
TELEPORT IDENTITY SECURITY
Expose and Eliminate Hidden Identity Risk
Teleport Identity Security traces the full chain of identity across Okta, Teleport, AWS, GitHub, and more, turning fragmented logs into actionable insight and enforceable control.
TRUSTED BY LEADERS




















THE REALTIME CHALLENGE
Attackers Don’t Break In. They Log In.
Traditional security tools can’t see or protect identity-level activity in real time across infrastructure.
Compromised Identities
Attackers use SSO bypass, token replay, or compromised agents to impersonate valid users.
Over-Broad Permissions
Standing privileges, long-lived cloud roles, and unused permissions open lateral paths everywhere.
Invisible Non-Human Actors
AI Agents, bots, CI jobs, microservices operate with little oversight or identity attribution.
Fragmented Logs & Tools
SIEM, CNAPPS, EDR, cloud logs, and PAM tools all show partial pictures of activity in the system.

Fifteen minutes after deploying Teleport Identity Security, Teleport flagged two engineers whose accounts quietly retained maintainer rights across 1,800 repos—far beyond their intended read-only access.
CISO, Fortune 500 Company
Teleport Identity Security
Teleport inspects identity activity and access context as identities move across cloud, code and infrastructure, to surface hidden identity risk. Detect threats in real time, improve security posture, and lock compromised users — all from one platform.
Identity-Aware Detection
Automated Protection
Identity Chain Visibility
AI Session Summaries
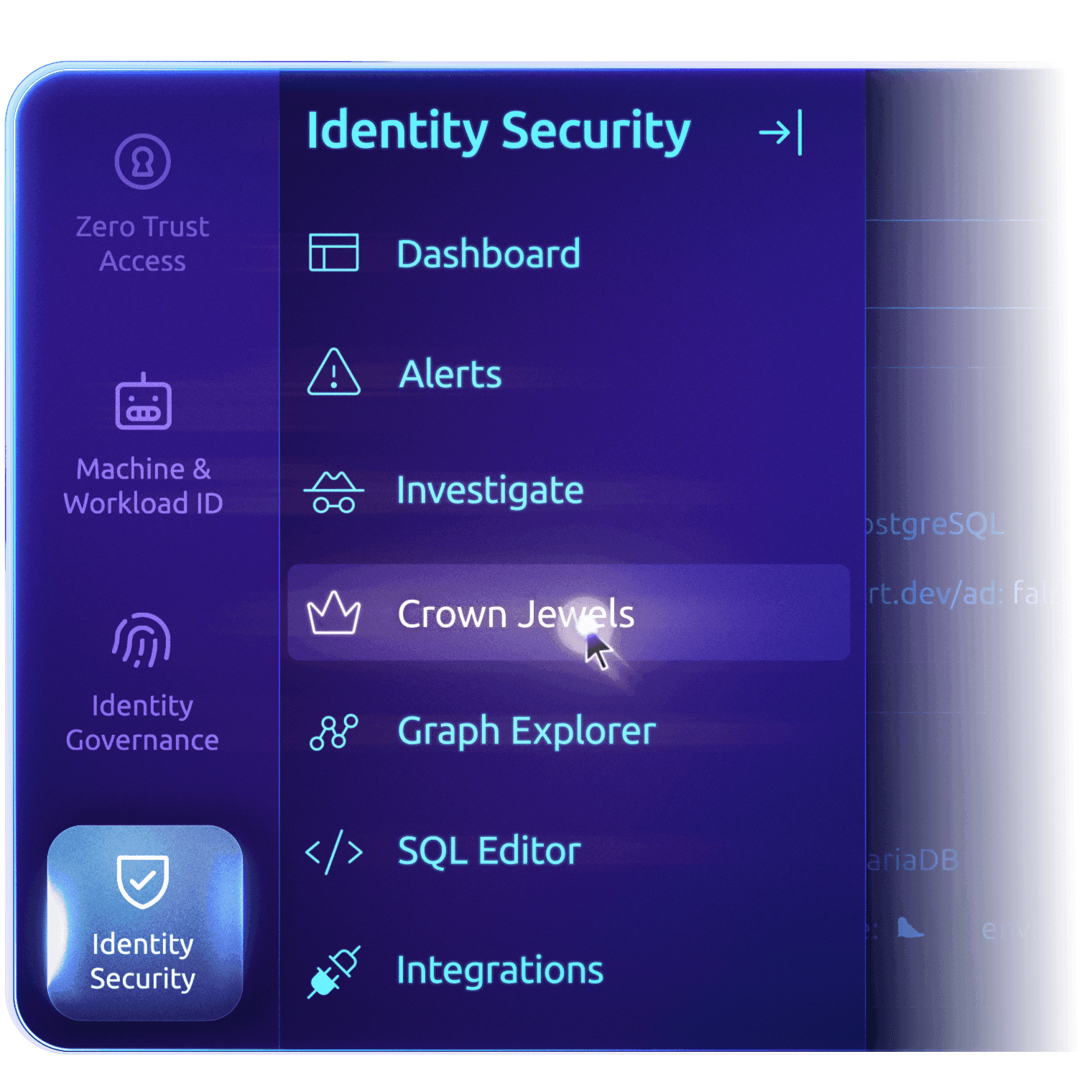
Crown Jewels
Detect Suspicious Activity in Real Time
Continuously analyze identity behavior across infrastructure to detect and investigate privilege escalation, lateral movement, and other high-risk behaviors quickly. Correlate and alert on more than 50+ identity vulnerability types:
Unusual identity/access patterns
Risky changes to permissions or roles
Devices that fail posture checks
Long-running or inactive sessions
Pathways spanning users, bots, and workload

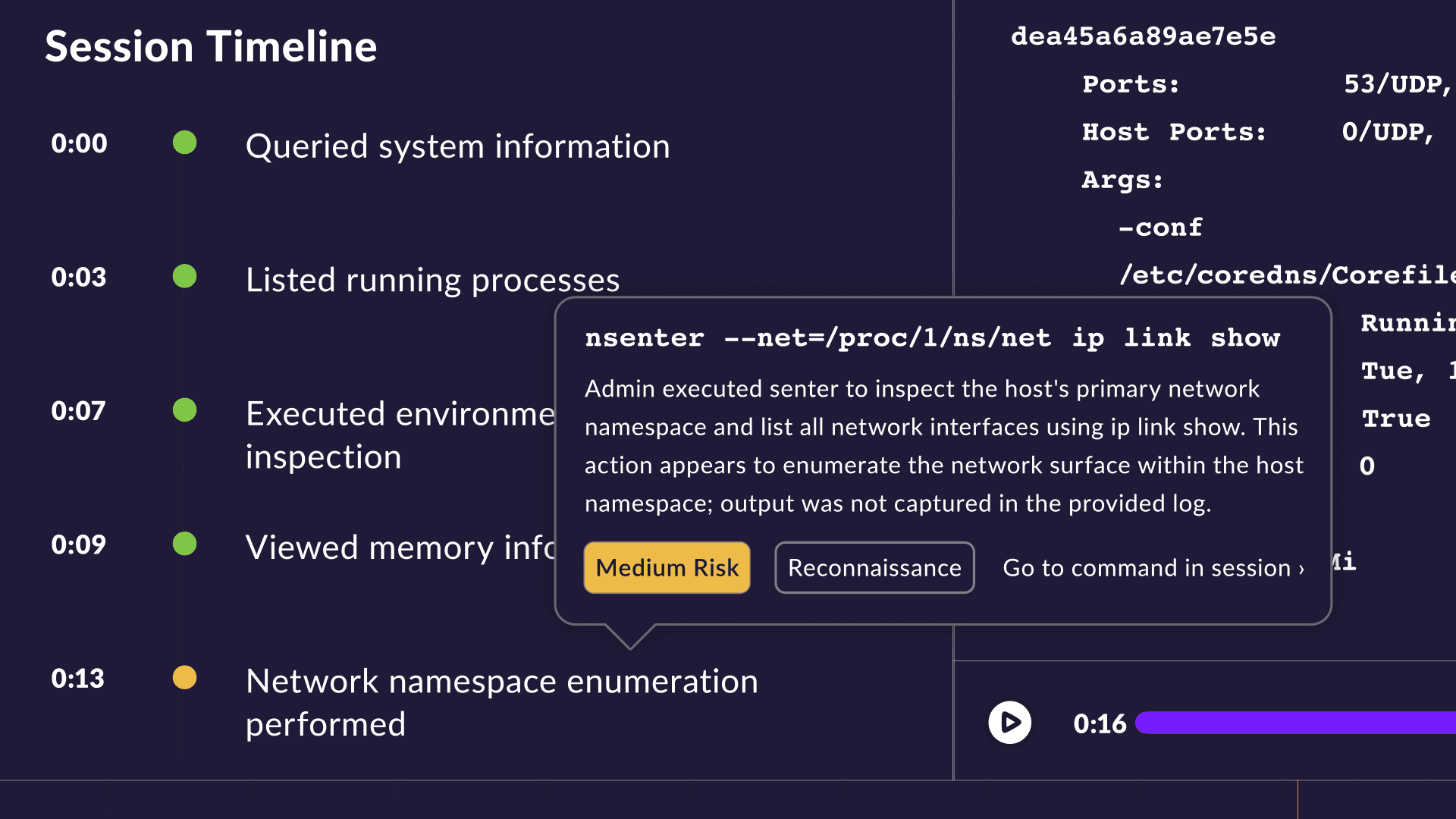
Trace Identity Chain of Activity
Teleport creates a unified view of how identities move across infrastructure, cloud and code — accelerating forensic investigation and audit preparation. Quickly reconstruct incidents with AI-generated timelines. Telemetry includes:
Identity-linked activity logs
Session recordings
Approval and JIT access event history
Cloud access events (via integrations)
Device posture data
Machine and workload identity issuances and renewals
Accelerate Investigations with AI‑Powered Session Summaries
Give security and platform teams AI-powered summaries, showing what happened during an identity’s access session across SSH, Kubernetes, database, cloud console, and more without manual audit log reviews or session replays. Investigate incidents, reduce analyst workloads, and improve clarity during security audits with instant insight into:
Which commands, queries, or operations were executed
Whether privileged or sensitive actions occurred
Which resources, clusters, or environments were accessed
Whether device posture, MFA, or policy checks were satisfied
Session context against the identity's broader activity timeline
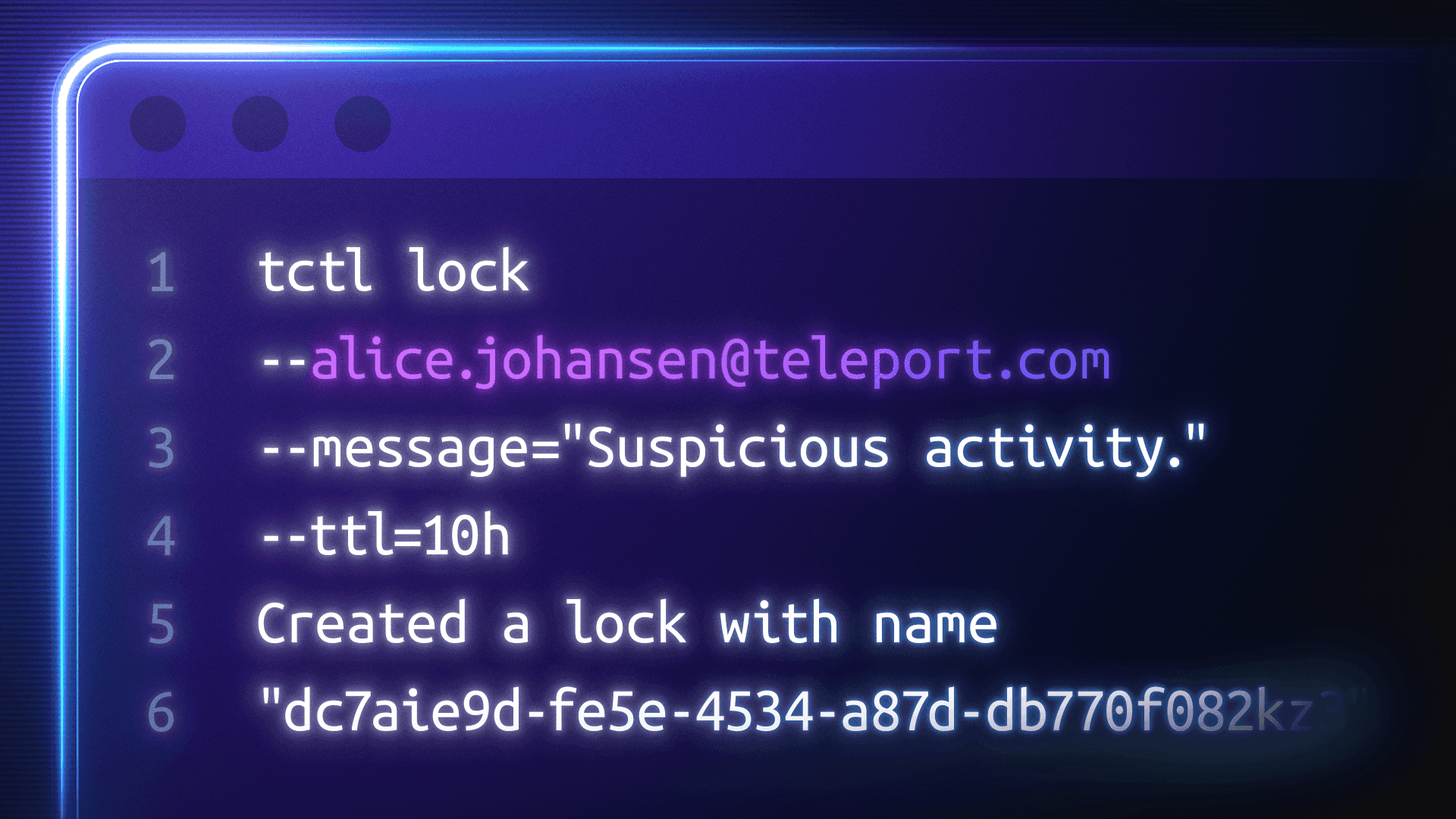
Respond Faster to Identity Threats
Give security teams simple, powerful controls to quickly respond to identity risks across infrastructure, including compromised access credentials, rogue automation, or misconfigured privileges.
Terminate active sessions for SSH, Kubernetes, databases, cloud consoles, or other Teleport-managed access
Lock identities (human or machine) to prevent new connections
Block non-compliant endpoints with device trust
Notify teams via Slack, PagerDuty, or similar integrations
Route events into your SIEM for correlated analysis
Visualize & Query
Access Relationships
Explore allow and deny paths with Access Graph for real-time identity-to-resource relationships. Dive deeper with custom queries in SQL Editor across roles, groups, and permissions.
Eliminate High-Risk Access Paths
Protect Crown Jewels
Designate your most critical assets to prioritize monitoring and alerts. Track changes in access paths, permissions, and user behavior to surface high-risk activity fast.
Reveal Shadow Access Paths
Scan for unmanaged SSH keys, expired credentials, and unauthorized identity-to-resource connections that create backdoor access risks.
Query Standing Privileges
Quickly identify and address accounts with lingering standing privileges. Convert sensitive access paths to just-in-time access requests.
Improve Security Posture
Govern → Access → Monitor → Respond
Teleport unifies identity governance, access, and security operations in a continuous loop that enforces least privilege and improves security posture across your engineering environment.
1
Govern identities
with SCIM provisioning, JIT access, and access reviews
2
Control access
to servers, clusters, databases, cloud consoles, and workloads
3
Monitor identity activity
across cloud and infrastructure
4
Respond quickly
with session termination and identity locking
What Our Customers Say
Teleport is a strategic technology partner as they help our joint customers to scale their AWS resources in a secure manner. With Teleport’s Identity-Native Infrastructure Access solution, DevOps Engineers get a frictionless experience managing infrastructure that doesn’t require secrets while implementing zero trust architecture in AWS.
We use Teleport Access Requests in combination with Auth0 to easily manage access to our infrastructure. Prior to Teleport, we manually managed SSH keys and a bastion machine and it was an organizational nightmare.
We used to go through multiple steps just to access cloud resources, and now it happens almost instantly. Our engineers are really happy with the significant improvement in their workflow.
Teleport’s vision for Infrastructure Identity is a game-changer for securing hybrid infrastructure.
Teleport is a strategic technology partner as they help our joint customers to scale their AWS resources in a secure manner. With Teleport’s Identity-Native Infrastructure Access solution, DevOps Engineers get a frictionless experience managing infrastructure that doesn’t require secrets while implementing zero trust architecture in AWS.
We use Teleport Access Requests in combination with Auth0 to easily manage access to our infrastructure. Prior to Teleport, we manually managed SSH keys and a bastion machine and it was an organizational nightmare.
We used to go through multiple steps just to access cloud resources, and now it happens almost instantly. Our engineers are really happy with the significant improvement in their workflow.
Teleport’s vision for Infrastructure Identity is a game-changer for securing hybrid infrastructure.
With Teleport, we were even able to close the Kubernetes API without losing access for our engineers or automation tools. That alone was a huge win.
Teleport allows us to comply with the regulatory hurdles that come with running an international stock exchange. The use of bastion hosts, integration with our identity service and auditing capabilities give us a compliant way to access our internal infrastructure.
The Infrastructure Identity solution from Teleport offers a glimpse into the future of more secure, more resilient, and higher-velocity enterprise computing.
Teleport has made obtaining a FedRAMP-Moderate ATO that much more achievable via their FIPS 140-2 endpoints, ease in integration with our SSO and MFA , and the view into audit logs of remote connection sessions provide the appropriate insight for Continuous Monitoring.
Over the many years of using Teleport, it's been an essential piece of my infrastructure to help secure access, and centralize my infrastructure into one dashboard, without having to jump around… I'm not sure how I could go without it.
With Teleport, we were even able to close the Kubernetes API without losing access for our engineers or automation tools. That alone was a huge win.
Teleport allows us to comply with the regulatory hurdles that come with running an international stock exchange. The use of bastion hosts, integration with our identity service and auditing capabilities give us a compliant way to access our internal infrastructure.
The Infrastructure Identity solution from Teleport offers a glimpse into the future of more secure, more resilient, and higher-velocity enterprise computing.
Teleport has made obtaining a FedRAMP-Moderate ATO that much more achievable via their FIPS 140-2 endpoints, ease in integration with our SSO and MFA , and the view into audit logs of remote connection sessions provide the appropriate insight for Continuous Monitoring.
Over the many years of using Teleport, it's been an essential piece of my infrastructure to help secure access, and centralize my infrastructure into one dashboard, without having to jump around… I'm not sure how I could go without it.

Additional Resources
Teleport Identity Security
Discover how Teleport Identity Security works, including key concepts, use cases, and more.
GoTo Secures and Simplifies Cloud Access with Teleport
Learn how GoTo’s engineering team improved compliance and security visibility with Teleport — simplifying audits across a global multi-cloud ecosystem.
From Cost Center to Business Catalyst: Making Identity Security Visible and Valuable
In this report from HyperFRAME Research, discover how unified identity security can become a key driver of business growth.
Frequently Asked Questions
What is Teleport Identity Security?
Teleport Identity Security uses Access Graph and related features to centralize logs, visualize identity-to-resource relationships, and help you answer questions like who can access what and what actions they perform.
What kinds of identity threats can Teleport spot in real time?
Identity Security monitors identity-related activity and access paths so you can detect anomalous access patterns, over-privileged accounts, insecure SSH keys, and changes to critical resources.
Does Teleport scale across large, multi-cloud engineering teams?
Teleport includes documented guidance for large-scale deployments and supports multi-cloud infrastructure access across SSH, databases, Kubernetes, and cloud providers.
Can Teleport plug into my SIEM and existing security tools?
Teleport can export audit events to SIEM tools and unifies logs from systems like Okta, AWS, and GitHub so existing detection and response workflows can use richer identity context.











