
TELEPORT ACCESS PLATFORM
Teleport Identity
Harden your infrastructure with identity
governance and security

Trusted by Market Leaders




















Cyber Attacks Have Shifted to Identity
Ranging from credential theft to human error, incidents of cloud cybersecurity breaches that involve identity and human factors are on the rise each year.
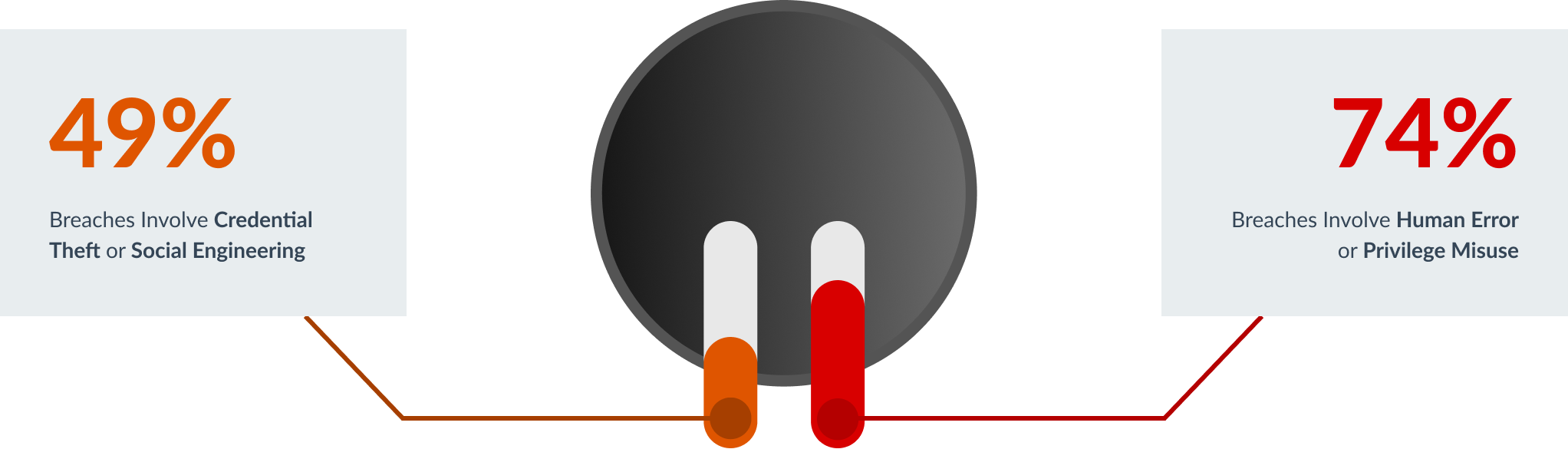
Protect your infrastructure with Teleport Access. Harden it with Teleport Identity.
Eliminate Weak Access Patterns
Access Monitoring & Response
Detect overly broad privileges and inspect sessions that are not using strong protection, such as multi-factor authentication or device trust.
Alerting and Response
Alert on access violations and purge unused permissions with automated access rules.
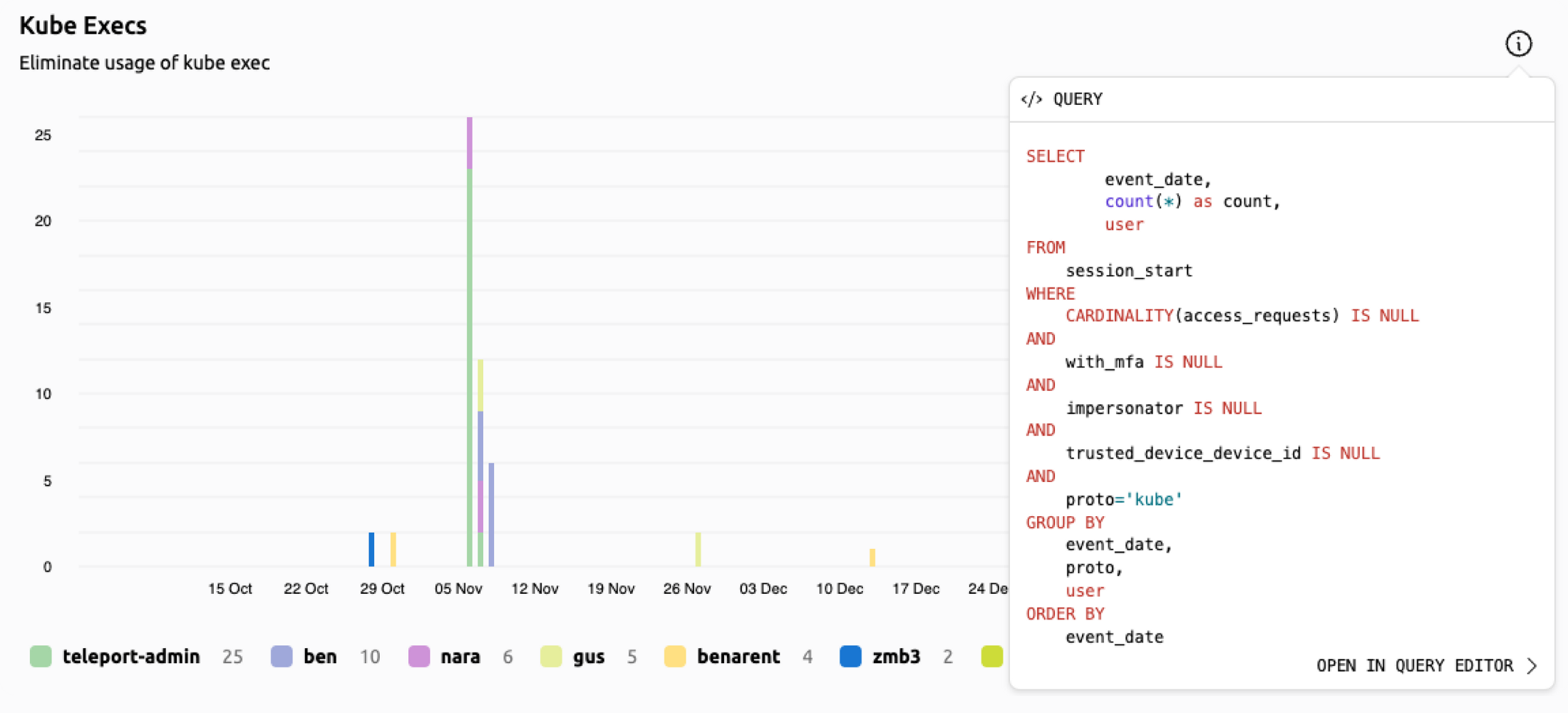
Reduce Attack Surface with Just-in-Time Access
Enforce principle of least privilege, granting only those privileges necessary to complete the task at hand and removing the need for super-privileged accounts.
Access Requests
Grant only those privileges necessary to complete the task at hand. Remove the need for super-privileged accounts. Engineers can use their preferred tools - kubectl, ssh, ansible, postgresql and many more.
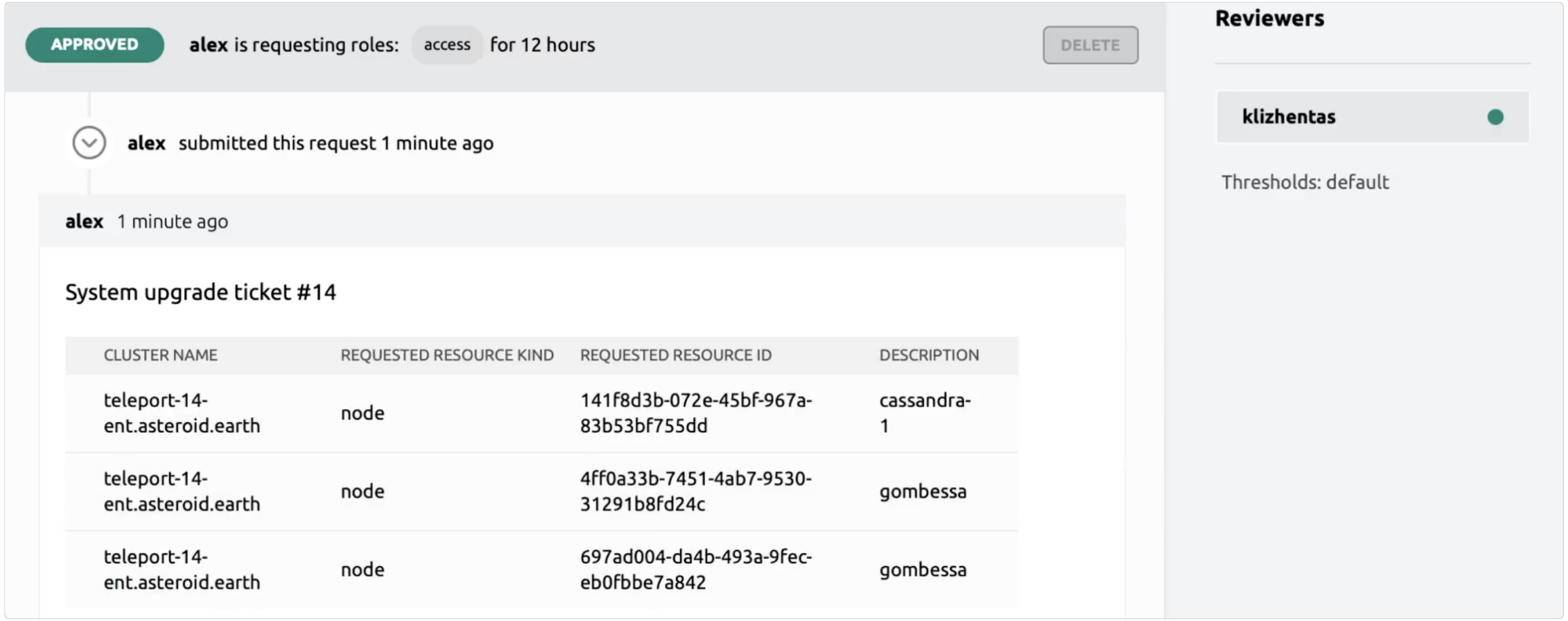
Access Reviews
Review access requests using Slack, PagerDuty, Microsoft Teams, Jira and ServiceNow. Assign managers, automate mandatory reviews, and implement custom review logic using our API and Go SDK.
Respond to Identity Threats
Take immediate action on suspicious or compromised identities and lock access instantly across your entire infrastructure.
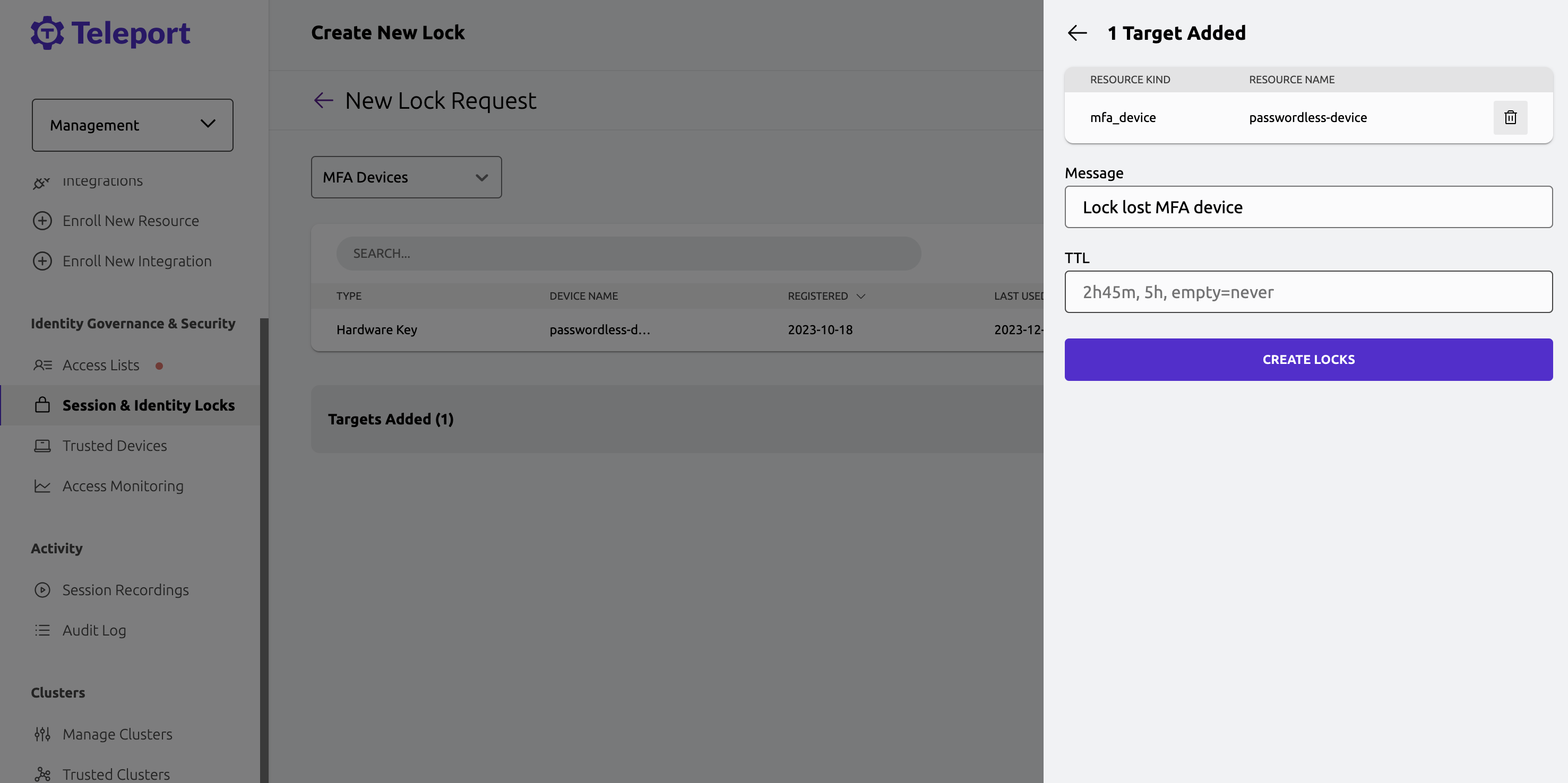
Identity Locking
Lock suspicious or compromised identities and stop all their activity across all protocols and services.
Access Management
Provision or deprovision access for all users and machines across all of your infrastructure.
Harden Identity Assurance
Require users and services to access your infrastructure only from current, registered devices. Pair required user and device identities to harden assurance of trusted identity.
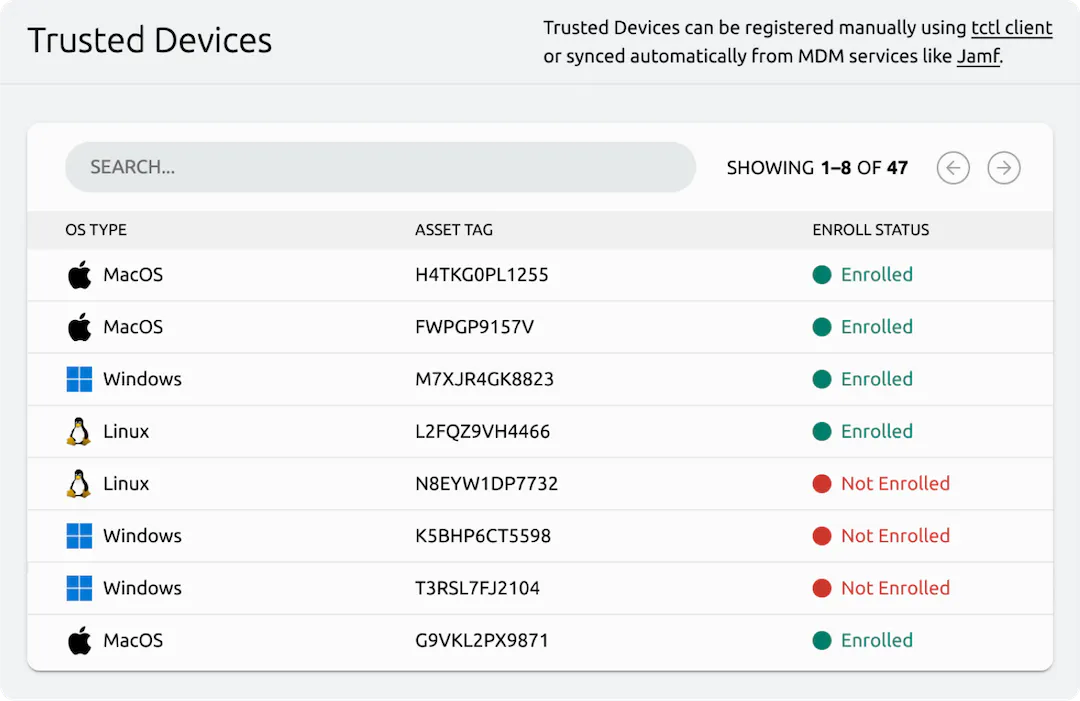
Device Trust
Require an up-to-date, registered device for each authentication. Teleport uses TPMs and secure enclaves to give every device a cryptographic identity. Getting started with Device Trust.
Require Paired User and Device Identity
Increase user identity assurance by restricting user access to resources exclusively via MDM-supervised or authorized devices.
What Our Customers Say
Learn More
TELEPORT ACCESS PLATFORM
Teleport Access
On-demand, least privileged access, with identity security and zero trust
Teleport Identity
Harden your infrastructure with identity governance and security
Teleport Policy
Unify and control access policies across all of your infrastructure