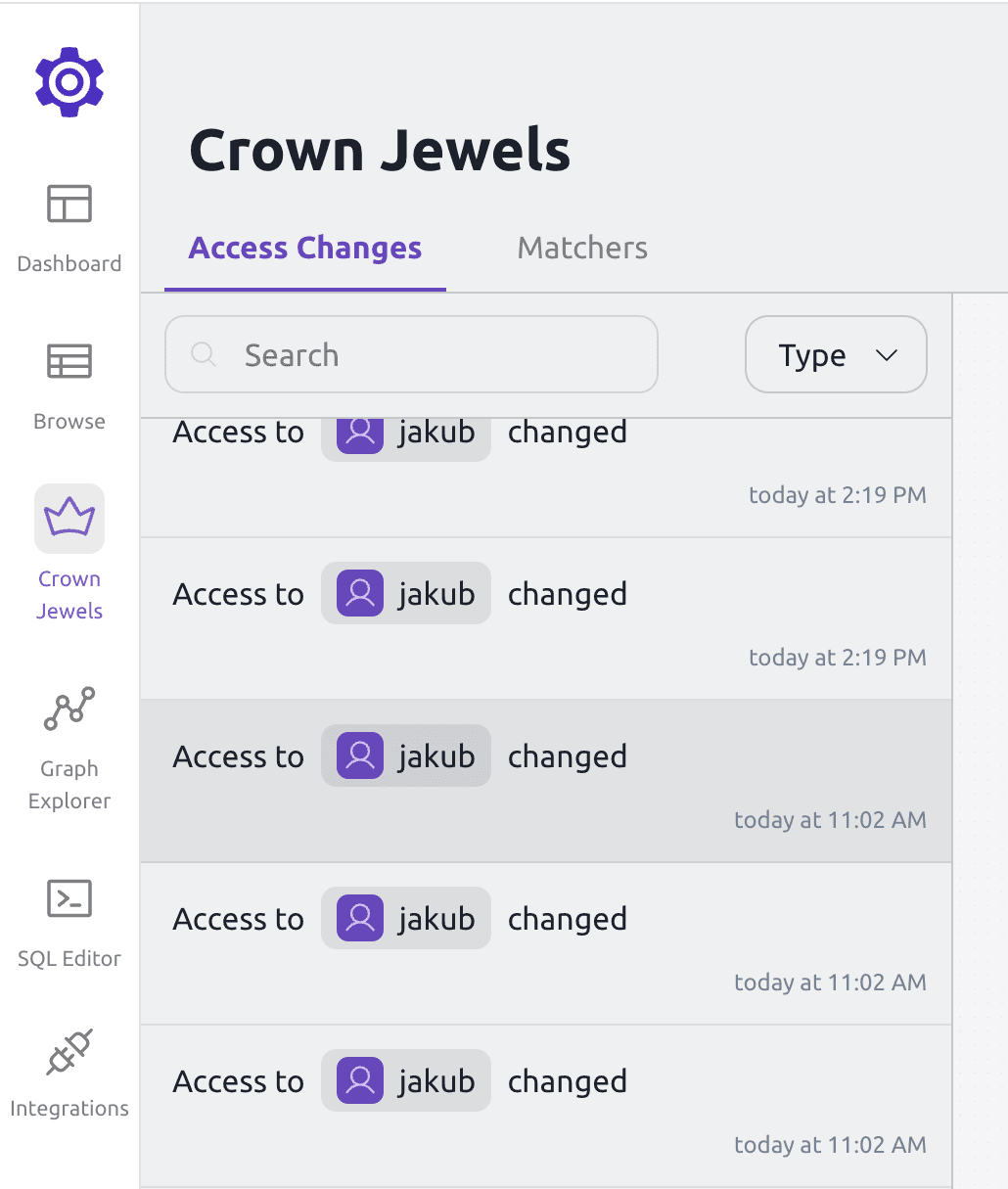
Crown Jewels: Prioritize Critical Resources
In any computing environment, there are typically hundreds or even thousands of resources. However, not all of these resources are equally important. Certain assets, known as “crown jewels,” are critical to the organization’s operations and must be protected at all costs. Whether it’s sensitive databases, mission-critical applications, or other high-value resources, the failure to secure these assets could result in catastrophic outcomes.
The Crown Jewels feature allows security and infrastructure teams to flag these high-priority resources. This helps cut through the noise by enabling organizations to focus their efforts where it matters most. The feature provides detailed insights on these critical assets, allowing teams to monitor any changes in access paths or permissions more closely.
Without the Crown Jewels feature, teams might struggle to differentiate between less important resources and those that require strict oversight. The risk of missing vital signals, such as unauthorized access modifications, increases when every resource is treated the same. With this feature, teams can create separate sets of crown jewels across departments, allowing self-governance while ensuring that critical assets remain well-protected.

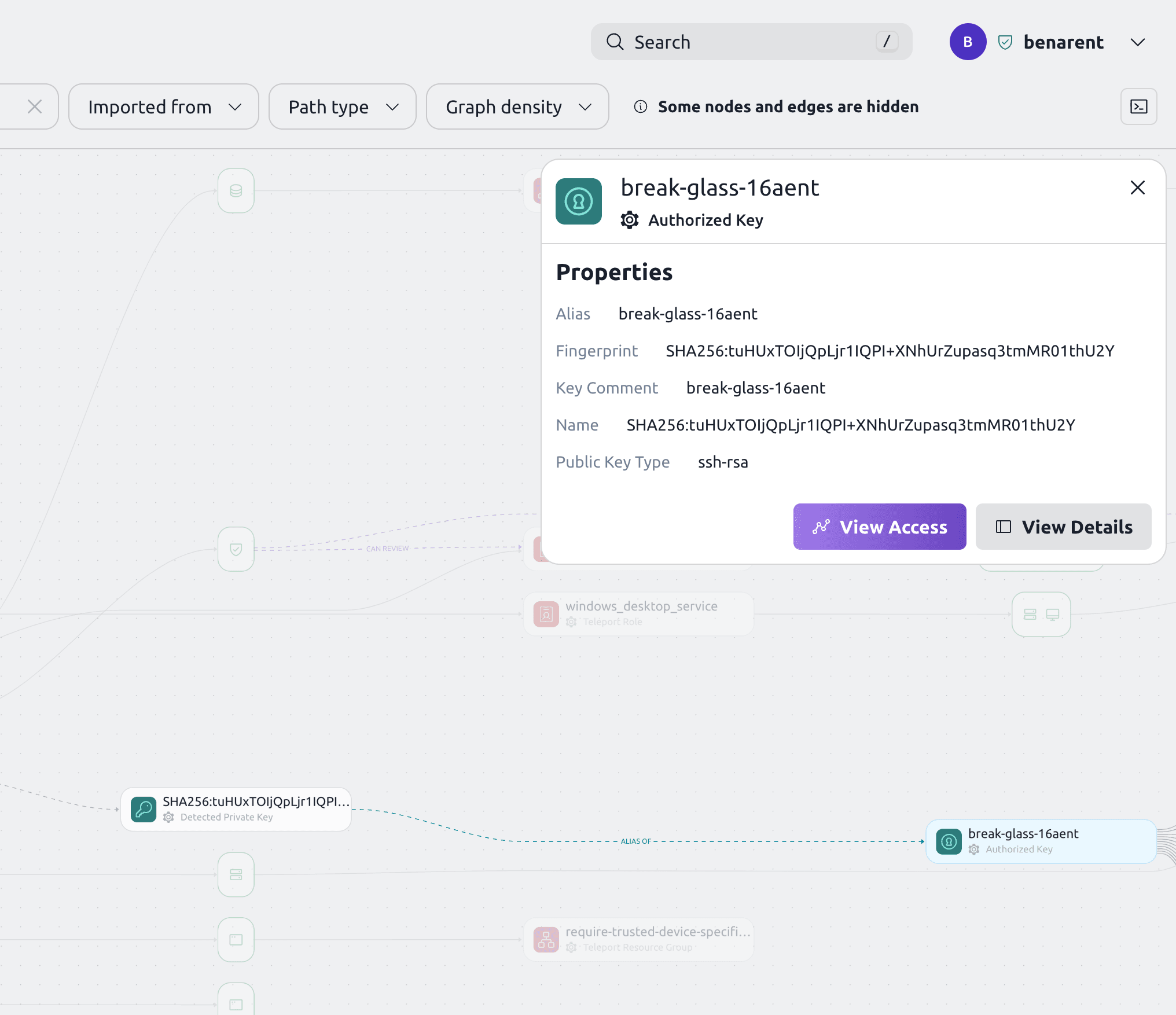
Discover Shadow Access via SSH Keys
One of the most concerning vulnerabilities in any system is the existence of shadow access, especially when it’s invisible to IT and security teams. Shadow access typically arises when users create unauthorized or undocumented SSH keys, which serve as backdoors to the system. These keys often bypass the formal access controls in place, posing a significant risk to the organization.
Teleport’s new feature addresses this issue by uncovering shadow access via SSH keys. By identifying these hidden access points, organizations can close potential backdoors, significantly reducing their risk exposure. This feature provides full visibility into the access landscape, ensuring that all access points, even those created informally, are accounted for.
Without this feature, organizations run the risk of unknowingly leaving critical systems exposed. Shadow access can lead to a breach, as attackers often exploit such hidden pathways. By bringing this issue to light, Teleport’s new feature helps teams eliminate blind spots and tighten their overall security.

The Importance of These Features for Modern Security
With today’s modern infrastructure, security teams face the constant challenge of managing increasingly complex systems. It’s no longer sufficient to rely solely on traditional access control methods. Organizations must adopt solutions that offer visibility, prioritization, and proactive risk management.
Teleport Policy’s newest capabilities are designed with these challenges in mind. The new dashboard provides essential insights, allowing teams to quickly identify risks and act accordingly. The Crown Jewels feature helps organizations focus their efforts on protecting the most critical resources. Meanwhile, the ability to uncover shadow access via SSH keys ensures that no access point goes unnoticed, reducing the risk of backdoor attacks.
These capabilities are not only about improving security but also about enhancing the efficiency of security teams. By providing clear, actionable insights, Teleport reduces the time spent on manually identifying risks and allows teams to focus on more strategic initiatives.
If you are ready to dive into how Teleport can solve for many of the issues discussed in this blog, please continue on to the associated topics listed below:
- Download the Teleport Identity Security datasheet
- Try Teleport for free for 14 days
Table Of Contents
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.
Tags

Subscribe to our newsletter

