Home - Teleport Blog - Accelerate FedRAMP Compliance with Teleport's Infrastructure Identity Platform
Accelerate FedRAMP Compliance with Teleport's Infrastructure Identity Platform
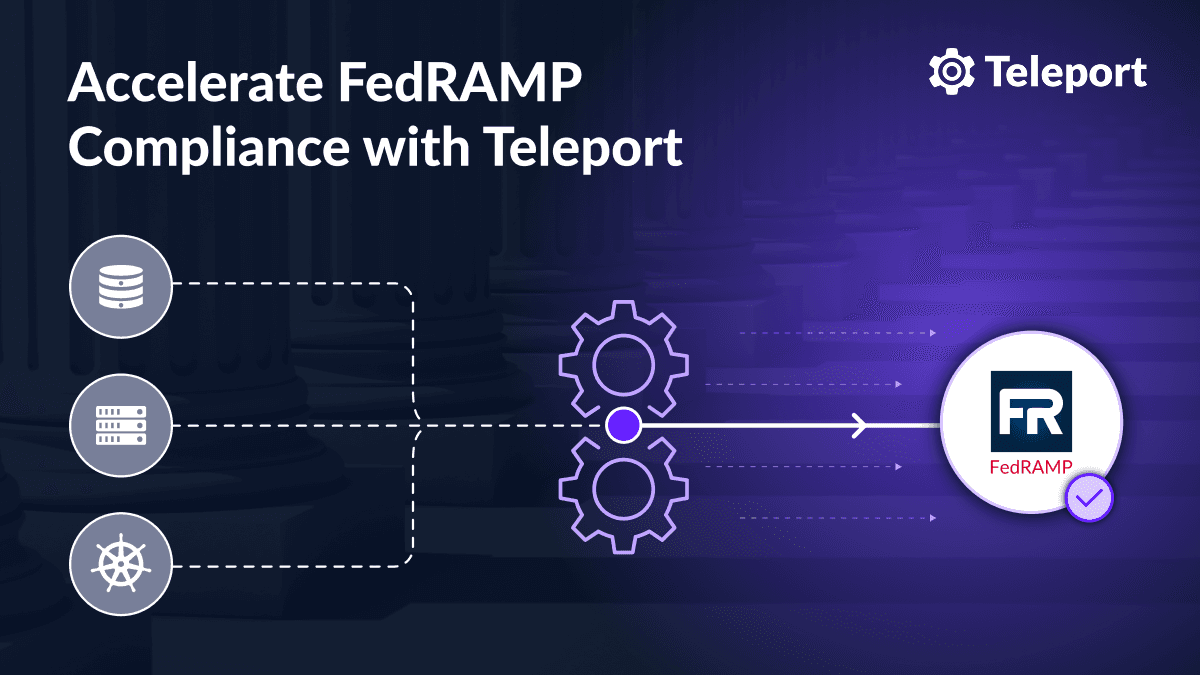
FedRAMP authorization can take years. The process is time-consuming, expensive and risky, requiring extensive human capital and dedicated technical resources from the initial project standup through continuous monitoring and compliance reporting before an Authorization To Operate (ATO) has been achieved.
The Teleport Infrastructure Identity Platform significantly reduces the time, cost and risk associated with FedRAMP compliance by addressing many of the most difficult FedRAMP control requirements.
Reduce Your Access Controls Rollout Timeline
The average organization will dedicate hundreds of hours to identifying, selecting, deploying, scaling, and troubleshooting technologies to implement FedRAMP controls. This is especially true for the controls related to infrastructure access. Specifically, there are twenty infrastructure access control and auditing requirements that are commonly cited as the most difficult and time-consuming to implement.
These infrastructure access control requirements are often the cause of failed audits, which can damage reputations and harm the organization's bottom line by stalling go-to-market strategies and delaying revenue opportunities.
Teleport eliminates the pain and risk associated with these complex control requirements through an on-premises infrastructure access solution that is easy to deploy and integrate into your environment.

With Teleport, FedRAMP admins can easily demonstrate controls for Access, Identification, Authentication, and Audit — significantly reducing the time to FedRAMP authorization and speeding up time to market.
The Traditional Approach to Centralizing Access Controls
Without Teleport, organizations face a technically complex, difficult and lengthy process of solving access control across their infrastructure in a way that meets FedRAMP’s many requirements.
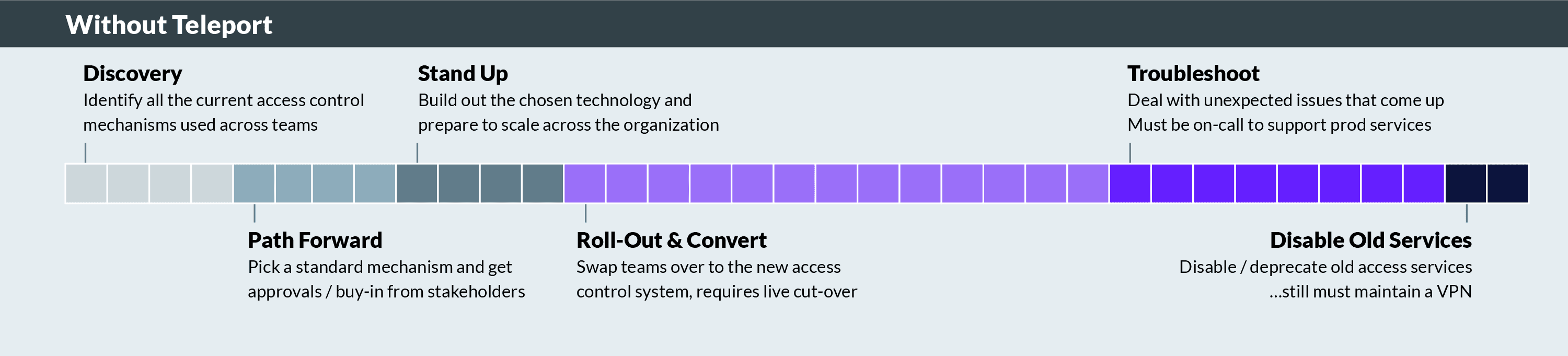
Here’s what the typical process for centralizing access controls looks like:

-
Discovery: FedRAMP Admins first must coordinate with internal DevOps, Engineering and IT teams to identify and understand all of the current access control mechanisms used within the infrastructure. Identifying and documenting these mechanisms introduces a significant risk of human error, especially in organizations with large, complex, and legacy infrastructure.
-
Path Forward: Next, they must select a standard mechanism for access control. This requires obtaining approval and buy-in from stakeholders across the organization. Once again, the human element is likely to complicate this step as discussions, negotiations and concessions will need to be made to ensure everyone is satisfied with the approach.
-
Stand Up: Once a mechanism is defined, the team must begin building out the chosen technology and preparing it to scale across the organization.
-
Roll-out: Upon completion of the technical build, the organization must then embark on the risky process of transitioning teams to the new access control system, often via a live cut-over, which may disrupt business operations.
-
Disable Old Services: When the roll-out is complete all of the old access mechanisms must be disabled/deprecated, likely while still maintaining a VPN.
-
Troubleshoot: Finally, the FedRAMP admin and supporting team must provide on-call support and respond to unexpected issues to ensure the new system works seamlessly.
The Teleport Approach to Centralizing Access Controls
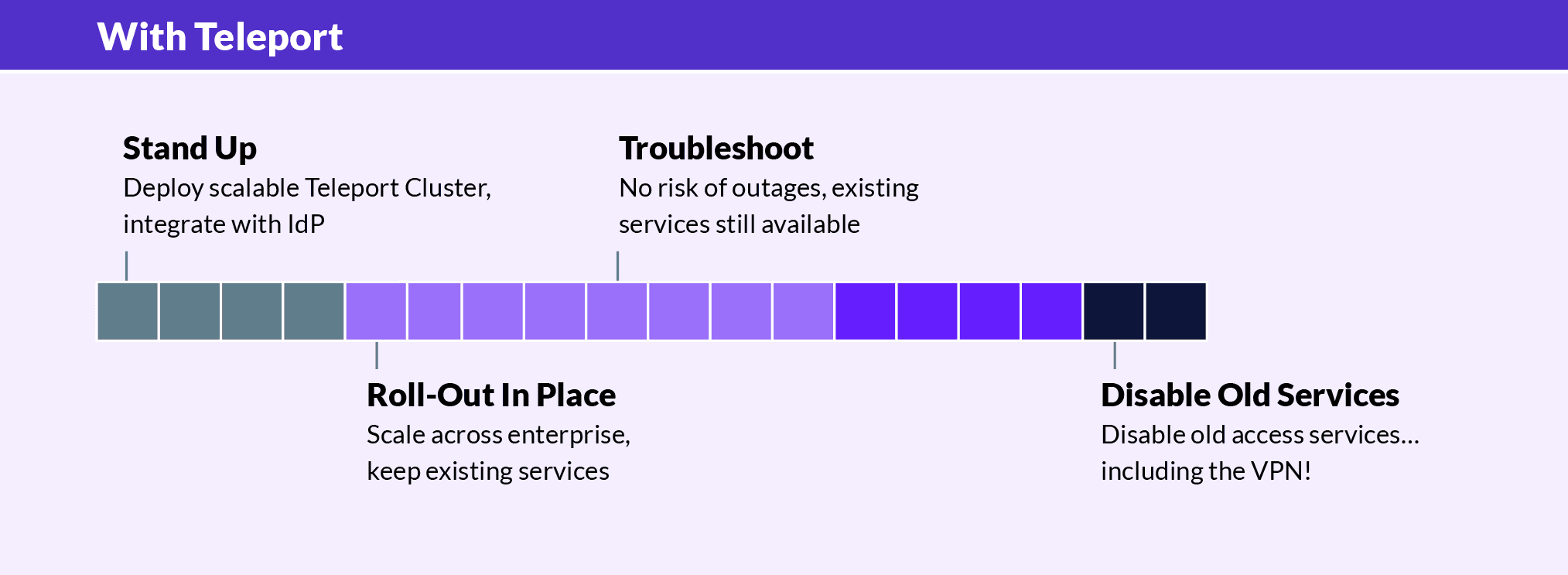
By deploying Teleport Infrastructure Identity Platform, organizations can significantly reduce the time and cost burden associated with traditional approaches to centralizing access controls. Below is a summarized example of how the same process would unfold if Teleport were used.

-
Stand Up: The organization deploys a scalable Teleport Cluster on-premises and integrates it with their Identity Provider (IdP). This step is straightforward and is performed with zero disruption to business operations.
-
Roll-Out: Next, they scale the Teleport deployment across the infrastructure, troubleshoot issues, and maintain existing services without disrupting your engineering teams. Once again, this process is seamless and avoids disruption. Teleport enables the organization to keep all of their existing services.
-
Disable Old Services: Finally, old services are disabled, including VPNs, without compromising security or compliance.
Teleport’s path to implementation of an interruption-free roll-out while letting teams maintain their existing access control mechanisms is the fastest, least friction path to centralize access control across large infrastructures and many teams. Along the way, users can adopt Teleport and become comfortable with the solution at their own pace, effectively avoiding many of the pitfalls on the way to widespread adoption of a uniform solution.
Which FedRAMP Controls Does Teleport Address?
Once deployed across your services, Teleport simplifies the process for achieving and maintaining FedRAMP compliance by addressing the most challenging control requirements related to infrastructure access and auditing. A full list of the FedRAMP access control name, ID and Teleport capability can be found here.
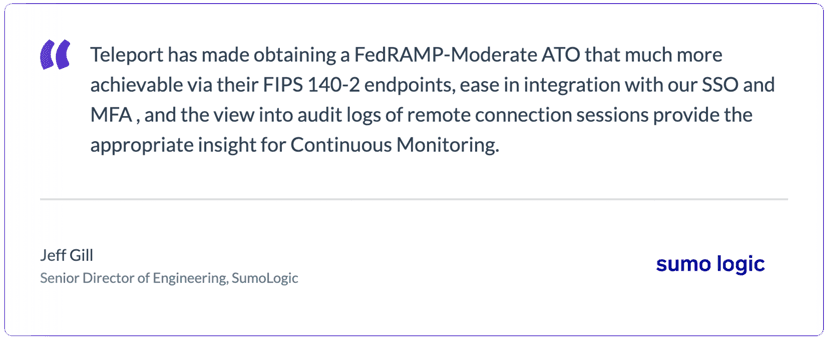
Teleport is currently deployed within the boundaries of multiple FedRAMP Authorized organizations. Customers consistently cite these key Teleport benefits:
- Access Control: All admin connections to internal hosts are secured and managed through robust access control mechanisms.
- FIPS-Validated Encryption: Every admin connection uses FIPS-validated encryption, ensuring the highest level of security.
- Elimination of Shared Credentials: here are no shared passwords or break-glass credentials, reducing the risk of unauthorized access.
- Session Controls: Teleport implements complex requirements such as concurrent session control, session timeouts, login banners, and automatic session termination.
- Comprehensive Logging: Teleport logs all personnel access and includes session recording for SSH, providing an easy-to-produce and complete audit trail.
Learn More
As you navigate the complexities of FedRAMP compliance, it’s crucial to leverage solutions that don’t compromise your DevOps flow or tech stack. Our webinar, hosted by Xin Ding, VP of Product at Teleport, explores how Teleport’s robust infrastructure access and security platform can help you overcome some of the most challenging aspects of the FedRAMP process. Webinar: Simplifying FedRAMP Compliance with Teleport
Table Of Contents
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.
Tags

Subscribe to our newsletter

