What is WebAuthn?
WebAuthn is a web standard for secure, passwordless authentication allowing web servers to authenticate users with asymmetric cryptography instead of passwords.
Article Contents
WebAuthn is a web standard for secure, passwordless authentication allowing web servers to authenticate users with asymmetric cryptography instead of passwords. Users can use their own devices, like security keys or smartphones, to authenticate themselves to a website. By eliminating passwords altogether, WebAuthn provides a more secure and convenient way for users to access their personal information and accounts online.
WebAuthn, or Web Authentication API, is a standard developed by W3C and FIDO, launched in 2018, and became the official web standard in 2019 for passwordless logins, supported by Chrome, Firefox, Safari, Microsoft Edge, Windows 10 and Google Android.
WebAuthn security and convenience
WebAuthn is very secure in that it uses public key cryptography ensuring that only a user’s device can authenticate that user to a website and that the keys involved are specific to that origin or domain. This removes the many risks that revolve around passwords and the broader danger of phishing attacks. In addition, the fact that users no longer need to remember or maintain complex passwords make WebAuthn very convenient as they can simply use their device to authenticate. And as a bonus, WebAuthn is considered multifactor in itself because it’s something you have (their device) with something you are (biometric).
WebAuthn utilizes asymmetric, public key cryptography. This means upon initial registration two keys are created:
- A public key, which can be shared publicly and will be encrypted and stored by the website or service.
- A private key, which should always remain private, is stored locally in a trusted platform module and can’t be stolen like a password. The private key is used to sign an attestation from the user, verifying that the user is indeed who they say they are.
The public key can be decrypted only with the private key, and the public key alone cannot mathematically reveal the private key in any way.
How WebAuthn works
Now there are three key terms that must be defined to understand how the WebAuthn flow works:
- Relying party: This is a website or application that needs to authenticate users.
- Client/platform: This is an operating system or browser used by the user to authenticate.
- Authenticator: This is a mechanism that accepts the user input to authenticate the user’s credential for the relying party. It can be an internal authenticator such as a secure enclave via fingerprint reader or facial recognition, or an external authenticator such as a Yubikey connected to your computer.
Let’s imagine that a user named Alice wants to sign up for online banking with a new bank that supports WebAuthn. Here’s what the registration flow would look like using our key terms above:
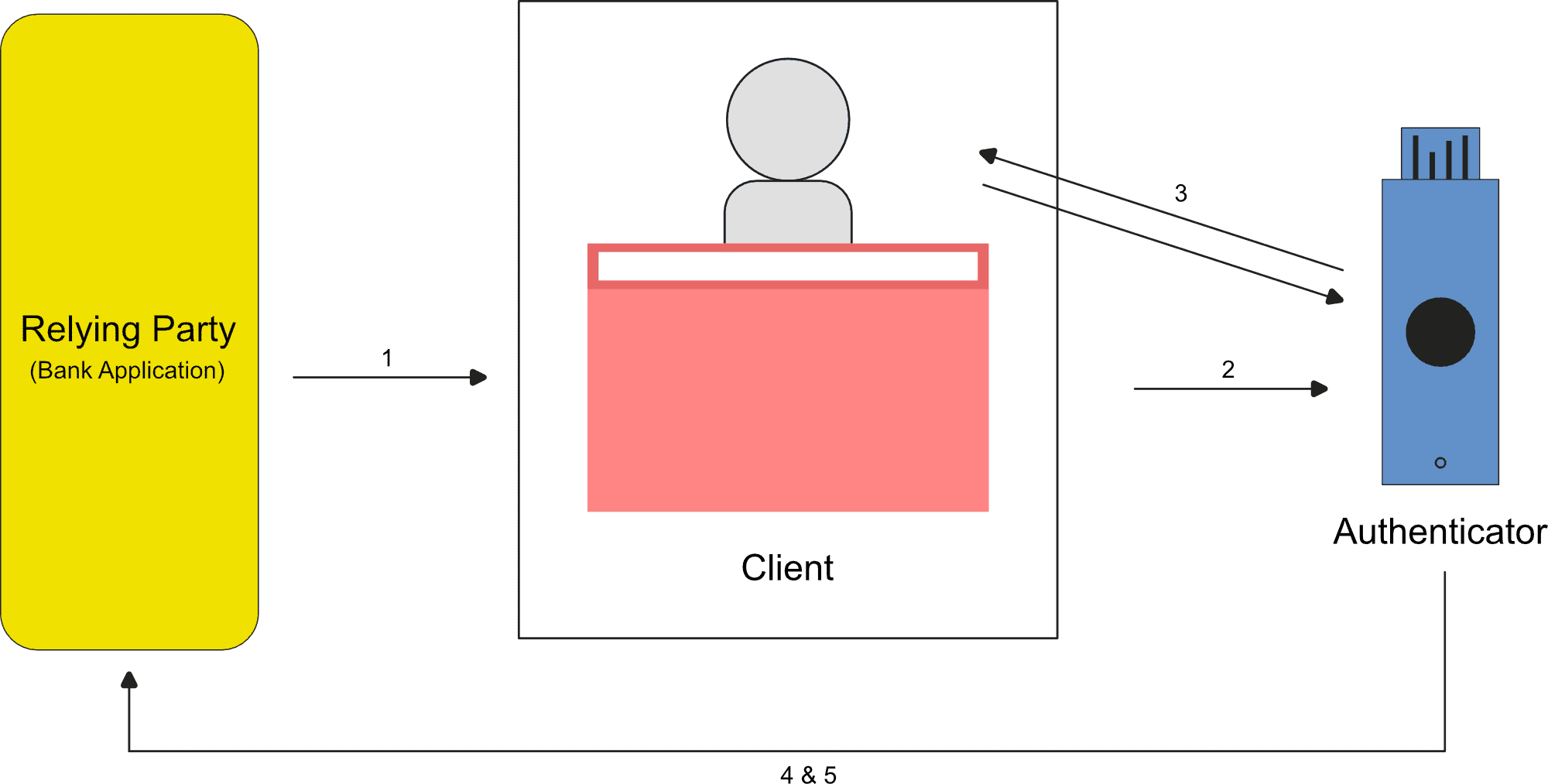
- Alice initiates the action to register a new account with her bank. The relying party (bank application) makes a create request to the client (Alice’s browser) with some data such as user information, information on the relying party, and a challenge (needed to prevent “replay attacks”).
- The request, with its data, gets sent to the authenticator.
- The authenticator prompts the user to take some action (tap a security key, touch the fingerprint module) upon which it will create a unique set of credentials, a public and private key pair.
- The authenticator sends the public key to the relying party along with other data verifying the origin that came in the request.
- The relying party verifies the response and saves the user data together with the new public key. The origin data it receives from the request helps to prevent phishing attacks. The registration is now finished.
Going forward when Alice logs in, instead of a create request, a get request will be sent to the client, and instead of the authenticator creating unique keys, the authenticator sends a response signed with the private key, and the relying party will verify.
While the WebAuthn standard is fairly easy to implement given its well-defined API, it has not taken off as fast with developers and major applications. In addition, when it is utilized, it’s often not as intended in its full potential, but merely as a multifactor add-on. With support for Passkeys (which use the WebAuthn API) in the rollout of iOS16, Ventura, and Windows 11, we look to see more adoption this year. Teleport is ahead of the curve already as WebAuthn was added in Teleport 10 with Passkey support now in place. You can try it for free today.