
Teleport
Run the Slack Access Request Plugin
- Version 16.x
- Version 15.x
- Version 14.x
- Version 13.x
- Older Versions
This guide will explain how to set up Slack to receive Access Request messages from Teleport. Teleport's Slack integration notifies individuals and channels of Access Requests. Users are then directed to log in to the Teleport cluster where they can approve and deny Access Requests, making it easier to implement security best practices without compromising productivity.
In Teleport Enterprise Cloud, Teleport manages the Slack integration for you, and you can enroll the Slack integration from the Teleport Web UI.
Visit the Teleport Web UI and click Access Management on the menu bar at the top of the screen.
On the left sidebar, click Enroll New Integration to visit the "Enroll New Integration" page:
On the "Select Integration Type" menu, click the tile for your integration. You will see a page with instructions to set up the integration, as well as a form that you can use to configure the integration.
Here is an example of sending an Access Request via Teleport's Slack plugin:
Prerequisites
-
A running Teleport cluster. If you want to get started with Teleport, sign up for a free trial.
-
The Enterprise
tctladmin tool andtshclient tool version >= 15.2.2, which you can download from your Teleport account workspace or the Teleport Enterprise Cloud Downloads page.
Recommended: Configure Machine ID to provide short-lived Teleport
credentials to the plugin. Before following this guide, follow a Machine ID
deployment guide to run the tbot binary on
your infrastructure.
- Slack admin privileges to create an app and install it to your workspace. Your Slack profile must have the "Workspace Owner" or "Workspace Admin" banner below your profile picture.
- Either a Linux host or Kubernetes cluster where you will run the Slack plugin.
To check that you can connect to your Teleport cluster, sign in with tsh login, then
verify that you can run tctl commands using your current credentials.
tctl is supported on macOS and Linux machines.
For example:
tsh login --proxy=teleport.example.com --user=[email protected]tctl statusCluster teleport.example.com
Version 15.2.2
CA pin sha256:abdc1245efgh5678abdc1245efgh5678abdc1245efgh5678abdc1245efgh5678
If you can connect to the cluster and run the tctl status command, you can use your
current credentials to run subsequent tctl commands from your workstation.
If you host your own Teleport cluster, you can also run tctl commands on the computer that
hosts the Teleport Auth Service for full permissions.
Step 1/8. Define RBAC resources
Before you set up the Slack plugin, you will need to enable Role Access Requests in your Teleport cluster.
For the purpose of this guide, we will define an editor-requester role, which
can request the built-in editor role, and an editor-reviewer role that can
review requests for the editor role.
Create a file called editor-request-rbac.yaml with the following content:
kind: role
version: v5
metadata:
name: editor-reviewer
spec:
allow:
review_requests:
roles: ['editor']
---
kind: role
version: v5
metadata:
name: editor-requester
spec:
allow:
request:
roles: ['editor']
thresholds:
- approve: 1
deny: 1
Create the roles you defined:
tctl create -f editor-request-rbac.yamlrole 'editor-reviewer' has been createdrole 'editor-requester' has been created
Allow yourself to review requests by users with the editor-requester role by
assigning yourself the editor-reviewer role.
Assign the editor-reviewer role to your Teleport user by running the appropriate
commands for your authentication provider:
-
Retrieve your local user's roles as a comma-separated list:
ROLES=$(tsh status -f json | jq -r '.active.roles | join(",")') -
Edit your local user to add the new role:
tctl users update $(tsh status -f json | jq -r '.active.username') \ --set-roles "${ROLES?},editor-reviewer" -
Sign out of the Teleport cluster and sign in again to assume the new role.
-
Retrieve your
githubauthentication connector:tctl get github/github --with-secrets > github.yamlNote that the
--with-secretsflag adds the value ofspec.signing_key_pair.private_keyto thegithub.yamlfile. Because this key contains a sensitive value, you should remove the github.yaml file immediately after updating the resource. -
Edit
github.yaml, addingeditor-reviewerto theteams_to_rolessection.The team you should map to this role depends on how you have designed your organization's role-based access controls (RBAC). However, the team must include your user account and should be the smallest team possible within your organization.
Here is an example:
teams_to_roles: - organization: octocats team: admins roles: - access + - editor-reviewer -
Apply your changes:
tctl create -f github.yaml -
Sign out of the Teleport cluster and sign in again to assume the new role.
-
Retrieve your
samlconfiguration resource:tctl get --with-secrets saml/mysaml > saml.yamlNote that the
--with-secretsflag adds the value ofspec.signing_key_pair.private_keyto thesaml.yamlfile. Because this key contains a sensitive value, you should remove the saml.yaml file immediately after updating the resource. -
Edit
saml.yaml, addingeditor-reviewerto theattributes_to_rolessection.The attribute you should map to this role depends on how you have designed your organization's role-based access controls (RBAC). However, the group must include your user account and should be the smallest group possible within your organization.
Here is an example:
attributes_to_roles: - name: "groups" value: "my-group" roles: - access + - editor-reviewer -
Apply your changes:
tctl create -f saml.yaml -
Sign out of the Teleport cluster and sign in again to assume the new role.
-
Retrieve your
oidcconfiguration resource:tctl get oidc/myoidc --with-secrets > oidc.yamlNote that the
--with-secretsflag adds the value ofspec.signing_key_pair.private_keyto theoidc.yamlfile. Because this key contains a sensitive value, you should remove the oidc.yaml file immediately after updating the resource. -
Edit
oidc.yaml, addingeditor-reviewerto theclaims_to_rolessection.The claim you should map to this role depends on how you have designed your organization's role-based access controls (RBAC). However, the group must include your user account and should be the smallest group possible within your organization.
Here is an example:
claims_to_roles: - name: "groups" value: "my-group" roles: - access + - editor-reviewer -
Apply your changes:
tctl create -f oidc.yaml -
Sign out of the Teleport cluster and sign in again to assume the new role.
Create a user called myuser who has the editor-requester role. This user
cannot edit your cluster configuration unless they request the editor role:
tctl users add myuser --roles=editor-requester
tctl will print an invitation URL to your terminal. Visit the URL and log in
as myuser for the first time, registering credentials as configured for your
Teleport cluster.
Later in this guide, you will have myuser request the editor role so you can
review the request using the Teleport plugin.
Step 2/8. Install the Teleport Slack plugin
We currently only provide linux-amd64 binaries. You can also compile these
plugins from source. You can run the plugin from a remote host or your local
development machine.
curl -L -O https://get.gravitational.com/teleport-access-slack-v15.2.2-linux-amd64-bin.tar.gztar -xzf teleport-access-slack-v15.2.2-linux-amd64-bin.tar.gzcd teleport-access-slacksudo ./install
Make sure the binary is installed:
teleport-slack versionteleport-slack v15.2.2 git:teleport-slack-v15.2.2-fffffffff go1.21
We currently only provide Docker images for linux-amd64.
Pull the Docker image for the latest access request plugin by running the following command:
docker pull public.ecr.aws/gravitational/teleport-plugin-slack:15.2.2
Make sure the plugin is installed by running the following command:
docker run public.ecr.aws/gravitational/teleport-plugin-slack:15.2.2 versionteleport-slack v15.2.2 git:teleport-slack-v15.2.2-api/14.0.0-gd1e081e 1.21
For a list of available tags, visit Amazon ECR Public Gallery.
To install from source you need git and go installed. If you do not have Go
installed, visit the Go downloads page.
git clone https://github.com/gravitational/teleport-plugins.gitcd teleport-plugins/access/slackmake
Move the teleport-slack binary into your PATH.
Make sure the binary is installed:
teleport-slack versionteleport-slack v15.2.2 git:teleport-slack-v15.2.2-fffffffff go1.21
Allow Helm to install charts that are hosted in the Teleport Helm repository:
helm repo add teleport https://charts.releases.teleport.dev
Update the cache of charts from the remote repository:
helm repo update
Step 3/8. Create a user and role for the plugin
Teleport's Access Request plugins authenticate to your Teleport cluster as a user with permissions to list and read Access Requests. This way, plugins can retrieve Access Requests from the Teleport Auth Service and present them to reviewers.
Define a user and role called access-plugin by adding the following content to
a file called access-plugin.yaml:
kind: role
version: v5
metadata:
name: access-plugin
spec:
allow:
rules:
- resources: ['access_request']
verbs: ['list', 'read']
- resources: ['access_plugin_data']
verbs: ['update']
# In order to provide access list review reminders, permissions to list and read access lists
# are necessary. This is currently only supported for a subset of plugins.
- resources: ['access_list']
verbs: ['list', 'read']
# Optional: To display user-friendly names in resource-based Access
# Requests instead of resource IDs, the plugin also needs permission
# to list the resources being requested. Include this along with the
# list-access-request-resources role definition.
review_requests:
preview_as_roles:
- list-access-request-resources
---
kind: user
metadata:
name: access-plugin
spec:
roles: ['access-plugin']
version: v2
---
# Optional, for displaying friendly names of resources. Resource types and
# labels can be further limited to only the resources that access can be
# requested to.
kind: role
version: v5
metadata:
name: list-access-request-resources
spec:
allow:
rules:
- resources: ['node', 'app', 'db', 'kube_cluster']
verbs: ['list', 'read']
node_labels:
'*': '*'
kubernetes_labels:
'*': '*'
db_labels:
'*': '*'
app_labels:
'*': '*'
group_labels:
'*': '*'
Create the user and role:
tctl create -f access-plugin.yaml
As with all Teleport users, the Teleport Auth Service authenticates the
access-plugin user by issuing short-lived TLS credentials. In this case, we
will need to request the credentials manually by impersonating the
access-plugin role and user.
If you are running a self-hosted Teleport Enterprise deployment and are using
tctl from the Auth Service host, you will already have impersonation
privileges.
To grant your user impersonation privileges for access-plugin, define a role
called access-plugin-impersonator by pasting the following YAML document into
a file called access-plugin-impersonator.yaml:
kind: role
version: v5
metadata:
name: access-plugin-impersonator
spec:
allow:
impersonate:
roles:
- access-plugin
users:
- access-plugin
Create the access-plugin-impersonator role:
tctl create -f access-plugin-impersonator.yaml
If you are providing identity files to the plugin with Machine ID, assign the
access-plugin role to the Machine ID bot user. Otherwise, assign this role to
the user you plan to use to generate credentials for the access-plugin role
and user:
Assign the access-plugin-impersonator role to your Teleport user by running the appropriate
commands for your authentication provider:
-
Retrieve your local user's roles as a comma-separated list:
ROLES=$(tsh status -f json | jq -r '.active.roles | join(",")') -
Edit your local user to add the new role:
tctl users update $(tsh status -f json | jq -r '.active.username') \ --set-roles "${ROLES?},access-plugin-impersonator" -
Sign out of the Teleport cluster and sign in again to assume the new role.
-
Retrieve your
githubauthentication connector:tctl get github/github --with-secrets > github.yamlNote that the
--with-secretsflag adds the value ofspec.signing_key_pair.private_keyto thegithub.yamlfile. Because this key contains a sensitive value, you should remove the github.yaml file immediately after updating the resource. -
Edit
github.yaml, addingaccess-plugin-impersonatorto theteams_to_rolessection.The team you should map to this role depends on how you have designed your organization's role-based access controls (RBAC). However, the team must include your user account and should be the smallest team possible within your organization.
Here is an example:
teams_to_roles: - organization: octocats team: admins roles: - access + - access-plugin-impersonator -
Apply your changes:
tctl create -f github.yaml -
Sign out of the Teleport cluster and sign in again to assume the new role.
-
Retrieve your
samlconfiguration resource:tctl get --with-secrets saml/mysaml > saml.yamlNote that the
--with-secretsflag adds the value ofspec.signing_key_pair.private_keyto thesaml.yamlfile. Because this key contains a sensitive value, you should remove the saml.yaml file immediately after updating the resource. -
Edit
saml.yaml, addingaccess-plugin-impersonatorto theattributes_to_rolessection.The attribute you should map to this role depends on how you have designed your organization's role-based access controls (RBAC). However, the group must include your user account and should be the smallest group possible within your organization.
Here is an example:
attributes_to_roles: - name: "groups" value: "my-group" roles: - access + - access-plugin-impersonator -
Apply your changes:
tctl create -f saml.yaml -
Sign out of the Teleport cluster and sign in again to assume the new role.
-
Retrieve your
oidcconfiguration resource:tctl get oidc/myoidc --with-secrets > oidc.yamlNote that the
--with-secretsflag adds the value ofspec.signing_key_pair.private_keyto theoidc.yamlfile. Because this key contains a sensitive value, you should remove the oidc.yaml file immediately after updating the resource. -
Edit
oidc.yaml, addingaccess-plugin-impersonatorto theclaims_to_rolessection.The claim you should map to this role depends on how you have designed your organization's role-based access controls (RBAC). However, the group must include your user account and should be the smallest group possible within your organization.
Here is an example:
claims_to_roles: - name: "groups" value: "my-group" roles: - access + - access-plugin-impersonator -
Apply your changes:
tctl create -f oidc.yaml -
Sign out of the Teleport cluster and sign in again to assume the new role.
You will now be able to generate signed certificates for the access-plugin
role and user.
Step 4/8. Export the access plugin identity
Give the plugin access to a Teleport identity file. We recommend using Machine
ID for this in order to produce short-lived identity files that are less
dangerous if exfiltrated, though in demo deployments, you can generate
longer-lived identity files with tctl:
Configure tbot with an output that will produce the credentials needed by
the plugin. As the plugin will be accessing the Teleport API, the correct
output type to use is identity.
For this guide, the directory destination will be used. This will write these
credentials to a specified directory on disk. Ensure that this directory can
be written to by the Linux user that tbot runs as, and that it can be read by
the Linux user that the plugin will run as.
Modify your tbot configuration to add an identity output.
If running tbot on a Linux server, use the directory output to write
identity files to the /opt/machine-id directory:
outputs:
- type: identity
destination:
type: directory
# For this guide, /opt/machine-id is used as the destination directory.
# You may wish to customize this. Multiple outputs cannot share the same
# destination.
path: /opt/machine-id
If running tbot on Kubernetes, write the identity file to Kubernetes secret
instead:
outputs:
- type: identity
destination:
type: kubernetes_secret
name: teleport-plugin-slack-identity
If operating tbot as a background service, restart it. If running tbot in
one-shot mode, execute it now.
You should now see an identity file under /opt/machine-id or a Kubernetes
secret named teleport-plugin-slack-identity. This contains the private key and signed
certificates needed by the plugin to authenticate with the Teleport Auth
Service.
Like all Teleport users, access-plugin needs signed credentials in order to
connect to your Teleport cluster. You will use the tctl auth sign command to
request these credentials.
The following tctl auth sign command impersonates the access-plugin user,
generates signed credentials, and writes an identity file to the local
directory:
tctl auth sign --user=access-plugin --out=identity
The plugin connects to the Teleport Auth Service's gRPC endpoint over TLS.
The identity file, identity, includes both TLS and SSH credentials. The
plugin uses the SSH credentials to connect to the Proxy Service, which
establishes a reverse tunnel connection to the Auth Service. The plugin
uses this reverse tunnel, along with your TLS credentials, to connect to the
Auth Service's gRPC endpoint.
By default, tctl auth sign produces certificates with a relatively short
lifetime. For production deployments, we suggest using Machine
ID to programmatically issue and renew
certificates for your plugin. See our Machine ID getting started
guide to learn more.
Note that you cannot issue certificates that are valid longer than your existing credentials.
For example, to issue certificates with a 1000-hour TTL, you must be logged in with a session that is
valid for at least 1000 hours. This means your user must have a role allowing
a max_session_ttl of at least 1000 hours (60000 minutes), and you must specify a --ttl
when logging in:
tsh login --proxy=teleport.example.com --ttl=60060
If you are running the plugin on a Linux server, create a data directory to hold certificate files for the plugin:
sudo mkdir -p /var/lib/teleport/api-credentialssudo mv identity /var/lib/teleport/plugins/api-credentials
If you are running the plugin on Kubernetes, Create a Kubernetes secret that contains the Teleport identity file:
kubectl -n teleport create secret generic --from-file=identity teleport-plugin-slack-identity
Once the Teleport credentials expire, you will need to renew them by running the
tctl auth sign command again.
Step 5/8. Register a Slack app
The Access Request plugin for Slack receives Access Request events from the Teleport Auth Service, formats them into Slack messages, and sends them to the Slack API to post them in your workspace. For this to work, you must register a new app with the Slack API.
Create your app
Visit https://api.slack.com/apps to create a new Slack app. Click "Create an App", then "From scratch". Fill in the form as shown below:
The "App Name" should be "Teleport". Click the "Development Slack Workspace" dropdown and choose the workspace where you would like to see Access Request messages.
Generate an OAuth token with scopes
Next, configure your application to authenticate to the Slack API. We will do this by generating an OAuth token that the plugin will present to the Slack API.
We will restrict the plugin to the narrowest possible permissions by using OAuth scopes. The Slack plugin needs to post messages to your workspace. It also needs to read usernames and email addresses in order to direct Access Request notifications from the Auth Service to the appropriate Teleport users in Slack.
After creating your app, the Slack website will open a console where you can specify configuration options. On the sidebar menu under "Features", click "OAuth & Permissions".
Scroll to the "Scopes" section and click "Add an OAuth Scope" for each of the following scopes:
chat:writeincoming-webhookusers:readusers:read.email
The result should look like this:
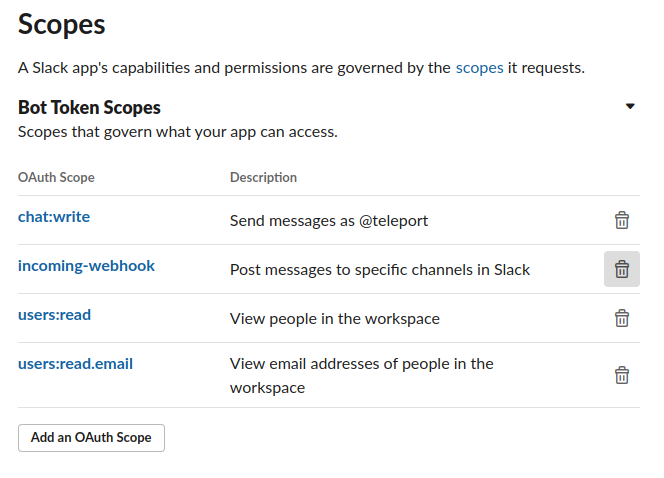
After you have configured scopes for your plugin, scroll back to the top of the OAuth & Permissions page, find the "OAuth Tokens for Your Workspace" section, and click "Install to Workspace". You will see a summary of the permission you configured for the Slack plugin earlier.
In "Where should Teleport post?", choose "Slackbot" as the default channel the plugin will post to. The plugin will post here when sending direct messages. Later in this guide, we will configure the plugin to post in other channels as well.
After submitting this form, you will see an OAuth token in the "OAuth & Permissions" tab under "Tokens for Your Workspace":
You will use this token later when configuring the Slack plugin.
Step 6/8. Configure the Teleport Slack plugin
At this point, the Teleport Slack plugin has the credentials it needs to communicate with your Teleport cluster and the Slack API. In this step, you will configure the Slack plugin to use these credentials. You will also configure the plugin to notify the right Slack channels when it receives an Access Request update.
Create a configuration file
The Teleport Slack plugin uses a configuration file in TOML format. Generate a
boilerplate configuration by running the following command (the plugin will not run
unless the config file is in /etc/teleport-slack.toml):
teleport-slack configure | sudo tee /etc/teleport-slack.toml > /dev/null
This should result in a configuration file like the one below:
# Example Slack plugin configuration TOML file
[teleport]
# Teleport Auth/Proxy Server address.
# addr = "example.com:3025"
#
# Should be port 3025 for Auth Server and 3080 or 443 for Proxy.
# For Teleport Cloud, should be in the form "your-account.teleport.sh:443".
# Credentials generated with `tctl auth sign`.
#
# When using --format=file:
# identity = "/var/lib/teleport/plugins/slack/identity" # Identity file
# refresh_identity = true # Refresh identity file on a periodic basis
#
# When using --format=tls:
# client_key = "/var/lib/teleport/plugins/slack/auth.key" # Teleport TLS secret key
# client_crt = "/var/lib/teleport/plugins/slack/auth.crt" # Teleport TLS certificate
# root_cas = "/var/lib/teleport/plugins/slack/auth.cas" # Teleport CA certs
[slack]
# Slack Bot OAuth token
# You can also use an absolute path to a token file, e.g.,
# "/var/lib/teleport/token"
token = "xoxb-11xx"
[role_to_recipients]
# Map roles to recipients.
#
# Provide slack user_email/channel recipients for access requests for specific roles.
# role.suggested_reviewers will automatically be treated as additional email recipients.
# "*" must be provided to match non-specified roles.
#
# "dev" = "devs-slack-channel"
# "*" = ["[email protected]", "admin-slack-channel"]
[log]
output = "stderr" # Logger output. Could be "stdout", "stderr" or "/var/lib/teleport/slack.log"
severity = "INFO" # Logger severity. Could be "INFO", "ERROR", "DEBUG" or "WARN".
The Slack Helm Chart uses a YAML values file to configure the plugin.
On your local workstation, create a file called teleport-slack-helm.yaml
based on the following example:
teleport:
# Teleport HTTPS Proxy Web Address, for Teleport Enterprise Cloud should be in the form "your-account.teleport.sh:443"
address: "teleport.example.com:443"
# Secret containing identity
identitySecretName: teleport-plugin-slack-identity
# Path within the secret containing the identity file.
identitySecretPath: identity
slack:
token: "xoxb-11xx" # Slack Bot OAuth token
# Mapping from role to recipients
roleToRecipients: []
# "dev": "devs-slack-channel"
# "*": ["[email protected]", "admin-slack-channel"]
Edit the configuration file
Open the configuration file created for the Teleport Slack plugin and update the following fields:
[teleport]
The Slack plugin uses this section to connect to your Teleport cluster:
addr: Include the hostname and HTTPS port of your Teleport Proxy Service
or Teleport Enterprise Cloud tenant (e.g., teleport.example.com:443 or
mytenant.teleport.sh:443).
identity: Fill this in with the path to the identity file you exported
earlier.
client_key, client_crt, root_cas: Comment these out, since we
are not using them in this configuration.
address: Include the hostname and HTTPS port of your Teleport Proxy Service
or Teleport Enterprise Cloud tenant (e.g., teleport.example.com:443 or
mytenant.teleport.sh:443).
identitySecretName: Fill in the identitySecretName field with the name
of the Kubernetes secret you created earlier.
identitySecretPath: Fill in the identitySecretPath field with the path
of the identity file within the Kubernetes secret. If you have followed the
instructions above, this will be identity.
If you are providing credentials to the plugin using a tbot binary that runs
on a Linux server, make sure the value of identity is the same as the path of
the identity file you configured tbot to generate, /opt/machine-id/identity.
Configure the plugin to periodically reload the identity file, ensuring that it does not attempt to connect to the Teleport Auth Service with expired credentials.
Add the following to the teleport section of the configuration:
refresh_identity = true
[slack]
token: Open https://api.slack.com/apps, find
the Slack app you created earlier, navigate to the "OAuth & Permissions" tab,
copy the "Bot User OAuth Token", and paste it into this field.
[role_to_recipients]
The role_to_recipients map configure the channels that the Slack plugin will
notify when a user requests access to a specific role. When the Slack plugin
receives an Access Request from the Auth Service, it will look up the role being
requested and identify the Slack channels to notify.
Here is an example of a role_to_recipients map:
[role_to_recipients]
"*" = "admin-slack-channel"
"dev" = ["dev-slack-channel", "admin-slack-channel"]
"dba" = "[email protected]"
In our Helm chart, the role_to_recipients field is called roleToRecipients
and uses the following format:
roleToRecipients:
"*": "admin-slack-channel"
"dev":
- "dev-slack-channel"
- "admin-slack-channel"
"dba": "[email protected]"
In the role_to_recipients map, each key is the name of a Teleport role. Each
value configures the Slack channel (or channels) to notify. The value can be a
single string or an array of strings. Each string must be either the name of a
Slack channel (including a user's direct message channel) or the email address
of a Slack user. If the recipient is an email address, the Slack plugin will
use that email address to look up a direct message channel.
The role_to_recipients map must also include an entry for "*", which the
plugin looks up if no other entry matches a given role name. In the example
above, requests for roles aside from dev and dba will notify the
admin-slack-channel channel.
Users can suggest reviewers when they create an Access Request, e.g.,:
tsh request create --roles=dbadmin [email protected],[email protected]
If an Access Request includes suggested reviewers, the Slack plugin will add these to the list of channels to notify. If a suggested reviewer is an email address, the plugin will look up the the direct message channel for that address and post a message in that channel.
Configure the Slack plugin to notify you when a user requests the editor role
by adding the following to your role_to_recipients config (replace
TELEPORT_USERNAME with the user you assigned the editor-reviewer role
earlier):
[role_to_recipients]
"*" = "access-requests"
"editor" = "TELEPORT_USERNAME"
roleToRecipients:
"*": "access-requests"
"editor": "TELEPORT_USERNAME"
Either create an access-requests channel in your Slack workspace or rename the
value of the "*" key to an existing channel.
Invite your Slack app
Once you have configured the channels that the Slack plugin will notify when it receives an Access Request, you will need to ensure that the plugin can post in those channels.
You have already configured the plugin to send direct messages as Slackbot. For
any other channel you mention in your role_to_recipients map, you will need
to invite the plugin to that channel. Navigate to each channel and enter /invite @teleport in the message box.
Step 7/8. Test your Slack app
Once Teleport is running, you've created the Slack app, and the plugin is configured, you can now run the plugin and test the workflow.
Start the plugin:
teleport-slack start
If everything works fine, the log output should look like this:
teleport-slack startINFO Starting Teleport Access Slack Plugin 7.2.1: slack/app.go:80INFO Plugin is ready slack/app.go:101
run the plugin:
docker run -v <path-to-config>:/etc/teleport-slack.toml public.ecr.aws/gravitational/teleport-plugin-slack:15.2.2 start
Install the plugin:
helm upgrade --install teleport-plugin-slack teleport/teleport-plugin-slack --values teleport-slack-helm.yaml
To inspect the plugin's logs, use the following command:
kubectl logs deploy/teleport-plugin-slack
Debug logs can be enabled by setting log.severity to DEBUG in
teleport-slack-helm.yaml and executing the helm upgrade ... command
above again. Then you can restart the plugin with the following command:
kubectl rollout restart deployment teleport-plugin-slack
Create an Access Request and check if the plugin works as expected with the following steps.
Create an Access Request
A Teleport admin can create an Access Request for another user with tctl:
tctl request create myuser --roles=editor
Users can use tsh to create an Access Request and log in with approved roles:
tsh request create --roles=editorSeeking request approval... (id: 8f77d2d1-2bbf-4031-a300-58926237a807)
Users can request access using the Web UI by visiting the "Access Requests" tab and clicking "New Request":
The user you configured earlier to review the request should receive a direct message from "Teleport" in Slack allowing them to visit a link in the Teleport Web UI and either approve or deny the request.
Resolve the request
Once you receive an Access Request message, click the link to visit Teleport and approve or deny the request:
You can also review an Access Request from the command line:
Replace REQUEST_ID with the id of the request
tctl request approve REQUEST_IDtctl request deny REQUEST_ID
Replace REQUEST_ID with the id of the request
tsh request review --approve REQUEST_IDtsh request review --deny REQUEST_ID
Once the request is resolved, the Slack bot will add an emoji reaction of ✅ or ❌ to the Slack message for the Access Request, depending on whether the request was approved or denied.
When the Slack plugin posts an Access Request notification to a channel, anyone with access to the channel can view the notification and follow the link. While users must be authorized via their Teleport roles to review Access Requests, you should still check the Teleport audit log to ensure that the right users are reviewing the right requests.
When auditing Access Request reviews, check for events with the type Access Request Reviewed in the Teleport Web UI.
Step 8/8. Set up systemd
This section is only relevant if you are running the Teleport Slack plugin on a Linux host.
In production, we recommend starting the Teleport plugin daemon via an init system like systemd. Here's the recommended Teleport plugin service unit file for systemd:
[Unit]
Description=Teleport Slack Plugin
After=network.target
[Service]
Type=simple
Restart=on-failure
ExecStart=/usr/local/bin/teleport-slack start --config=/etc/teleport-slack.toml
ExecReload=/bin/kill -HUP $MAINPID
PIDFile=/run/teleport-slack.pid
[Install]
WantedBy=multi-user.target
Save this as teleport-slack.service in either /usr/lib/systemd/system/ or
another unit file load
path
supported by systemd.
Enable and start the plugin:
sudo systemctl enable teleport-slacksudo systemctl start teleport-slack
Next steps
- Read our guides to configuring Resource Access Requests and Role Access Requests so you can get the most out of your Access Request plugins.