Table Of Contents
Home - Teleport Blog - API Keys are Passwords Too - Dec 29, 2021
API Keys are Passwords Too
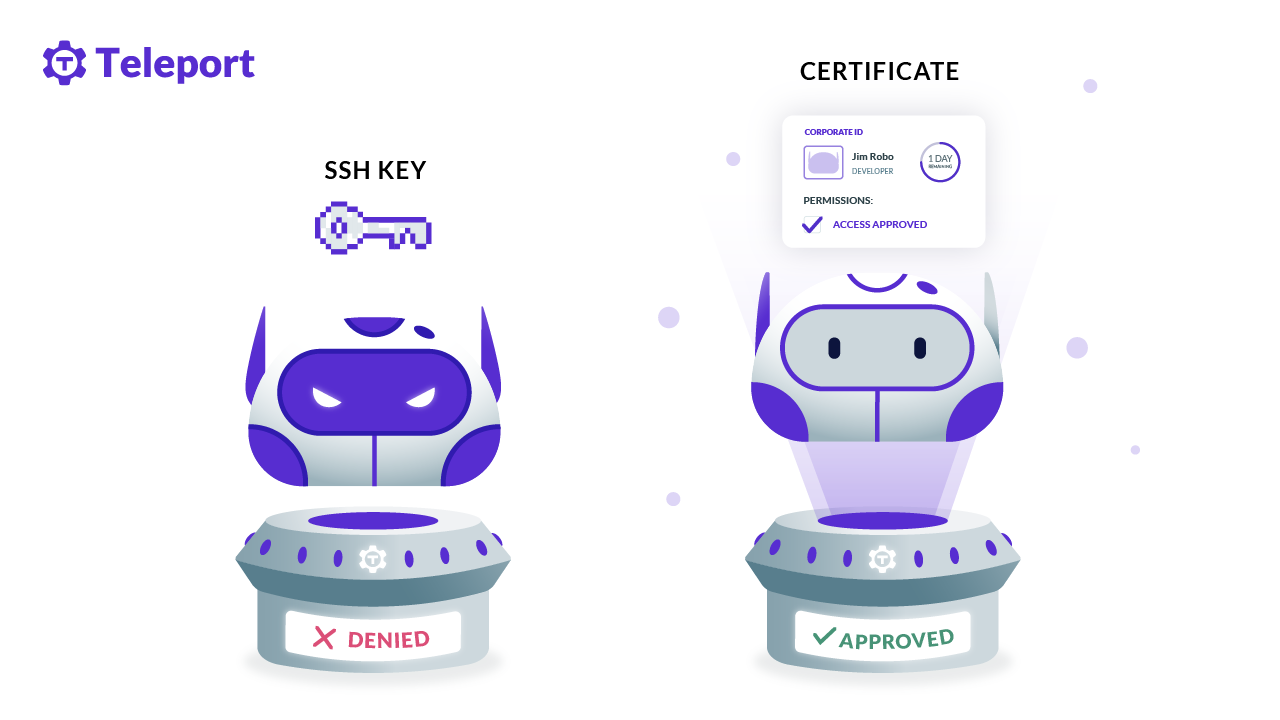
Use of misused or stolen credentials is the number one cause of data breaches. Using Password123 is worthy of a good laugh, but there are other passwords that are used everyday: API keys and other tokens used to access critical infrastructure.
Teleport recently commissioned a survey of 1000 IT, DevOps and Security professionals and found that passwords are the number one way of managing access to infrastructure.
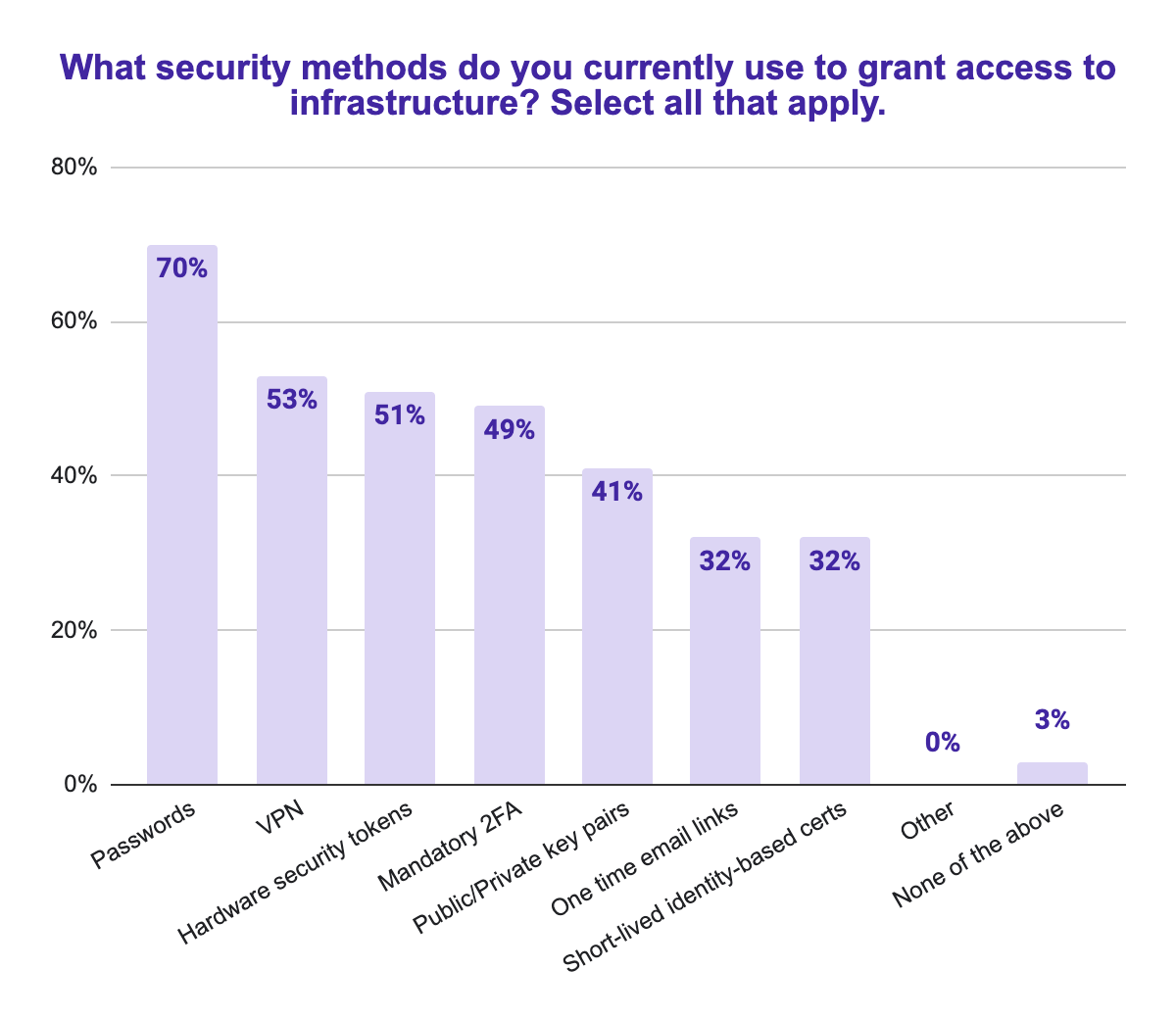

This is a problem. As our CTO wrote in a blog post recently titled “It’s Time to Get Rid of Passwords in Our Infrastructure”, a password is “any text that can be copied and passed ‘as is’ from a client to a service on the wire for authentication.”
The problem with passwords is that they can be guessed or brute-forced. They can also be stolen or intercepted by hackers before any breach is detected.
API keys are really just passwords, because like password123, they can be copied and pasted to access a Linux server and by right of having it, you are granted access.
Most people I talk to agree that using API keys exactly like passwords is a security problem. But they will suggest that they are not so susceptible to attack because they are using a “secure vault” to protect their API keys and other shared credentials. As our CTO recently wrote: “Some types of software promising to replace passwords are more dangerous than they seem, because they give you a false sense of security and reinforce the status quo. If you are using them, you haven’t replaced passwords, but created a treasure chest for hackers. These apps call themselves ‘Password managers’ or ‘Vaults’. I would call them ‘password aggregators’.”
The average cost of a data breach is about $4 million dollars, and it is even higher in regulated markets like health care and financial services. Mega-breaches, defined as breaches of more than 50 million records, cost on average 100x the average breach, or about $400 million. The 2017 Equifax breach cost $2 billion.
When you look at the cost of continuing to use API keys and other password-like static credentials to access infrastructure, it becomes clear that an alternative is needed.
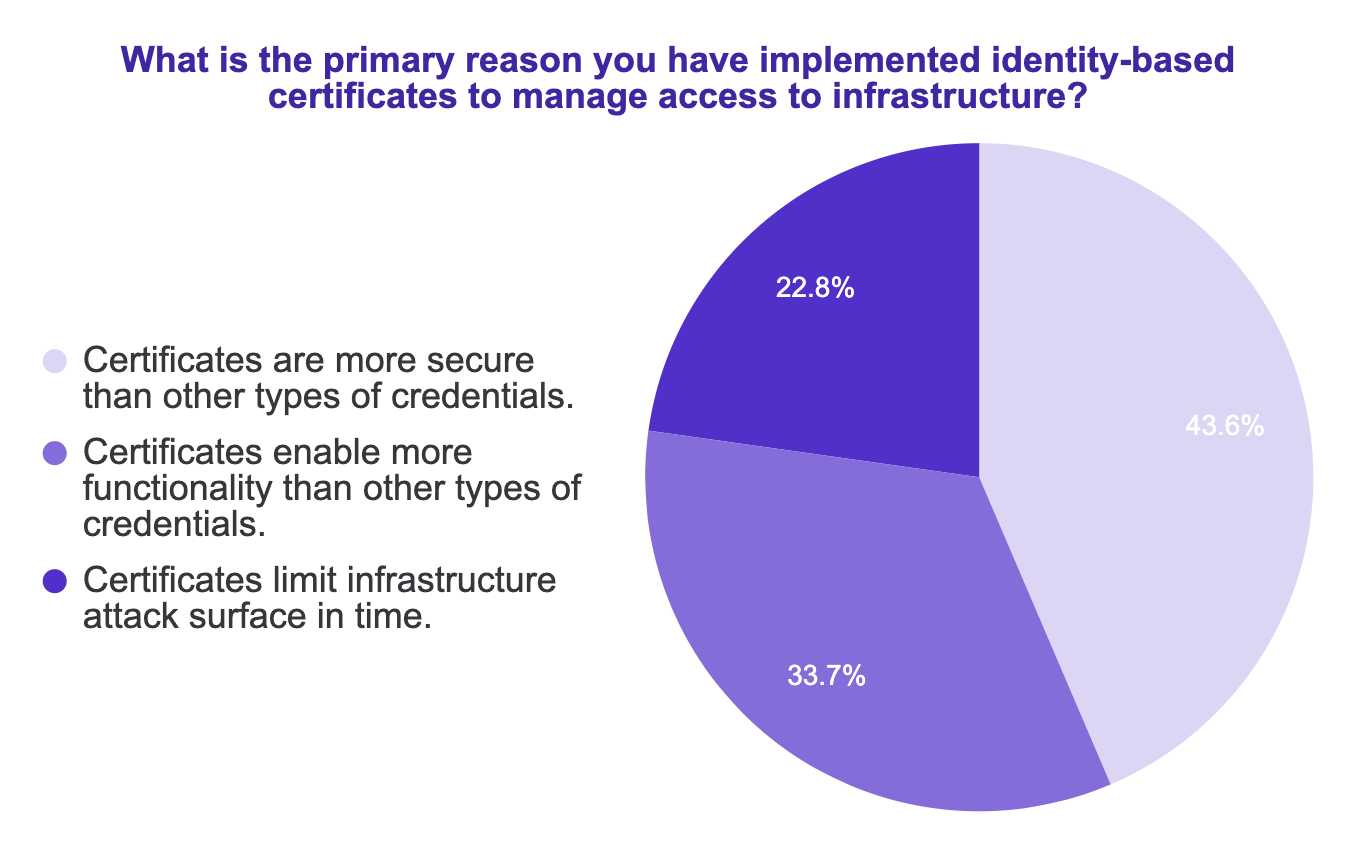
Luckily there is one, and it is not only more secure but also improves developer productivity. I’m talking about identity-based, short-lived certificates. In our survey, the innovative companies who had moved to certificates pointed out their enhanced security, great functionality (e.g. ability to easily deliver fine-grained role-based access controls), and how since they automatically expire, they reduce attack surface in time.

Teleport cybersecurity blog posts and tech news
Every other week we'll send a newsletter with the latest cybersecurity news and Teleport updates.
Teleport makes it easy to get all the advantages of identity-based, short-lived certificates for your entire infrastructure. In the process, your developers are more productive and you improve security. Want to learn more about how Teleport allows you to move away from passwords in your infrastructure? Talk to a solutions engineer today.
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

