Trusted by Market Leaders


















SSH
Replace bastion hosts
SSH into servers running anywhere, from clouds and data centers to third party private networks behind NAT and firewalls.
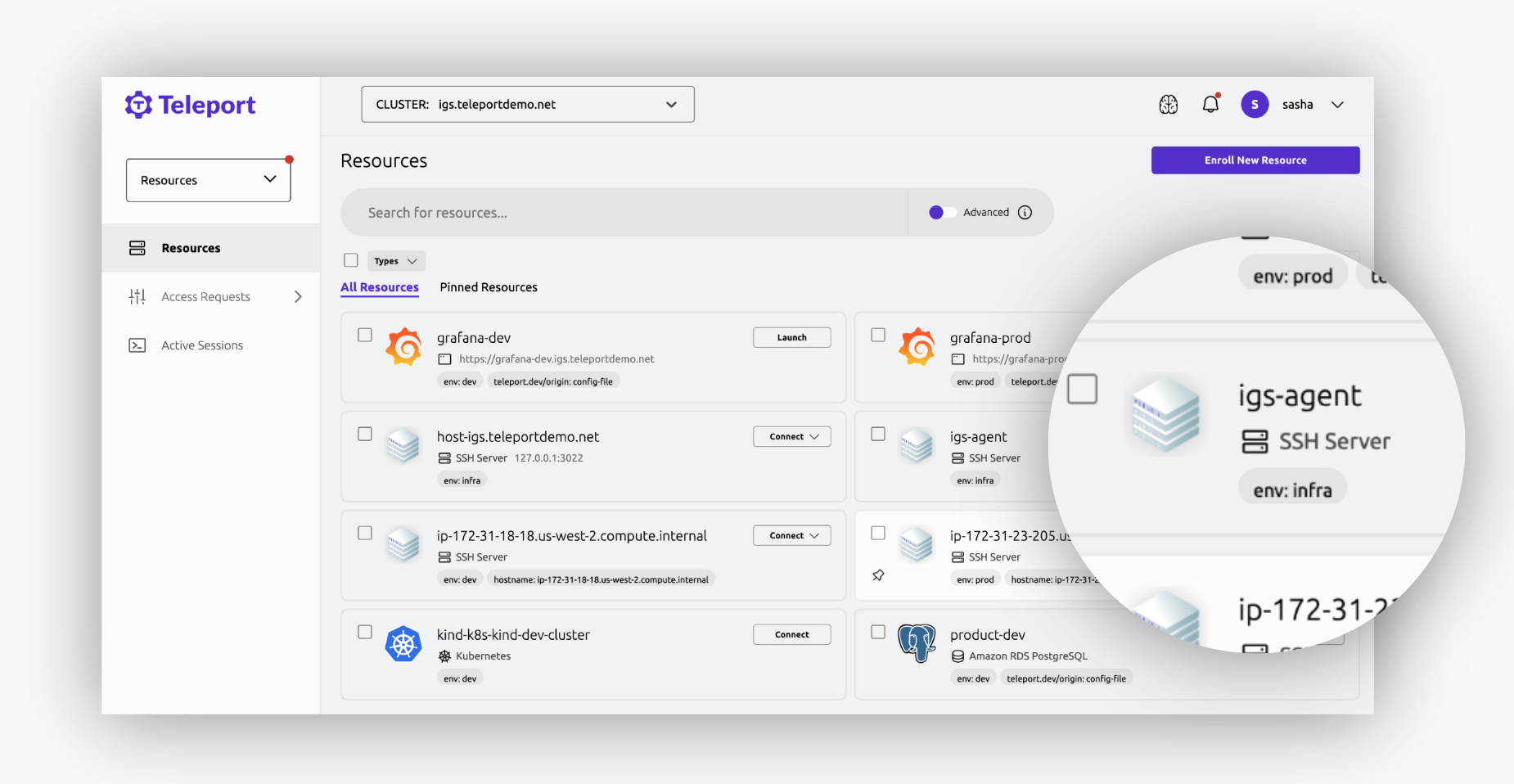
Transform Your SSH Server Access

Improve Engineer Experience
No need to remember passwords or credentials, or access paths. Access servers anywhere from a dynamic, live inventory of servers across infrastructure silos.
Protect Your Infrastructure
Secure remote access, without VPNs or bastion hosts. Eliminate credentials and standing privileges, enforcing the principle of least privileged access.

Make Compliance a Breeze
All sessions are tracked at the identity and protocol level, making it a breeze to compile compliance reports or conduct forensic investigations.

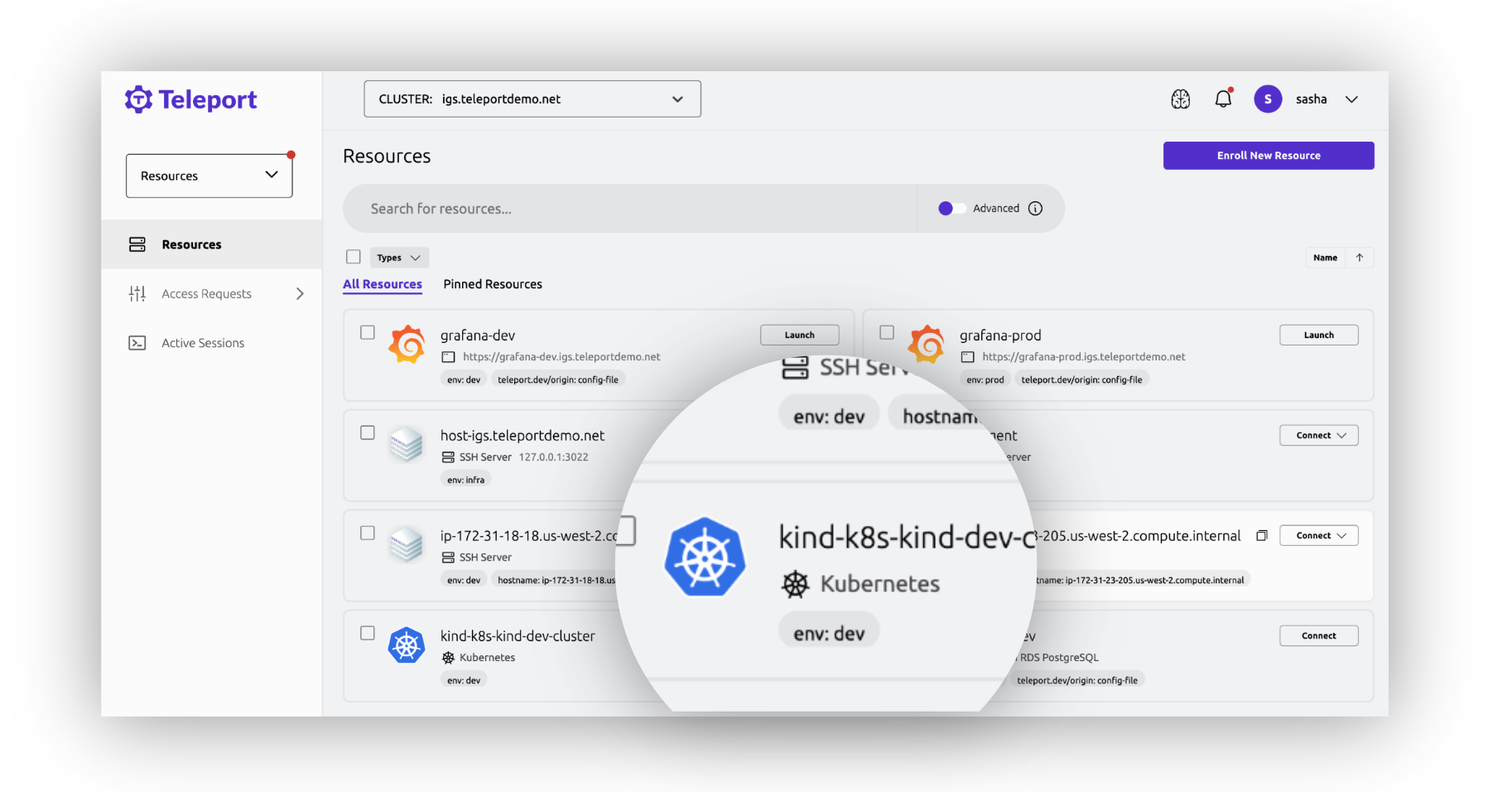
Kubernetes
Improve engineer experience
Log in once to access all environments. No need to juggle passwords or hop between VPNs and clouds. Teleport supports all CNCF-certified Kubernetes distributions and existing tooling: kubectl, EKS, AKS, GKE, Rancher, K3s, Helm, Istio, Terraform, and more.
Databases
Protect data from exfiltration
Secure and audit all database connections to protect your data from being accessed and exfiltrated by unauthorized parties. Your teams can keep using their favorite tools: pgAdmin, PopSQL, DBeaver, MySQL Workbench, MS SQL Management Studio, and others.

Web Apps
Secure remote access without VPNs
Access CI/CD pipelines, monitoring dashboards, code repositories and other applications across all environments without VPNs or open ports. Reduce attack surface area by multiplexing all connections to all apps and services on a single public facing port using mutual TLS and certificate auth.
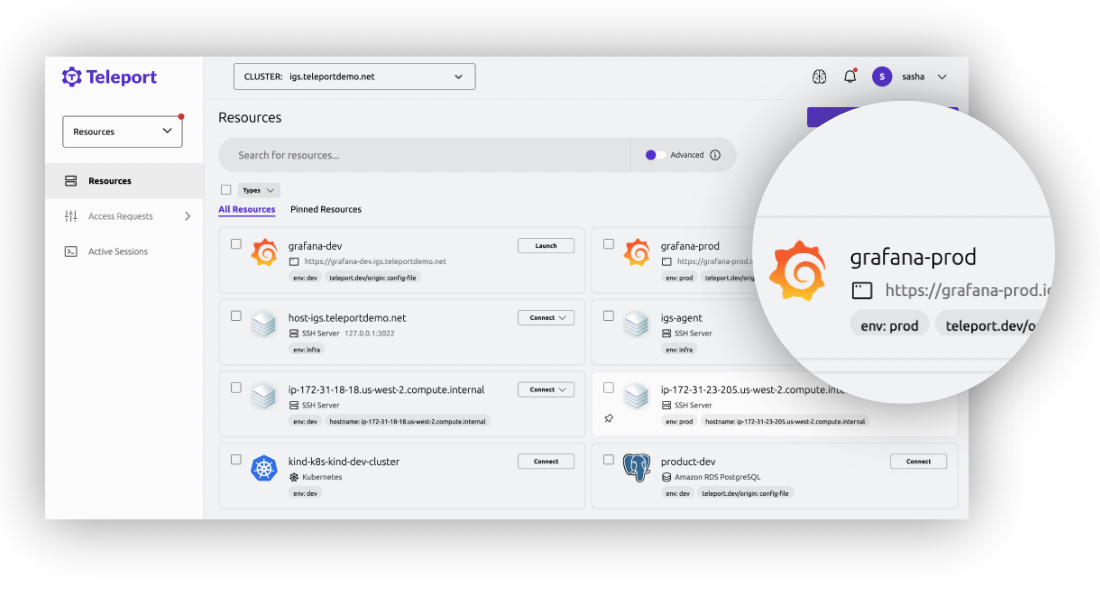
Windows
Secure RDP access
Access Windows hosts across all computing environments in the cloud, on-premises, or at the edge without opening RDP ports and using passwords. View live activity and audit events for Windows user sessions across all environments. Automatically discover and provision access to all Windows servers with custom automation, Active Directory, or cloud API.
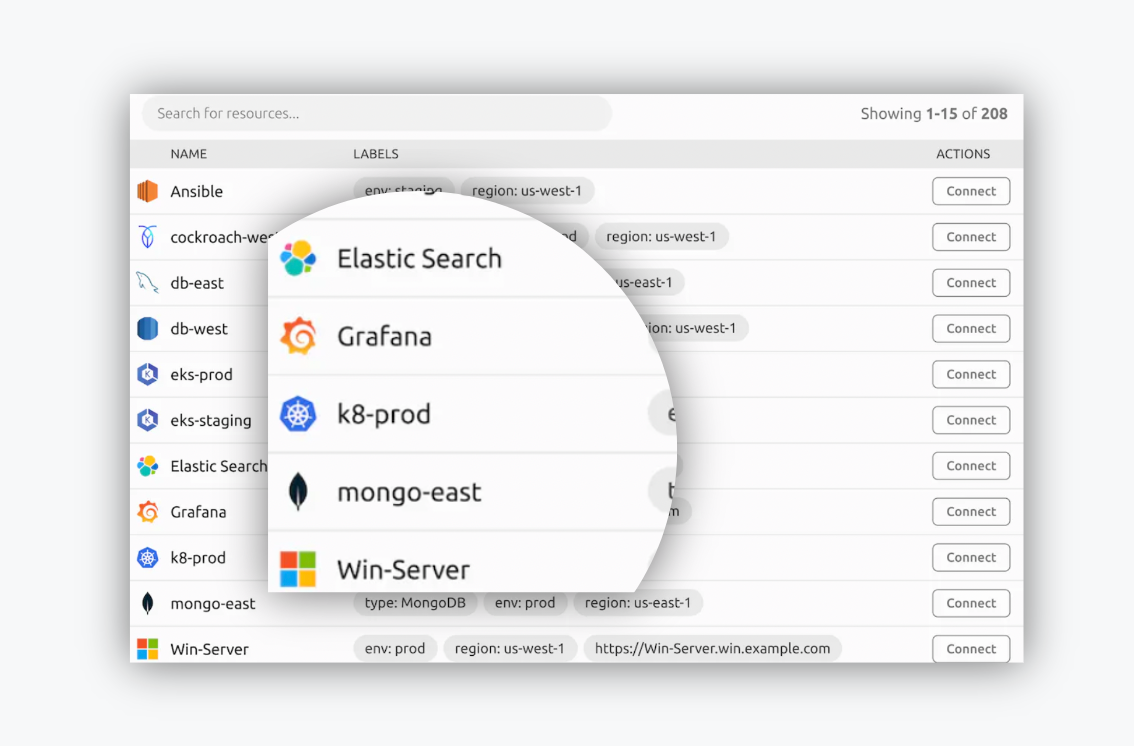
Clouds
Secure access to AWS, Azure, and GCP
Provide on-demand, least privileged access to your AWS, Azure and GCP cloud infrastructure. Use a single path to search, request access, and switch between multi-cloud environments without passwords, opening ports, or looking up internal hostnames.

