Table Of Contents
Teleport Blog - Goodbye passwords. Why Teleport is joining the FIDO Alliance - Jul 28, 2022
Goodbye passwords. Why Teleport is joining the FIDO Alliance

Passwords and other shared secrets are the number one cause of data breaches. The security risks of passwords is widely recognized in the consumer space with the leading tech companies (and competitors) including Microsoft, Google, Apple joining together to create the FIDO Alliance to reduce the over-reliance on passwords. With FIDO, passwords are replaced with more secure, and easier to use biometric and cryptographic authentication.
FIDO is the organization behind the most widely used passwordless protocol used today - WebAuthn. WebAuthn powers the biometric logins on modern browsers and mobile devices including Touch ID, Face ID and Windows Hello.
Teleport has just joined the FIDO Alliance to bring this improved mix of security and usability to infrastructure resources like Linux and Windows servers, databases, Kubernetes clusters, and internal applications. We believe, it should be just as easy and secure to authenticate against these resources in the cloud or corporate data center as it is to log in to a mobile banking or social media site.
This blog will explain why enterprise cloud environments and data centers have more passwords than you would guess and why we must get rid of them all to protect our infrastructure and customers from attack. By joining the FIDO Alliance, and releasing our own FIDO-based Passwordless Infrastructure Access Solution, Teleport is enabling this future today.
Passwords are everywhere in your infrastructure
When most people think about passwords, they imagine something like a login form on an e-commerce website. However, passwords are widely used for systems guarding critical infrastructure access.
The attackers in the infamous Solar Winds hack planted one of the most sophisticated pieces of malware right in the Orion software. This software was used to infiltrate key U.S. corporations and agencies, resulting in massive exposure. But how did attackers get the access in the first place?
Solarwinds investigation states:
We’ve confirmed that a SolarWinds email account was compromised and used to programmatically access accounts of targeted SolarWinds personnel in business and technical roles.
By compromising credentials of SolarWinds employees, the threat actors were able to gain access to and exploit our Orion development environment.
But it’s not only email apps that get hacked and phished all the time. Most of our infrastructure relies on various forms of passwords.
API keys or sender-unconstrained Oauth 2.0 tokens are a form of passwords too. If an attacker steals the secret, the game is over, just like with passwords. They can impersonate and make any API calls on behalf of the user.
Oauth 2.0 is commonly used in lots of login flows, you might be receiving Oauth 2.0 tokens today to access your Kubernetes cluster. OIDC is a reputable standard that results in OAuth 2.0 tokens being issued to users or machines as a part of the login flow. But Oauth 2.0 comes in different flavors, and most of the time the tokens issued to users and services are no different than passwords, as they are not constrained to the device or identity of the user.
In April 2022, the infrastructure world experienced a mass scale attack using stolen Oauth 2.0 credentials. Here is how attack unrolled:
First, attackers stole a machine account credential - basically a shared secret. Then they got access to other shared secrets to access Github API, OAuth 2.0 tokens:
On April 7, 2022, a threat actor obtained access to a Heroku database and downloaded stored customer GitHub integration OAuth tokens. Access to the environment was gained by leveraging a compromised token for a Heroku machine account.
After that, attackers got foothold to private repositories in Github and started looking for secrets in them:
Based on subsequent analysis, we believe this API key was obtained by the attacker when they downloaded a set of private npm repositories using a stolen OAuth token from one of the two affected third-party OAuth applications described above.
It’s secrets and passwords all the way down. Attackers start with the user's password or machine token, exploit those to exfiltrate other secrets, such as Oauth 2.0 tokens or API Keys, and it goes on, and on and on.
That is why relinquishing login passwords is not enough, we have to eliminate all forms of shared secrets from our infrastructure. Vaults that store long lived shared secrets are attacked by hackers. We must replace secrets with identity-based access - a system that issues short lived credentials bound to devices and users they have been issued for. Google recognized this more than a decade ago with its famous BeyondCorp paper. And the Federal Government this year is recommending the same approach in its widely popularized zero-trust memo.
FIDO is the way our industry can move past secrets like passwords, keys and tokens for infrastructure access, improving both usability and security.
Instead of storing credentials in a vault, the old school way of providing access, FIDO promotes standards that use a combination of biometric authentication and private keys that never leave secure enclaves of devices they are associated with. Let’s take a look at the FIDO diagram showing a login process:
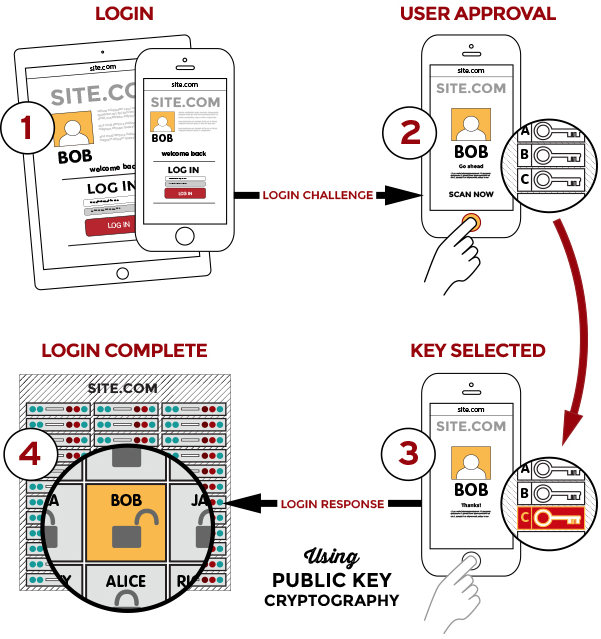

How exactly does FIDO work?
- Private key is stored in the Secure Enclave on Apple devices and in the Trusted Platform Module (TPM) on Windows Hello.
- Only public keys are shared with third parties to verify your identity
- Biometric data is stored on the device, not on the service side, never leaving your device.
In the Teleport 10 release, we have added full support for FIDO Webauthn passwordless authentication for accessing all your infrastructure, including Windows and Linux servers, Kubernetes clusters, databases, and internal applications like Jenkins, Elasticsearch or Grafana dashboards.
In our implementation we embraced not only the passwordless nature of WebAuthn logins, but also the strong cryptographic guarantee that credentials issued to users will be useless on other machines:
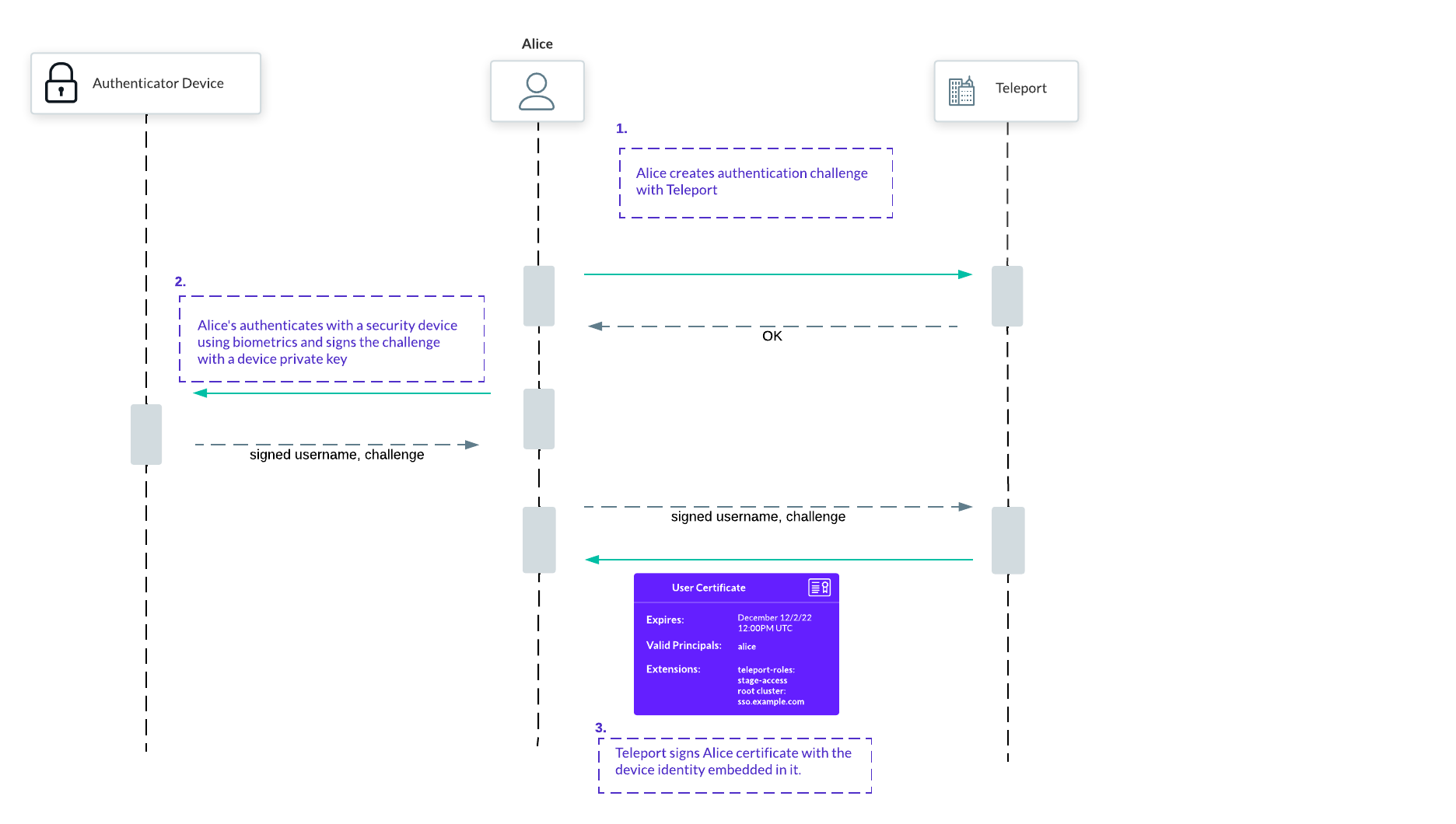

We can't stop just at passwordless access for users, we have to eliminate passwords and secrets from all of the infrastructure, all the way. With our project Machine ID we bring passwordless access for machines and services.
By removing all forms of secrets from our infrastructure, security and user experience are improved. This can’t happen a moment too soon and we are excited to join the FIDO Alliance to further this mission.
Tags
Teleport Newsletter
Stay up-to-date with the newest Teleport releases by subscribing to our monthly updates.

Subscribe to our newsletter

