Introduction to Enrolling Servers
Teleport consolidates SSH access across all environments, decreases configuration complexity, supports industry best practices and compliance while giving complete visibility over all sessions and events.
Teleport server access is designed for the following kinds of scenarios:
- When up to a vast number of clusters must be managed using the command-line (
tsh) or programmatically (through the Teleport API) and you want to simplify your stack, security, and configuration complexity. - When security team members must track and audit every user session.
- When Teleport users require a complete, dedicated, and secure SSH option (Teleport Node running in SSH mode) and more than a certificate authority (Teleport Auth) with proxy (Teleport Proxy).
- When resource and network security must be maximized: SSH certificates over secret keys, multi-factor authentication (MFA), Single Sign-On (SSO), and short-lived certificates.
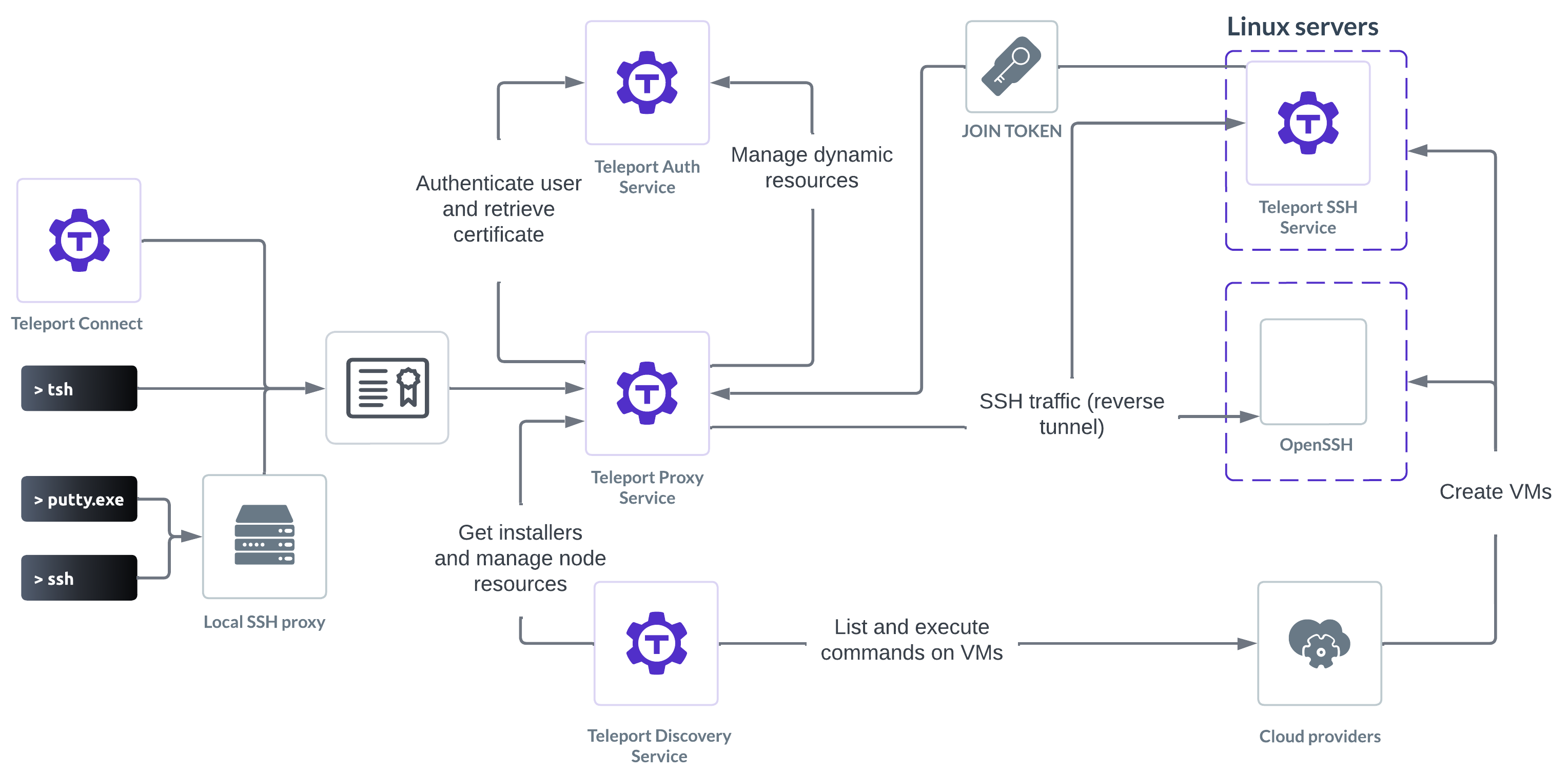
Getting started
- Get started: Get started using Teleport server access in 10 minutes. Server access for most common SSH use-cases.
Guides
- Using Teleport with PAM: How to configure Teleport SSH with PAM (Pluggable Authentication Modules).
- Agentless OpenSSH Integration: How to use Teleport in agentless mode on systems with OpenSSH and
sshd. - Recording Proxy Mode: How to use Teleport Recording Proxy Mode to capture activity on OpenSSH servers.
- BPF Session Recording: How to use BPF to record SSH session commands, modified files and network connections.
- Restricted Session: How to configure and use Restricted Session to apply security policies to SSH sessions.
- Visual Studio Code: How to remotely develop with Visual Studio Code and Teleport.