
USE CASES
Protect Your Infrastructure
Make your infrastructure resilient to identity-based attacks
Trusted by Market Leaders




















Thwart attackers
Eliminate credentials & standing privileges
Remove secrets and over permissions as attack surfaces and enforce the principle of least privileged access. Teleport leverages cryptographic identity for all users, machines, devices, resources and workloads, preventing attackers from stealing credentials or secrets or exploiting human error to gain access.
Harden your Infrastructure Security

Teleport Access
Eliminate credentials and standing privileges. Secure remote access from anywhere to applications and workloads.

Teleport Identity
Monitor and respond to weak access patterns, lock compromised users, and deploy access requests and reviews.

Teleport Policy
View and analyze access relationships, intervene in threat incidents, and manage and apply policy across all infrastructure.

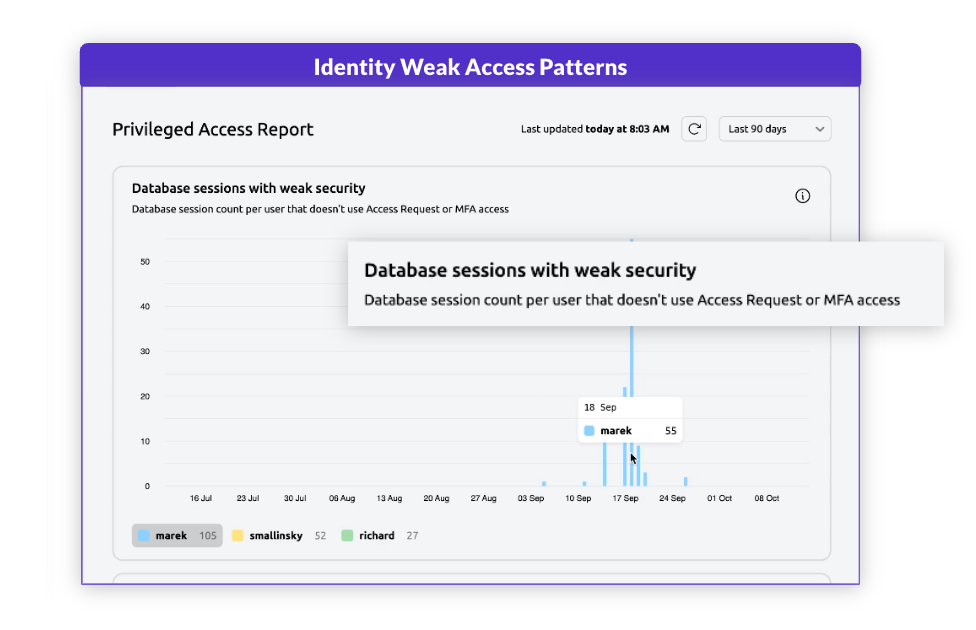
Monitor & Respond
Gain visibility into privileged access patterns
Identify weak security practices, detect overly broad privileges, and inspect how many critical sessions are not using strong protection (e.g., MFA, trusted devices) Alert on access violations and purge unused permissions with automated access rules.
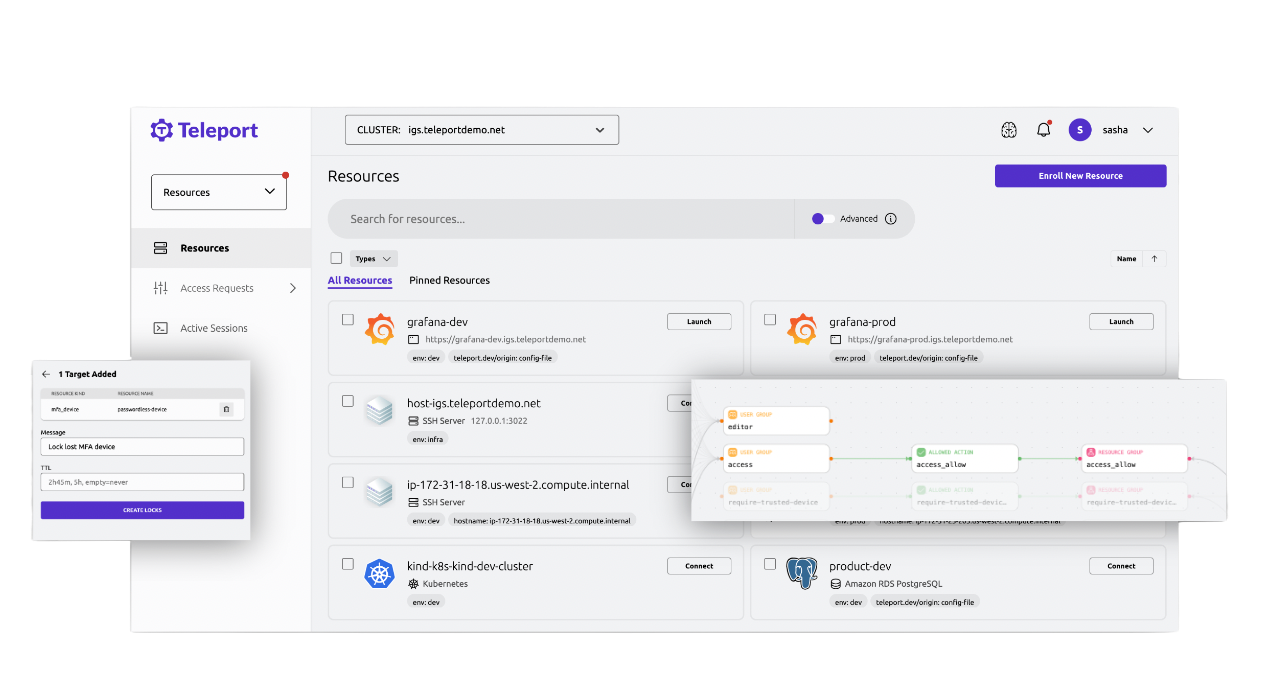
Remediate Everywhere
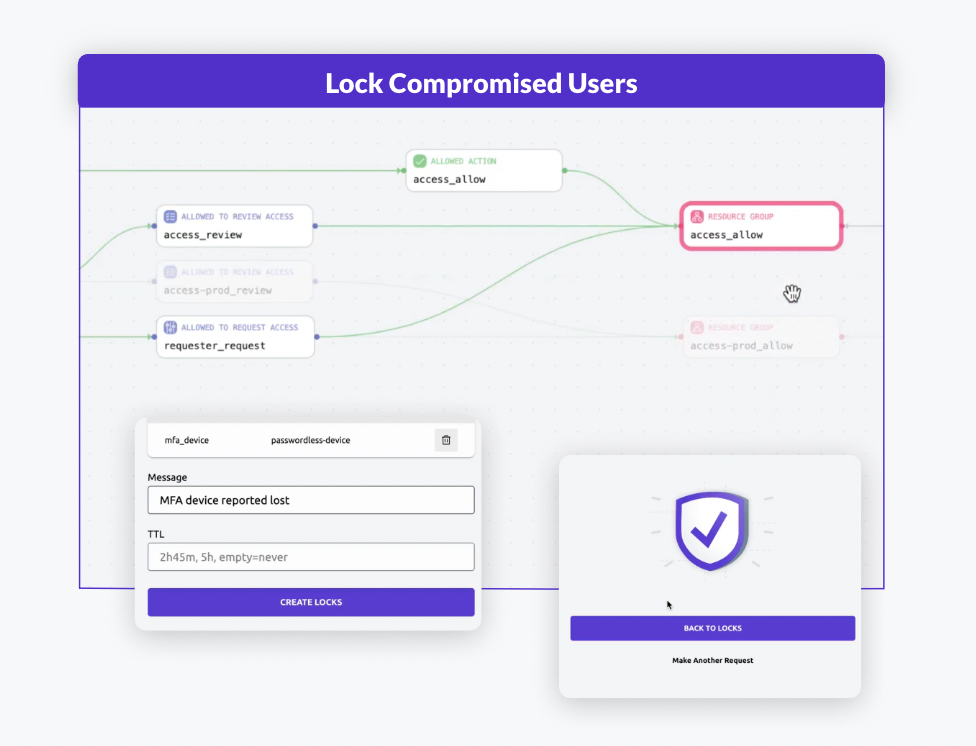
Lock users, everywhere they access infrastructure
Lock compromised users, whether due to a lost device, a threat incident, or change in employment status, instantly across all infrastructure.
One Place for Policy
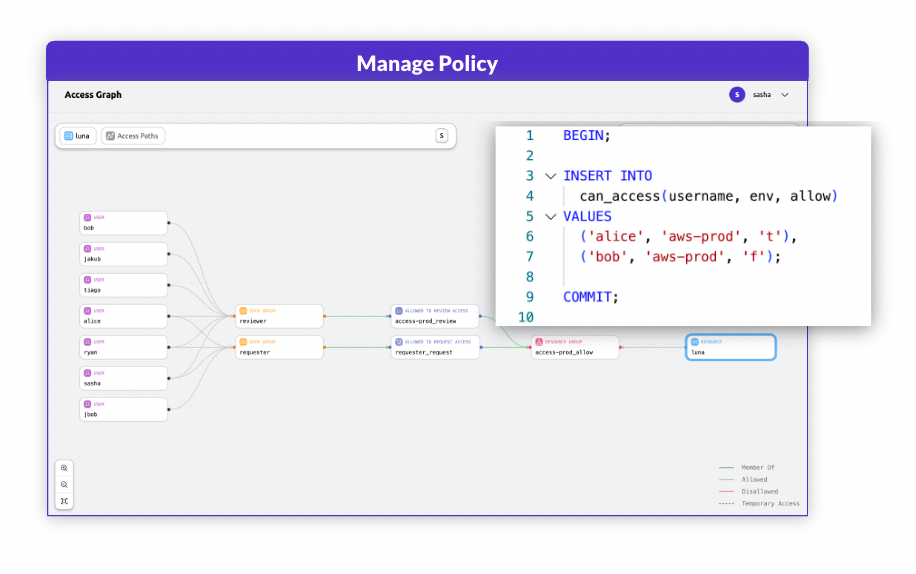
View access relationships & manage policy
Gain visibility and control, minimize attack surface and reduce management overhead with all your access space mapped out as a unified graph. Query, analyze and optimize the paths to achieve the principle of least privileged access.
Secure Access from Anywhere
Zero trust access to resources and workloads
Teleport implements Zero Trust on the application and workload level. Critical infrastructure resources do not need to listen on the network and are accessed via encrypted reverse tunnels. Multiple organizations can manage trust across teams and securely access shared infrastructure via role mapping.
What Our Customers Say
Learn More
Why Customers Adopt Teleport
Improve Productivity
Secure access to the infrastructure you need, when you need it
Protect Infrastructure
Remove secrets and standing privileges as attack services
Streamline Compliance
FedRAMP, SOC 2, HIPAA, PCI, ISO 27001