
TELEPORT ACCESS PLATFORM
Secretless Database Access
The easiest, most secure way to access data
Secure, compliant, and effortless Database Access for all DBs from Amazon Aurora to Snowflake

Trusted by Market Leaders




















Prevent phishing attacks
Move away from vulnerable keys and passwords towards auto-expiring certificates for users and service account store access databases.

Meet compliance requirements
Continuously maintain compliance and pass audits with minimal effort, The supported standards include SOC 2, FedRAMP, HIPAA, ISO 27001, PCI and more.

Complete visibility into access and behaviour
See what's happening and who is responsible with the live session view, and the consolidated audit log across all the databases.

Free yourself from network boundaries
You can access databases running anywhere. From clouds and data centers to this party private networks behind NAT and firewalls,
Access that doesn't get in the way
Login once and easily switch between environments, No need to juggle passwords or hop between VPNs.
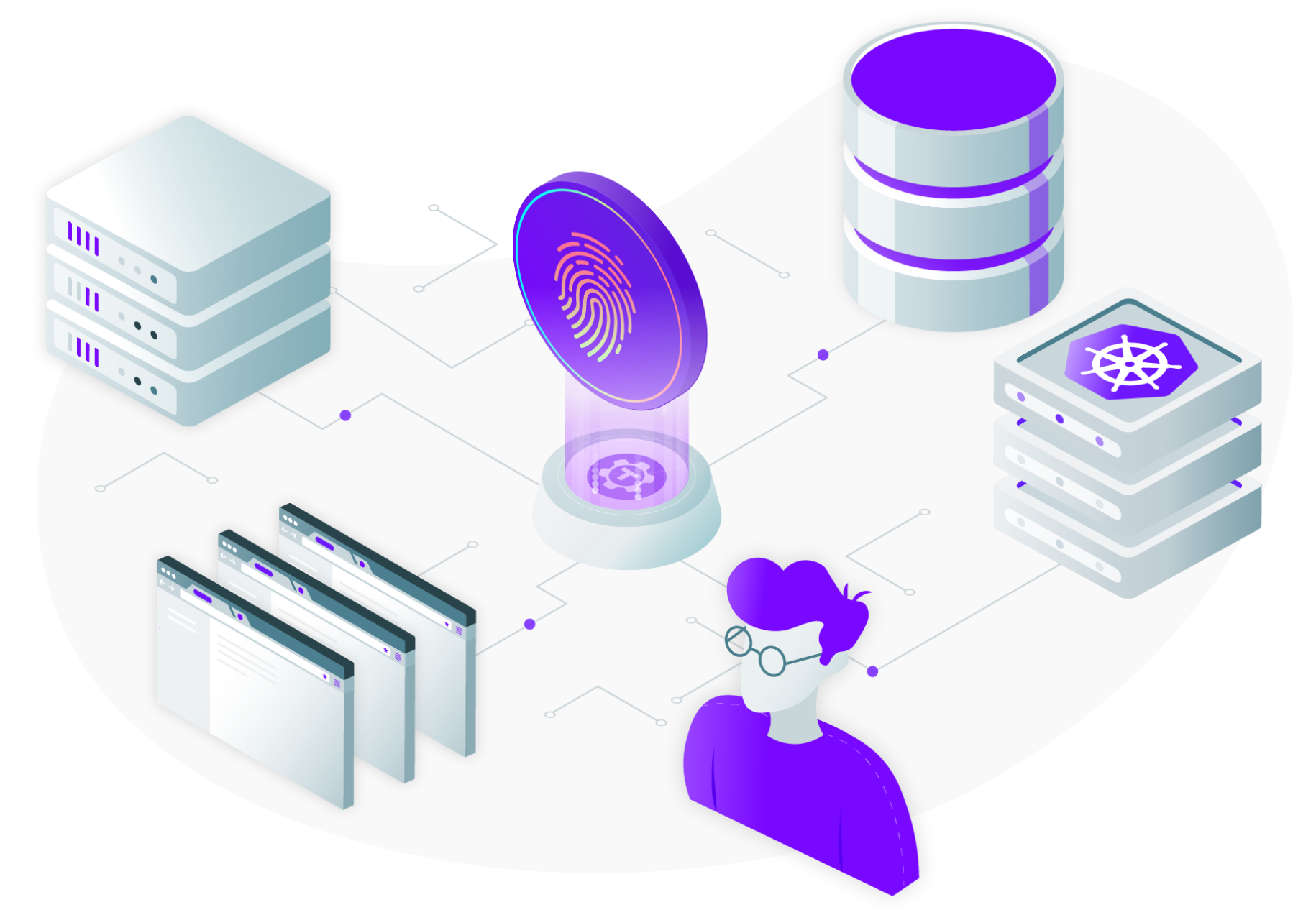
Break access silos
Reduce overhead by consolidating database access permission in one place. Easily enforce policy for engineers and service accounts across all environments.

Features

SSO for all database
SSO lets you quickly onboard and off-board your team. Teleport works with any SAML or OIDC SSO Provider.

FIPS mode
Avoid human errors by enforcing only configuration options that are compliant with FIPS 140-2

Service accounts
Automatically issue and rotate certificates for CI/CD automation with the Machine ID feature.

Access requests
Move away from privileged accounts with just-in-time temporary privilege escalation.

Service controls
Moderated sessions, concurrent session restrictions, proactive session termination, and identity locking.

Trusted devices catalog
Automatic live catalog of trusted servers, trusted laptops and workstations.
+ more
Database Demo
Works with everything you have

MySQL

CockroachDB

GCP Cloud SQL

Amazon RDS

Amazon Aurora

Amazon Redshift

MongoDB

MongoDB Atlas

MS SQL

Redis

Snowflake

MemoryDB

Elasticsearch

Cassandra

